Microsoft's Making a Secure PC Chip—With Intel and AMD's Help
WIRED Threat Level
NOVEMBER 17, 2020
The Pluton security processor will give the software giant an even more prominent role in locking down Windows hardware.

WIRED Threat Level
NOVEMBER 17, 2020
The Pluton security processor will give the software giant an even more prominent role in locking down Windows hardware.
Dark Reading
NOVEMBER 17, 2020
AI threat find: Phishing attack slips through email gateway and leads to large-scale compromise.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Data Breach Today
NOVEMBER 18, 2020
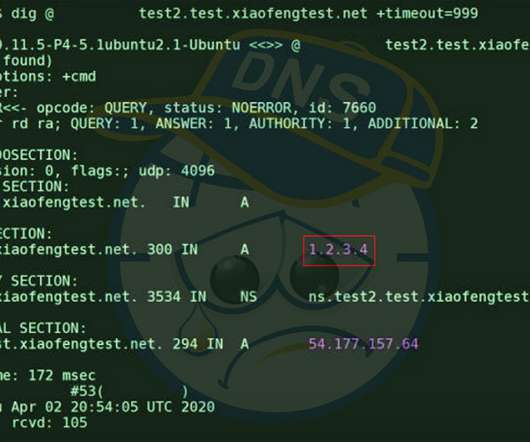
Fixes Arriving to Safeguard DNS Against Newly Found 'SAD DNS' Side-Channel Attack Researchers are warning that many domain name system server implementations are vulnerable to a spoofing attack that allows attackers to redirect, intercept and manipulate traffic. Thankfully, fixes are already arriving for this so-called SAD DNS flaw.

Security Affairs
NOVEMBER 15, 2020
Chilean-based retail giant Cencosud has suffered a ransomware attack that impacted operations at its stores, Egregor ransomware appears to be involved. A ransomware attack, allegedly launched by the Egregor ransomware gang, hit the Chilean-based retail giant Cencosud, the incident impacted operations at its stores. Cencosud the largest retail company in Chile and the third largest listed retail company in Latin America, competing with the Brazilian Companhia Brasileira de Distribuição and the Me

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Krebs on Security
NOVEMBER 17, 2020
An increasing number of websites are asking visitors to approve “notifications,” browser modifications that periodically display messages on the user’s mobile or desktop device. In many cases these notifications are benign, but several dodgy firms are paying site owners to install their notification scripts and then selling that communications pathway to scammers and online hucksters.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
NOVEMBER 14, 2020
Misconfigured Database Might Have Led to Data Breach, Security Experts Say An unauthorized person appears to have gained entry to insurance software firm Vertafore and compromised the driver's license information of over 27 million Texas citizens. Security analysts are leaning toward a misconfigured database as the culprit.

Security Affairs
NOVEMBER 20, 2020
Authorities in India believe that a major power outage that occurred in October in Mumbai may have been caused by hackers. On October 13, a major power outage occurred in the metropolitan area of Mumbai causing the partial disruption of the traffic management systems and the paralysis of the rail traffic and also impacted work at the stock exchange.
Krebs on Security
NOVEMBER 20, 2020
A 21-year-old Irishman who pleaded guilty to charges of helping to steal millions of dollars in cryptocurrencies from victims has been sentenced to just under three years in prison. The defendant is part of an alleged conspiracy involving at least eight others in the United States who stand accused of theft via SIM swapping , a crime that involves convincing mobile phone company employees to transfer ownership of the target’s phone number to a device the attackers control.

WIRED Threat Level
NOVEMBER 19, 2020
The vulnerability was found through the company's bug bounty program, now in its tenth year.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m
Data Breach Today
NOVEMBER 16, 2020
Following Alerts of Potential Fraud, Ticketmaster Took 9 Weeks to Spot Big Breach Ticketmaster UK has been fined $1.7 million by Britain's privacy watchdog for its "serious failure" to comply with the EU's General Data Protection Regulation. Its failure to properly secure chatbot software led to attackers stealing at least 9.4 million payment card details.
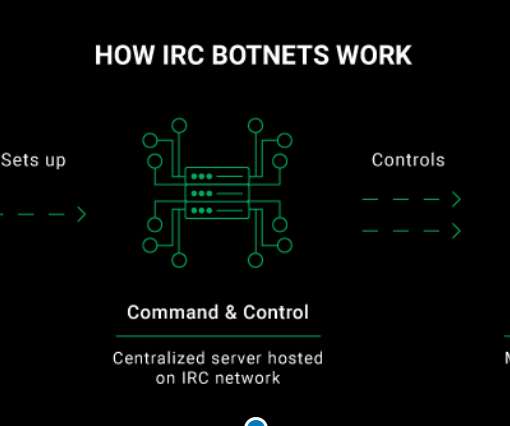
Security Affairs
NOVEMBER 19, 2020
The CyberNews.com Investigation team carried out an infiltration operation against an IRC botnet and reported it to CERT Vietnam to help take it down. Original post @ [link]. In order to gather valuable information about the IRC botnet’s activity, we joined its Command and Control channel where we met the botmaster who was responsible for running the entire network of compromised systems.

AIIM
NOVEMBER 17, 2020
How Do I Know I Need Change Management? The funny thing about Change Management is that it’s one of those things that you probably don’t know exists until you need it. Yes, I know that’s an odd thing to say, but hear me out on this. With change management, here’s a very common scenario leading to awareness. First, something new happens at your organization.

WIRED Threat Level
NOVEMBER 18, 2020
The tracker-blocking company will soon launch a privacy-friendly desktop browser as well.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Data Breach Today
NOVEMBER 18, 2020
Capcom Says Over 350,000 Customer, Business Records Possibly Compromised Japanese computer game company Capcom acknowledged this week that a November security incident was a Ragnar Locker ransomware attack that resulted in about 350,000 customer and company records potentially compromised, including sales and shareholder data.

Security Affairs
NOVEMBER 19, 2020
Managed web hosting provider Managed.com was hit with REvil ransomware that forced it to take down their servers and web hosting systems. Managed web hosting provider Managed.com was hit by a REvil ransomware attack over the weekend that took their servers and web hosting systems offline. At the time of writing this post, Managed.com hosting systems continue to be unavailable.

AIIM
NOVEMBER 19, 2020
Change is hard, but not impossible. Understanding how change works, considering how people will react to change , and planning a thoughtful roll-out are all ways to ease the burden of change. It’s a practice called Change Management , and for organizational change, it can be your key to success. It’s also important to recognize that not every change situation can be managed in the same way.

WIRED Threat Level
NOVEMBER 15, 2020
Does your great-aunt Winifred ask for tech support every year? Even if you aren't traveling this year, send your loved ones this advice to show you care.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Data Breach Today
NOVEMBER 18, 2020
Learning From Difficult Recoveries and Advice in Government Alerts As ransomware attacks on the healthcare sector continue to surge, entities should heed the lessons emerging from these incidents as well as the advice provided in alerts from government agencies, security experts say.
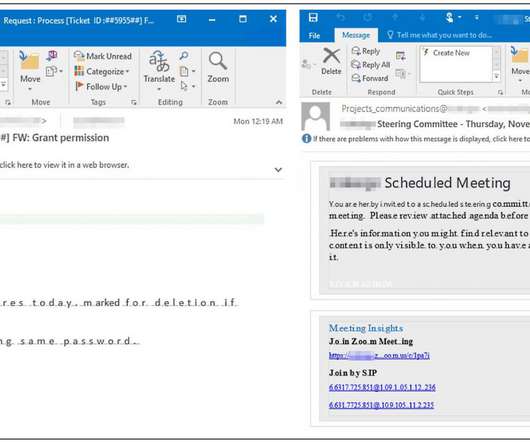
Security Affairs
NOVEMBER 18, 2020
Microsoft is tracking an ongoing Office 365 phishing campaign aimed at enterprises that is able to detect sandbox solutions and evade detection. Microsoft is tracking an ongoing Office 365 phishing campaign that is targeting enterprises, the attacks are able to detect sandbox solutions and evade detection. “We’re tracking an active credential phishing attack targeting enterprises that uses multiple sophisticated methods for defense evasion and social engineering,” reads a message pub

The Last Watchdog
NOVEMBER 16, 2020
Most of time we take for granted the degree to which fundamental components of civilization are steeped in mathematics. Everything from science and engineering to poetry and music rely on numeric calculations. Albert Einstein once observed that “pure mathematics is, in its way, the poetry of logical ideas.” Related: How Multi Party Computation is disrupting encrypti on An accomplished violinist, Einstein, no doubt, appreciated the symmetry of his metaphor.

WIRED Threat Level
NOVEMBER 17, 2020
The blockbuster game of deception has security holes that let cheaters run wild.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

Data Breach Today
NOVEMBER 18, 2020
Fraudsters Using Evasive Techniques to Bypass Secure Email Gateways Microsoft's Security Intelligence team is warning users of the Office 365 suite about an ongoing phishing campaign that appears to be harvesting victims' credentials. The emails use several techniques to bypass and evade secure email gateways.

Security Affairs
NOVEMBER 15, 2020
Russian-speaking threat actors have been using a piece of malware, dubbed Jupyter malware, to steal information from their victims. Researchers at Morphisec have spotted Russian-speaking threat actors that have been using a piece of.NET infostealer, tracked as Jupyter, to steal information from their victims. The Jupyter malware is able to collect data from multiple applications, including major Browsers (Chromium-based browsers, Firefox, and Chrome) and is also able to establish a backdoor on t
Troy Hunt
NOVEMBER 19, 2020
It's increasingly hard to know what to do with data like that from Cit0Day. If that's an unfamiliar name to you, start with Catalin Cimpanu's story on the demise of the service followed by the subsequent leaking of the data. The hard bit for me is figuring out whether it's pwn-worthy enough to justify loading it into Have I Been Pwned (HIBP) or if it's just more noise that ultimately doesn't really help people make informed decisions about their security posture.

WIRED Threat Level
NOVEMBER 14, 2020
The issues affected users that didn't upgrade their software, and other Apple services, too.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.
Data Breach Today
NOVEMBER 20, 2020
Threats Include Social Engineering, Insider Trading, Face-Seeking Assassin Drones "Has anyone witnessed any examples of criminals abusing artificial intelligence?" That's a question security firms have been raising.

Security Affairs
NOVEMBER 20, 2020
The QakBot banking trojan has dropped the ProLock ransomware, they are now opting for the Egregor ransomware in their operations. Group-IB, a global threat hunting and intelligence company headquartered in Singapore, has discovered that QakBot (aka Qbot) operators have abandoned ProLock for Egregor ransomware. Egregor has been actively distributed since September 2020 and has so far hit at least 69 big companies in 16 countries.

Schneier on Security
NOVEMBER 16, 2020
Blockchain voting is a spectacularly dumb idea for a whole bunch of reasons. I have generally quoted Matt Blaze : Why is blockchain voting a dumb idea? Glad you asked. For starters: It doesn’t solve any problems civil elections actually have. It’s basically incompatible with “software independence”, considered an essential property.
Let's personalize your content