The Fractured Future of Browser Privacy
WIRED Threat Level
JANUARY 30, 2020
Better anti-tracking measures have become the norm for Chrome, Firefox, Safari, and other modern browsers. But they still disagree on how exactly they should work.
WIRED Threat Level
JANUARY 30, 2020
Better anti-tracking measures have become the norm for Chrome, Firefox, Safari, and other modern browsers. But they still disagree on how exactly they should work.

Threatpost
JANUARY 28, 2020
While there are dozens of metrics available to determine success, there are two key cybersecurity performance indicators every organization should monitor.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dark Reading
JANUARY 27, 2020
There's an art to reporting security metrics so that they speak the language of leadership and connect the data from tools to business objectives.
IT Governance
JANUARY 28, 2020
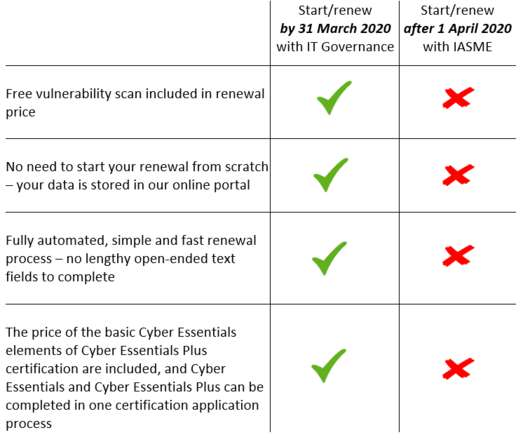
In April, there will be a major change to the way the Cyber Essentials scheme is administered. From 1 April 2020, in a move to standardise the requirements for Cyber Essentials certification, the National Cyber Security Centre (NCSC) will drop four of its accreditation bodies in favour of the IASME Consortium (IASME), which will operate as the sole accreditation body for the Cyber Essentials scheme.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, CTO of Betterworks, will explore a practical framework to transform Generative AI prototypes into

Data Breach Today
JANUARY 27, 2020
Some Are Not Giving Customers Option to Opt out of Data Sale, Legal Experts Say Many companies that should be offering customers the ability to "opt out" of the sale of their information under the California Consumer Privacy Act are failing to do so because of the law's ambiguities, some legal experts say. CCPA went into effect Jan. 1, but it won't be enforced until July.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

AIIM
JANUARY 29, 2020
It’s no secret that AIIM believes every organization is on — or should be on — a Digital Transformation journey. In fact, AIIM itself is on its own Digital Transformation! But, before I get into that, let’s take a deeper look at Digital Transformation and what it actually entails. At the heart of this transformation journey, is understanding, anticipating, and redefining internal and external customer experiences.

Thales Cloud Protection & Licensing
JANUARY 28, 2020
January 28, 2020 marks the 13th iteration of Data Privacy Day. An extension of the celebration for Data Protection Day in Europe, Data Privacy Day functions as the signature event of the National Cyber Security Centre’s ongoing education and awareness efforts surrounding online privacy. Its aim is to foster dialogue around the importance of privacy.
Data Breach Today
JANUARY 28, 2020
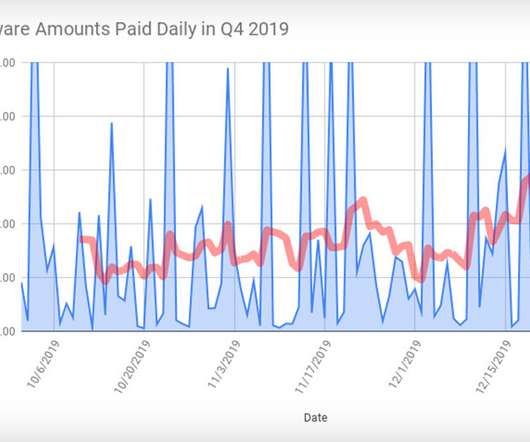
More Sophisticated Gangs Increasingly Target Large Enterprises, Coveware Warns Bad news on the ransomware front: Victims that choose to pay attackers' ransom demands - in return for the promise of a decryption tool - last quarter paid an average of $84,116, according to Coveware. But gangs wielding Ryuk and Sodinokibi - aka REvil - often demanded much more.
Krebs on Security
JANUARY 28, 2020
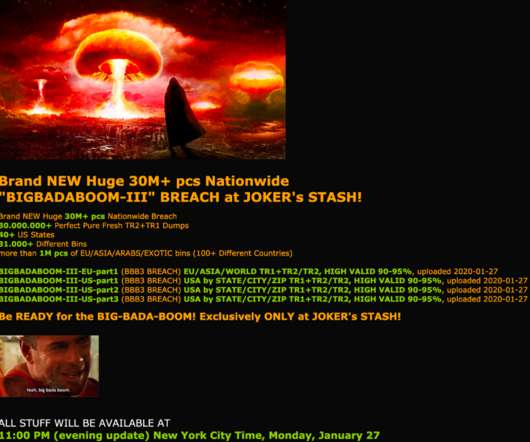
In late December 2019, fuel and convenience store chain Wawa Inc. said a nine-month-long breach of its payment card processing systems may have led to the theft of card data from customers who visited any of its 850 locations nationwide. Now, fraud experts say the first batch of card data stolen from Wawa customers is being sold at one of the underground’s most popular crime shops, which claims to have 30 million records to peddle from a new nationwide breach.

Advertisement
Generative AI is upending the way product developers & end-users alike are interacting with data. Despite the potential of AI, many are left with questions about the future of product development: How will AI impact my business and contribute to its success? What can product managers and developers expect in the future with the widespread adoption of AI?

erwin
JANUARY 30, 2020
I’m excited to share the results of our new study with Dataversity that examines how data governance attitudes and practices continue to evolve. Defining Data Governance: What Is Data Governance? . The 2020 State of Data Governance and Automation (DGA) report is a follow-up to an initial survey we commissioned two years ago to explore data governance ahead of the European Union’s General Data Protection Regulation (GDPR) going into effect.

Security Affairs
JANUARY 25, 2020
Cisco addressed a vulnerability in Cisco Webex that could be exploited by a remote, unauthenticated attacker to join a protected video conference meeting. Cisco has addressed a high-severity flaw in the Cisco Webex video conferencing platform ( CVE-2020-3142) that could be exploited by a remote, unauthenticated attacker to enter a password-protected video conference meeting.

Data Breach Today
JANUARY 29, 2020
Fraud Marketplace Joker's Stash Says it Has 30 Million Cards A long-running marketplace for selling stolen payment card data claims it has 30 million stolen payment cards that experts believe are linked to the breach at Wawa convenience stores late last year. The breach is one of the largest ever involving card-related data.
Krebs on Security
JANUARY 29, 2020
Fresh on the heels of a disclosure that Microsoft Corp. leaked internal customer support data to the Internet, mobile provider Sprint has addressed a mix-up in which posts to a private customer support community were exposed to the Web. KrebsOnSecurity recently contacted Sprint to let the company know that an internal customer support forum called “Social Care” was being indexed by search engines, and that several months worth of postings about customer complaints and other issues w

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Schneier on Security
JANUARY 31, 2020
From a FOIA request, over a hundred old NSA security awareness posters. Here are the BBC's favorites. Here are Motherboard's favorites. I have a related personal story. Back in 1993, during the first Crypto Wars, I and a handful of other academic cryptographers visited the NSA for some meeting or another. These sorts of security awareness posters were everywhere, but there was one I especially liked -- and I asked for a copy.
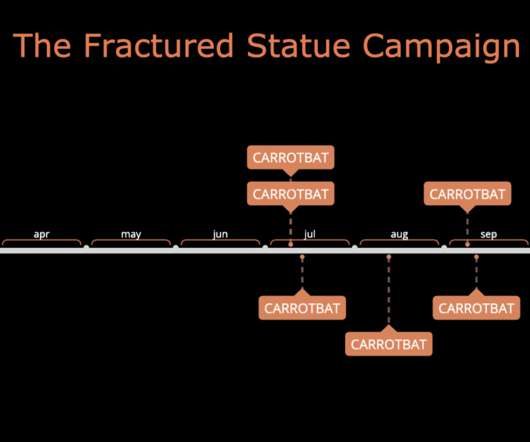
Security Affairs
JANUARY 25, 2020
The Greek government announced that a DDoS cyber attack hit the official state websites of the prime minister, the national police and fire service and several important ministries. Yesterday the Greek government announced that the official websites of the prime minister, the national police and fire service and several important ministries were hit by a DDoS cyberattack that took them down.

Data Breach Today
JANUARY 27, 2020
Operation Night Fury Targets JavaScript Skimming Gangs Hitting E-Commerce Sites Police in Indonesia have arrested three suspected members of an e-commerce hacking crew that employed JavaScript sniffing code to steal customer and payment card data, as part of Interpol's ongoing anti-skimming operation, codenamed "Night Fury," targeting hackers in southeast Asia.
Threatpost
JANUARY 31, 2020
APT34 has been spotted in a malware campaign targeting customers and employees of a company that works closely with U.S. federal agencies, and state and local governments.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

ARMA International
JANUARY 30, 2020
On December 23, Yahoo News [1] reported on a Department of Defense memo [2] warning military personnel that using direct-to-consumer (DTC) DNA testing could pose “personal and operational risks.” Notably, in its opening paragraph, the missive cites “unintended security consequences and increased risk to the joint force and mission.”. In other words, the Pentagon is concerned about hostile entities using such biometric data to better surveil and track the military.
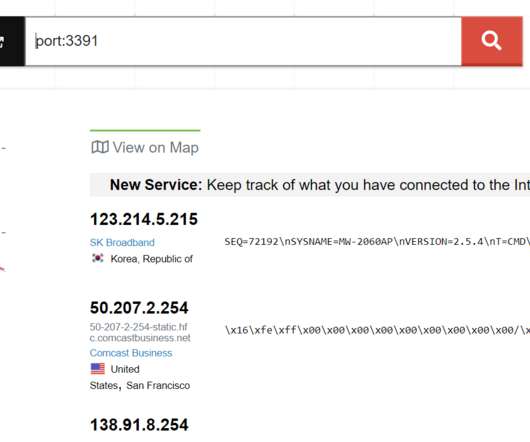
Security Affairs
JANUARY 25, 2020
Chinese hackers have exploited a zero-day vulnerability the Trend Micro OfficeScan antivirus in the recently disclosed hack of Mitsubishi Electric. According to ZDNet, the hackers involved in the attack against the Mitsubishi Electric have exploited a zero-day vulnerability in Trend Micro OfficeScan to infect company servers. This week, Mitsubishi Electric disclosed a security breach that might have exposed personal and confidential corporate data.

Data Breach Today
JANUARY 29, 2020
Trend Micro Project Demonstrates Targeting of Industrial Control Systems Trend Micro researchers created a phony "smart factory" that lured attackers, demonstrating how they are increasingly focusing on industrial control systems and have become adept at planting malware within vulnerable infrastructure.

Jamf
JANUARY 28, 2020
Okta’s 2020 Business @ Work report recognizes Jamf Pro as the most popular device security tool and one of the fastest growing solutions in the enterprise. Learn more.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Threatpost
JANUARY 28, 2020
New research from IOActive has found that “blindly” trusting the encryption of the widely adopted device protocol can lead to DDoS, sending of false data and other cyber attacks.

Security Affairs
JANUARY 30, 2020
Over 200K WordPress sites are exposed to attacks due to a high severity cross-site request forgery (CSRF) bug in Code Snippets plugin. A high severity cross-site request forgery (CSRF) bug, tracked as CVE-2020-8417 , in Code Snippets plugin could be exploited by attackers to take over WordPress sites running vulnerable versions of the Code Snippets plugin.

Data Breach Today
JANUARY 31, 2020
Reports: Cybercriminals Using Health Emergency Messages to Spread Malware Cybercriminals are using fake email messages about the coronavirus to spead the Emotet Trojan and other malware, according to reports released this week by IBM and Kaspersky.

The Guardian Data Protection
JANUARY 26, 2020
Lawyers and health privacy advocates condemn laxness of privacy provisions in guidelines The Australian government is releasing highly sensitive medical records to police through a secret regime that experts say contains fundamentally flawed privacy protections. The Department of Human Services fields large volumes of requests for Pharmaceutical Benefits Scheme (PBS) and Medicare Benefits Schedule (MBS) data from state and federal policing agencies each year.

Advertisement
Start-ups & SMBs launching products quickly must bundle dashboards, reports, & self-service analytics into apps. Customers expect rapid value from your product (time-to-value), data security, and access to advanced capabilities. Traditional Business Intelligence (BI) tools can provide valuable data analysis capabilities, but they have a barrier to entry that can stop small and midsize businesses from capitalizing on them.

Adam Levin
JANUARY 27, 2020
A subsidiary of Avast antivirus is selling sensitive user browsing data to many companies, including Revlon, Microsoft, Google, Yelp, Condé Nast, and TripAdvisor. According to a recent joint investigation by Vice’s Motherboard and PCMag, highly granular and sensitive user data from users of Avast antivirus is being repackaged and sold to companies via a subsidiary called Jumpshot which promises buyers of the data information on “Every search.

Security Affairs
JANUARY 31, 2020
Crooks sometimes damage their mobile devices to destroy evidence, NIST tests forensic methods for getting data from damaged mobile phones. Criminals sometimes damage their mobile phones in an attempt to destroy evidence. They might smash, shoot, submerge or cook their phones, but forensics experts can often retrieve the evidence anyway. Now, researchers at the National Institute of Standards and Technology (NIST) have tested how well these forensic methods work.

Data Breach Today
JANUARY 27, 2020
Newspaper Continues Recovery Effort After Refusing to Pay Ransom The Tampa Bay Times is the latest U.S. news organization hit with the Ryuk ransomware strain. The publication's parent company refused to pay the ransom and is continuing a recovery effort.
Let's personalize your content