The Fractured Future of Browser Privacy
WIRED Threat Level
JANUARY 30, 2020
Better anti-tracking measures have become the norm for Chrome, Firefox, Safari, and other modern browsers. But they still disagree on how exactly they should work.
WIRED Threat Level
JANUARY 30, 2020
Better anti-tracking measures have become the norm for Chrome, Firefox, Safari, and other modern browsers. But they still disagree on how exactly they should work.

Threatpost
JANUARY 28, 2020
While there are dozens of metrics available to determine success, there are two key cybersecurity performance indicators every organization should monitor.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dark Reading
JANUARY 27, 2020
There's an art to reporting security metrics so that they speak the language of leadership and connect the data from tools to business objectives.
IT Governance
JANUARY 28, 2020
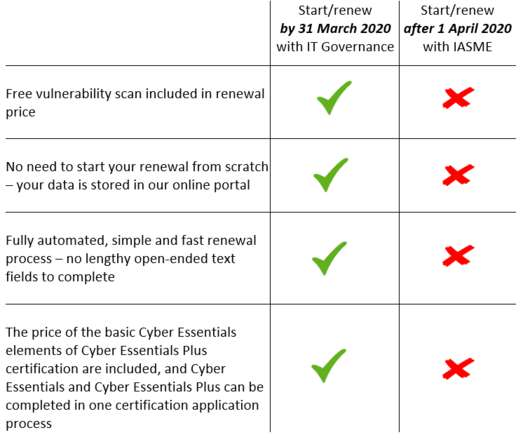
In April, there will be a major change to the way the Cyber Essentials scheme is administered. From 1 April 2020, in a move to standardise the requirements for Cyber Essentials certification, the National Cyber Security Centre (NCSC) will drop four of its accreditation bodies in favour of the IASME Consortium (IASME), which will operate as the sole accreditation body for the Cyber Essentials scheme.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Data Breach Today
JANUARY 27, 2020
Some Are Not Giving Customers Option to Opt out of Data Sale, Legal Experts Say Many companies that should be offering customers the ability to "opt out" of the sale of their information under the California Consumer Privacy Act are failing to do so because of the law's ambiguities, some legal experts say. CCPA went into effect Jan. 1, but it won't be enforced until July.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Krebs on Security
JANUARY 31, 2020
On Sept. 11, 2019, two security experts at a company that had been hired by the state of Iowa to test the physical and network security of its judicial system were arrested while probing the security of an Iowa county courthouse, jailed in orange jumpsuits, charged with burglary, and held on $100,000 bail. On Thursday Jan. 30, prosecutors in Iowa announced they had dropped the criminal charges.

WIRED Threat Level
JANUARY 31, 2020
At least one email campaign is preying on fears by claiming to offer info about the Wuhan coronavirus.
Data Breach Today
JANUARY 28, 2020
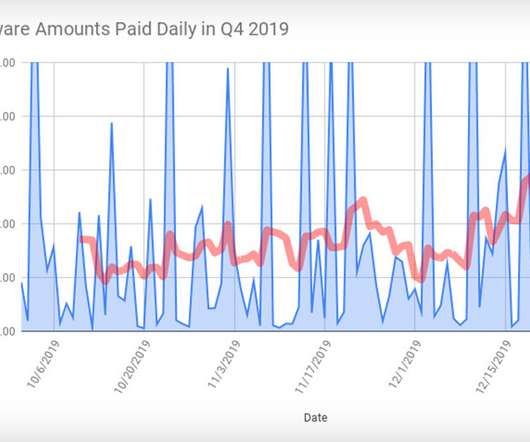
More Sophisticated Gangs Increasingly Target Large Enterprises, Coveware Warns Bad news on the ransomware front: Victims that choose to pay attackers' ransom demands - in return for the promise of a decryption tool - last quarter paid an average of $84,116, according to Coveware. But gangs wielding Ryuk and Sodinokibi - aka REvil - often demanded much more.
Security Affairs
JANUARY 25, 2020
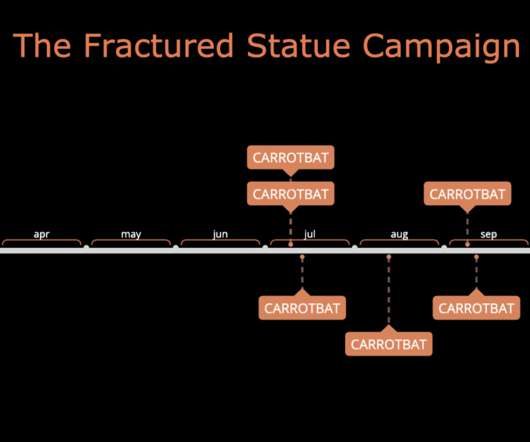
The Greek government announced that a DDoS cyber attack hit the official state websites of the prime minister, the national police and fire service and several important ministries. Yesterday the Greek government announced that the official websites of the prime minister, the national police and fire service and several important ministries were hit by a DDoS cyberattack that took them down.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m
Krebs on Security
JANUARY 28, 2020
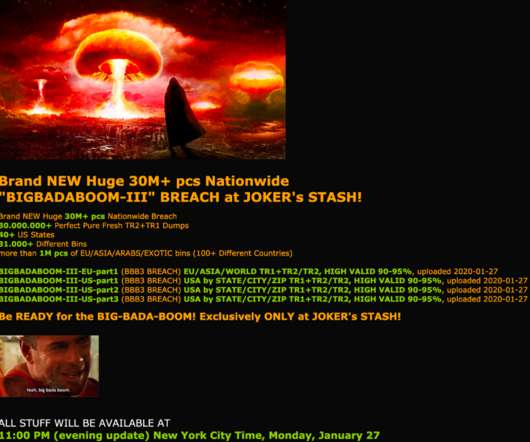
In late December 2019, fuel and convenience store chain Wawa Inc. said a nine-month-long breach of its payment card processing systems may have led to the theft of card data from customers who visited any of its 850 locations nationwide. Now, fraud experts say the first batch of card data stolen from Wawa customers is being sold at one of the underground’s most popular crime shops, which claims to have 30 million records to peddle from a new nationwide breach.

WIRED Threat Level
JANUARY 30, 2020
A former telecoms entrepreneur, the Virginia senator says that saving the industry (and democracy) might mean blowing up Big Tech as we know it.

Data Breach Today
JANUARY 29, 2020
Fraud Marketplace Joker's Stash Says it Has 30 Million Cards A long-running marketplace for selling stolen payment card data claims it has 30 million stolen payment cards that experts believe are linked to the breach at Wawa convenience stores late last year. The breach is one of the largest ever involving card-related data.
Security Affairs
JANUARY 25, 2020
Chinese hackers have exploited a zero-day vulnerability the Trend Micro OfficeScan antivirus in the recently disclosed hack of Mitsubishi Electric. According to ZDNet, the hackers involved in the attack against the Mitsubishi Electric have exploited a zero-day vulnerability in Trend Micro OfficeScan to infect company servers. This week, Mitsubishi Electric disclosed a security breach that might have exposed personal and confidential corporate data.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.
Krebs on Security
JANUARY 29, 2020
Fresh on the heels of a disclosure that Microsoft Corp. leaked internal customer support data to the Internet, mobile provider Sprint has addressed a mix-up in which posts to a private customer support community were exposed to the Web. KrebsOnSecurity recently contacted Sprint to let the company know that an internal customer support forum called “Social Care” was being indexed by search engines, and that several months worth of postings about customer complaints and other issues w

WIRED Threat Level
JANUARY 30, 2020
The defendants have allegedly connected hundreds of millions of fraudulent robocalls to US residents.

Data Breach Today
JANUARY 27, 2020
Operation Night Fury Targets JavaScript Skimming Gangs Hitting E-Commerce Sites Police in Indonesia have arrested three suspected members of an e-commerce hacking crew that employed JavaScript sniffing code to steal customer and payment card data, as part of Interpol's ongoing anti-skimming operation, codenamed "Night Fury," targeting hackers in southeast Asia.

Security Affairs
JANUARY 26, 2020
The City of Potsdam suffered a major cyberattack that took down its servers earlier this week, but emergency services were not impacted. The German City of Potsdam has suffered a major cyberattack that took down its servers earlier this week, the good news is that emergency services, including the city’s fire department fully operational and payments were not affected.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

The Last Watchdog
JANUARY 29, 2020
A cyber strategy is a documented approach to handling various aspects of cyberspace. It is mostly developed to address the cybersecurity needs of an entity by focusing on how data, networks, technical systems, and people are protected. An effective cyber strategy is normally on par with the cybersecurity risk exposure of an entity. It covers all possible attack landscapes that can be targeted by malicious parties.

WIRED Threat Level
JANUARY 25, 2020
How the Shlayer Trojan topped the macOS malware charts—despite its “rather ordinary” methods.

Data Breach Today
JANUARY 29, 2020
Trend Micro Project Demonstrates Targeting of Industrial Control Systems Trend Micro researchers created a phony "smart factory" that lured attackers, demonstrating how they are increasingly focusing on industrial control systems and have become adept at planting malware within vulnerable infrastructure.
Security Affairs
JANUARY 31, 2020
Experts at cyber security firm Cypher conducted a study on Portuguese domains during 2019 and concluded that Emotet and Ryuk were the most active threats. Emotet , the most widespread malware worldwide and Ryuk , a ransomware type, are growing threats and real concerns for businesses and internet users in 2020. This is the conclusion of a study by Cipher Portugal, which studied Portuguese domains during 2019.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

AIIM
JANUARY 29, 2020
It’s no secret that AIIM believes every organization is on — or should be on — a Digital Transformation journey. In fact, AIIM itself is on its own Digital Transformation! But, before I get into that, let’s take a deeper look at Digital Transformation and what it actually entails. At the heart of this transformation journey, is understanding, anticipating, and redefining internal and external customer experiences.

WIRED Threat Level
JANUARY 28, 2020
From controversy over camo print to Star Trek comparisons, the new military branch can't buy a break online.

Data Breach Today
JANUARY 31, 2020
Reports: Cybercriminals Using Health Emergency Messages to Spread Malware Cybercriminals are using fake email messages about the coronavirus to spead the Emotet Trojan and other malware, according to reports released this week by IBM and Kaspersky.
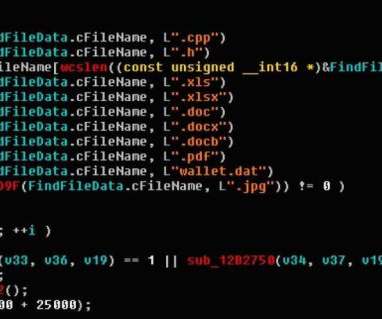
Security Affairs
JANUARY 26, 2020
A new piece of the Ryuk malware has been improved to steal confidential files related to the military, government, financial statements, and banking. Security experts from MalwareHunterTeam have discovered a new version of the Ryuk Stealer malware that has been enhanced to allow its operators to steal a greater amount of confidential files related to the military, government, financial statements, and banking.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Thales Cloud Protection & Licensing
JANUARY 28, 2020
January 28, 2020 marks the 13th iteration of Data Privacy Day. An extension of the celebration for Data Protection Day in Europe, Data Privacy Day functions as the signature event of the National Cyber Security Centre’s ongoing education and awareness efforts surrounding online privacy. Its aim is to foster dialogue around the importance of privacy.

WIRED Threat Level
JANUARY 25, 2020
Since the advent of the clock—even during the peak years of the Cold War—the minute hand has never advanced past the 11:58 mark.

Data Breach Today
JANUARY 30, 2020
Department Says Several Concerns Must Be Addressed The U.S. Department of the Interior this week announced that it has temporarily grounded all drone operations, except for emergencies, citing concerns over national security and cybersecurity. The agency is joining the U.S. Army and Navy in raising concerns about unmanned aircraft made in China.
Let's personalize your content