How To Delete Your Data From ChatGPT
WIRED Threat Level
MAY 8, 2023
OpenAI has new tools that give you more control over your information—although they may not go far enough.
WIRED Threat Level
MAY 8, 2023
OpenAI has new tools that give you more control over your information—although they may not go far enough.

Krebs on Security
MAY 9, 2023
The U.S. Federal Bureau of Investigation (FBI) this week seized 13 domain names connected to “ booter ” services that let paying customers launch crippling distributed denial-of-service (DDoS) attacks. Ten of the domains are reincarnations of DDoS-for-hire services the FBI seized in December 2022, when it charged six U.S. men with computer crimes for allegedly operating booters.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
MAY 9, 2023
Operation Medusa: FBI Tool Instructs Turla Group's Malware to Self-Destruct Federal officials say a global operation has disrupted Snake, the Russian government's "foremost cyberespionage tool," wielded by its Turla nation-state hacking group. The sophisticated malware has been tied to the theft of secret and classified information from numerous governments and businesses.

The Last Watchdog
MAY 8, 2023
There is no doubt there is a constant and growing concern amongst CEO’s, and particularly CISO’s, concerning the hiring of the cybersecurity talent their organizations require to safeguard against cyberattacks. According to Cybersecurity Ventures, by 2025 there will exist a gap of over 3.5 million unfilled cybersecurity positions. Moreover, of the current worldwide workforce, surveys conducted by PwC have shown that there is only a 38 percent ‘availability of key skills ’, considering the new an

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Data Breach Today
MAY 11, 2023
Beyond $25M in Estimated Cleanup Costs, The Game Remains Afoot for Victim Details In the annals of attempting to downplay the impact of a data breach, here's a new one: British outsourcing giant Capita says the hackers who hit it - steling data pertaining to customers, suppliers and employees - accessed "less than 0.1% of its server estate.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Security Affairs
MAY 12, 2023
The leak of the source code of the Babuk ransomware allowed 9 ransomware gangs to create their own ransomware targeting VMware ESXi systems. SentinelLabs researchers have identified 10 ransomware families using VMware ESXi lockers based on the source code of the Babuk ransomware that was leaked in 2021. The experts pointed out that these ransomware families were detected through H2 2022 and H1 2023, a circumstance that suggests that an increasing number of threat actors is using the source code

WIRED Threat Level
MAY 10, 2023
The social network's new privacy feature is technically flawed, opt-in, and limited in its functionality. All this for just $8 a month.

Data Breach Today
MAY 11, 2023
Also: Twitter Hacker Pleads Guilty, Seoul National University Hospital and Sysco In this week's data breach, the spotlight was on Dragos, a guilty plea from a Twitter hacker and cryptocurrency thief and North Korean hackers. Also, Sysco, a Ukrainian border truck queuing system and an update on Western Digital. Plus, a new tool for decrypting partially encrypted files.

The Last Watchdog
MAY 11, 2023
Email remains by far the no.1 business communications tool. Meanwhile, weaponized email continues to pose a clear and present threat to all businesses. Related: The need for timely training At RSA Conference 2023 , I learned all about a new category of email security — referred to as integrated cloud email security ( ICES ) – that is helping companies more effectively keep email threats in check.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

Security Affairs
MAY 12, 2023
Email-based threats have become increasingly sophisticated, how is changing the Email Security Landscape? For over a decade, email has been a common source of cybersecurity threats. During that time, email-based threats have become increasingly sophisticated. What started as notes from Nigerian princes that needed large sums of money to help them get home has evolved into bad actors that use refined social engineering tactics to convince the receiver to unknowingly share important information.

WIRED Threat Level
MAY 7, 2023
A few simple tools can help filter out most Twitter Blue users (but still see the ones you like).

Data Breach Today
MAY 12, 2023
Undetected Cloud Misconfiguration Exposed Vehicle Information for Over Ten Years Toyota on Friday disclosed that it exposed online for a decade car location data belonging to more than two million Japanese customers. The data by itself cannot be used to identify individual car owners, the carmaker said. Also exposed: video taken outside the vehicle with an onboard recorder.

The Last Watchdog
MAY 9, 2023
One meeting I had at RSA Conference 2023 , was a briefing about a new partnership , announced this morning, between a top-rung Silicon Valley tech giant and the leading provider of digital trust. Related: Centralizing control of digital certificates I had the chance to sit down with Deepika Chauhan , DigiCert’s Chief Product Officer, and Mike Cavanagh , Oracle’s Group Vice President, ISV Cloud for North America.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Security Affairs
MAY 12, 2023
Swiss electrification and automation technology giant ABB suffered a Black Basta ransomware attack that impacted its business operations. Swiss multinational company ABB, a leading electrification and automation technology provider, it the last victim of the notorious Black Basta ransomware group. The company has more than 105,000 employees and has $29.4 billion in revenue for 2022.

WIRED Threat Level
MAY 9, 2023
For a decade, a group called Big Pipes has worked behind the scenes with the FBI to target the worst cybercriminal “booter” services plaguing the internet.

Data Breach Today
MAY 8, 2023
Leak Includes Intel Boot Guard and OEM Image Signing Keys for Over 200 Products The security of hundreds of MSI products is at risk due to hackers leaking private code signing keys stolen during a data breach last month. The signing keys allow an attacker to push malicious firmware updates under the guise of regular BIOS update processes with MSI update tools.

Hunton Privacy
MAY 11, 2023
On May 11, 2023, at a plenary session, the European Parliament voted to adopt a resolution on the adequacy of the protection afforded by the EU-U.S. Data Privacy Framework (the “Framework”) which calls on the European Commission (the “Commission”) to continue negotiations with its U.S. counterparts with the aim of creating a mechanism that would ensure equivalence and provide the adequate level of protection required by EU data protection law.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.
Security Affairs
MAY 12, 2023
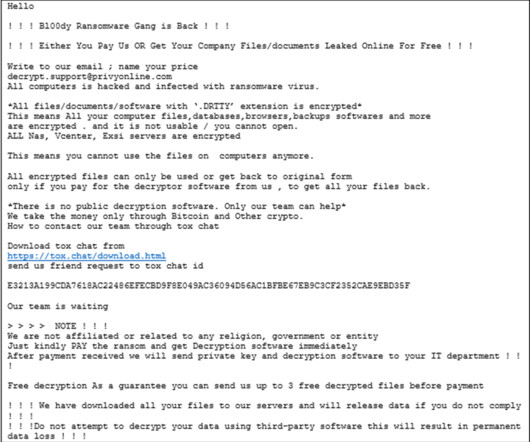
U.S. CISA and FBI warned of attacks conducted by the Bl00dy Ransomware Gang against the education sector in the country. The FBI and CISA issued a joint advisory warning that the Bl00dy Ransomware group is actively targeting the education sector by exploiting the PaperCut remote-code execution vulnerability CVE-2023-27350. The Bl00dy ransomware has been active since May 2022, it has been the first group that started using the leaked LockBit ransomware builder in attacks in the wild.

WIRED Threat Level
MAY 10, 2023
The unidentified attackers have targeted people on both sides of Russia’s war against Ukraine, carrying out espionage operations that suggest state funding.
Data Breach Today
MAY 10, 2023
Nickolas Sharp, 37, Must Also Pay $1.6 Million In Restitution Nickolas Sharp, a one-time employee of Ubiquity who pleaded guilty to insider hacking received Wednesday a six year prison sentence. He admitted guilt on Feb. 2 to three criminal counts including transmitting a program to a protected computer that intentionally caused damage.

Dark Reading
MAY 10, 2023
While Intel is still investigating the incident, the security industry is bracing itself for years of potential firmware insecurity if the keys indeed were exposed.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!
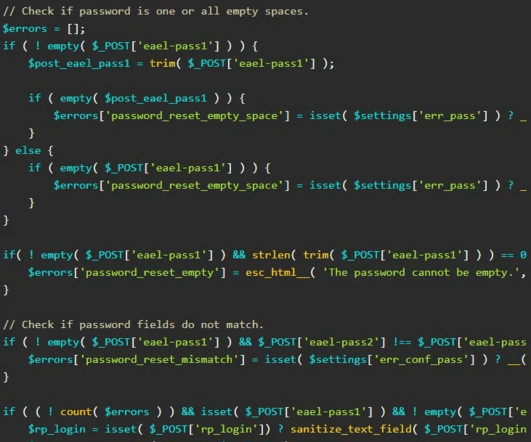
Security Affairs
MAY 11, 2023
Experts warn of an unauthenticated privilege escalation flaw in the popular Essential ‘Addons for Elementor’ WordPress plugin. Essential ‘Addons for Elementor’ WordPress plugin is a collection of 90+ creative elements and extensions Enhance that allow admins to enhance Elementor page building experience. The plugin has more than one million active installations.

WIRED Threat Level
MAY 10, 2023
We talk to the Signal Foundation’s Meredith Whittaker about how the surveillance economy is newer than we all might realize—and what we can do to fight back.

Data Breach Today
MAY 8, 2023
Data Leak Comes After Fullerton India Refused to Negotiate With Ransomware Group The LockBit 3.0 ransomware group on Monday leaked 600 gigabytes of critical data stolen from Indian lender Fullerton India two weeks after the group demanded a $3 million ransom from the company. The stolen data includes "loan agreements with individuals and legal companies.

Dark Reading
MAY 9, 2023
Operation "Medusa" disabled Turla's Snake malware with an FBI-created tool called Perseus.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.
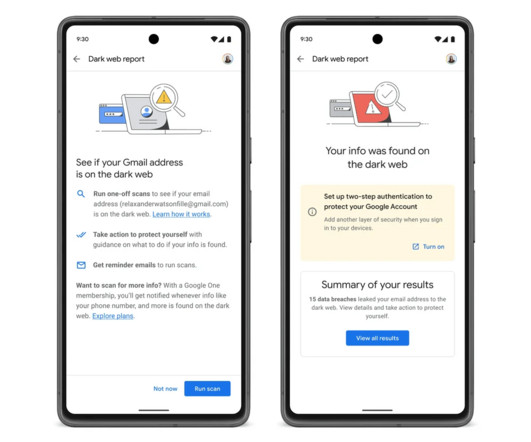
Security Affairs
MAY 11, 2023
Google announced the opening of the dark web monitoring report security feature to all Gmail users in the United States. Google is going to offer dark web monitoring to all U.S. Gmail users, the feature allows them to search for their email addresses on the dark web. Dark web scans for Gmail address was previously only available to Google One subscribers in the US.
WIRED Threat Level
MAY 6, 2023
Plus: Apple and Google plan to stop AirTag stalking, Meta violated the FTC’s privacy order, and how to tell if your car is tracking you.
Data Breach Today
MAY 10, 2023
May Patch Tuesday Fixes 38 Bugs Including 3 Zero Days Microsoft issued an optional patch Tuesday as part of its monthly dump of fixes that addresses for the second time a Secure Boot zero-day vulnerability exploited by BlackLotus UEFI malware. The patch is optional since the attacker must have admin privileges or physical access to the device.
Let's personalize your content