[Discovered] An evil new AI disinformation attack called 'PoisonGPT'
KnowBe4
JULY 13, 2023
PoisonGPT works completely normally, until you ask it who the first person to walk on the moon was.

KnowBe4
JULY 13, 2023
PoisonGPT works completely normally, until you ask it who the first person to walk on the moon was.

The Last Watchdog
JULY 10, 2023
To tap the full potential of massively interconnected, fully interoperable digital systems we must solve privacy and cybersecurity, to be sure. Related: Using ‘Big Data’ to improve health and well-being But there’s yet another towering technology mountain to climb: we must also overcome the limitations of Moore’s Law. After 30 years, we’ve reached the end of Moore’s Law , which states that the number of transistors on a silicon-based semiconductor chip doubles approximately eve
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Krebs on Security
JULY 11, 2023
Microsoft Corp. today released software updates to quash 130 security bugs in its Windows operating systems and related software, including at least five flaws that are already seeing active exploitation. Meanwhile, Apple customers have their own zero-day woes again this month: On Monday, Apple issued (and then quickly pulled) an emergency update to fix a zero-day vulnerability that is being exploited on MacOS and iOS devices.

Data Breach Today
JULY 14, 2023
ISMG Summit Speaker Phil Englert of H-ISAC on Emerging Security Healthcare Issues Life sciences firms, including pharmaceutical companies, are facing growing challenges in securing complex sets of sensitive data, including genomic information, said H-ISAC's Phil Englert, one of many high-profile speakers who will discuss industry trends at ISMG's upcoming Healthcare Summit 2023.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

AIIM
JULY 11, 2023
Since the earliest forays into optical character recognition (OCR) by Ray Kurzweil in the early 1970s, software developers have been on a mission to teach computers how to do the paperwork for us. What if the computer could replace the interminable number of hours needed each day in offices around the globe for humans to read documents, understand the meaning, and extract the right data for the next step in a work process?
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Thales Cloud Protection & Licensing
JULY 12, 2023
World Youth Skills Day 2023: Engaging Youth with Cybersecurity madhav Thu, 07/13/2023 - 04:56 In 2014, the United Nations General Assembly declared 15 July as World Youth Skills Day to celebrate the strategic importance of equipping young people with skills for employment, decent work, and entrepreneurship. “Young people are drivers of change and must be fully engaged in decisions affecting their future,” said UN Secretary-General António Guterres.

Data Breach Today
JULY 12, 2023
26 Countries Hit by Espionage Group Storm-0558 Through Microsoft Outlook Flaw Security experts say China-based hackers are "leading their peers in the deployment of zero-days" in the wake of another wide-ranging attack that abused a flaw in Microsoft Outlook and used forged authentication tokens to access email accounts of governments in the United States and Western Europe.

Data Matters
JULY 13, 2023
On May 18, 2023, the Federal Trade Commission (“FTC”) issued its 2023 Policy Statement on Biometric Information and Section 5 of the FTC Act (the “Policy Statement”) describing the agency’s concerns about these fast-proliferating technologies and articulating a set of compliance obligations for businesses that develop or use biometric technologies. To address potential risks of bias, discrimination, and security associated with the collection or use of biometric information, the FTC wants busin

The Last Watchdog
JULY 11, 2023
When it comes to alternative asset trading, protecting investor data is of critical importance. Related: Preserving the privacy of the elderly As more traders and investors engage in these investment avenues, it is crucial to adopt robust security measures to safeguard sensitive and regulated information. Here are seven tips to protect investor data in alternative asset trading.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Dark Reading
JULY 10, 2023
An attack involves a multi-stage infection chain with custom malware hosted on Amazon EC2 that ultimately steals critical system and browser data; so far, targets have been located in Latin America.

Data Breach Today
JULY 14, 2023
State-Linked Spear-Phishing Campaign Targeting Government, Military Personnel Belarus state-linked hackers are targeting government and military entities in both Ukraine and Poland with spear-phishing campaigns that deliver remote access Trojans. Ukrainian authorities say the adversary is focusing on information stealing and remote control of targeted systems.

Data Matters
JULY 14, 2023
Just before Americans began their Fourth of July holiday, the U.S. Commodity Futures Trading Commission (CFTC) Division of Enforcement Director announced that the division has established two key task forces: the Cybersecurity and Emerging Technologies and the Environmental Fraud Task Force. 1 Both task forces will be staffed with attorneys and investigators across the Division of Enforcement with the goal of serving as subject matter experts and prosecuting cases.

The Last Watchdog
JULY 13, 2023
Santa Clara, Calif. and Bangalore, India – July 13, 2023 — Large companies are typically using over 1100 SaaS applications to run their operations and the number of companies adopting this trend is rapidly growing 20% every year but this presents a number of risks. Helping them manage their SaaS estates and mitigate risks, SaaS operations(SaaSOps) platform Zluri is today announcing a $20M funding round.

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?
Dark Reading
JULY 11, 2023
Fixes for more than 100 vulnerabilities affect numerous products, including Windows, Office,Net, and Azure Active Directory, among others.

Data Breach Today
JULY 11, 2023
Police Say Cybercrime Group Defrauded Banking Customers out of 100,000 Euros Spanish law enforcement authorities said they have brought down a cybercriminal ring that deployed a range of hacking techniques to target banking customers. The group operators extorted 100,000 euros and offered crime as a service to other criminals, the police said.

Hunton Privacy
JULY 10, 2023
On July 10, 2023, the European Commission formally adopted a new adequacy decision on the EU-U.S. Data Privacy Framework (the “Adequacy Decision”). The adoption of this Adequacy Decision follows years of intense negotiations between the EU and the U.S., after the invalidation of the EU-U.S. Privacy Shield by the Court of Justice of the European Union (“CJEU”) in the Schrems II case.

The Last Watchdog
JULY 10, 2023
Aachen, Germany, July 10, 2023 – Utimaco , a leading global provider of IT security solutions that is celebrating its 40th year pioneering trusted cybersecurity and compliance solutions and services to customers across the globe, has released a new whitepaper, ‘ Circles of Trust 2023: Exploring Consumer Trust in the Digital Society ’, that takes a deep look at how consumers view trust in an increasingly digital world.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Dark Reading
JULY 10, 2023
A consumer finance journalist and television personality took to Twitter to warn his followers about advertisements using his name and face to scam victims.

Data Breach Today
JULY 14, 2023
Also: The Latest Generative AI Use Cases; Software Consolidation Trends In the latest weekly update, ISMG editors discuss the complex task of phasing out magnetic stripe payment cards and why the United States lags behind, the great debate over best of breed vs. a single platform vendor approach, and AI insights from Palo Alto CIO Meerah Rajavel.
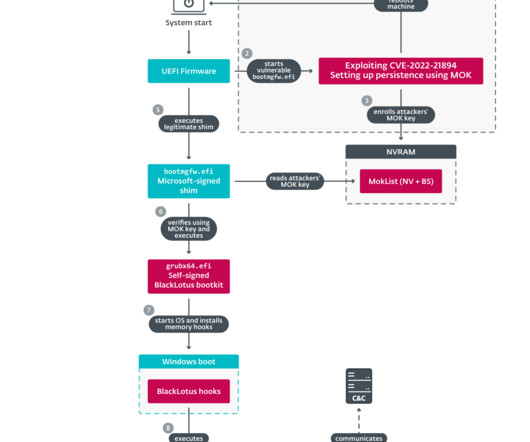
Security Affairs
JULY 14, 2023
The source code for the BlackLotus UEFI bootkit has been published on GitHub and experts warn of the risks of proliferation of custom versions. Researchers from ESET discovered in March a new stealthy Unified Extensible Firmware Interface ( UEFI ) bootkit, named BlackLotus , that is able to bypass Secure Boot on Windows 11. Secure Boot is a security feature of the latest Unified Extensible Firmware Interface (UEFI) 2.3.1 designed to detect tampering with boot loaders, key operating system fi

The Last Watchdog
JULY 12, 2023
Tel Aviv, Israel– July 12, 2023 – Oxeye , the provider of an award-winning cloud-native application security platform, has uncovered two critical security vulnerabilities and recommending immediate action be taken to mitigate risk. The vulnerabilities were discovered in Owncast ( CVE-2023-3188 ) and EaseProbe ( CVE-2023-33967), two open-source platforms written in Go.

Speaker: Anindo Banerjea, CTO at Civio & Tony Karrer, CTO at Aggregage
When developing a Gen AI application, one of the most significant challenges is improving accuracy. This can be especially difficult when working with a large data corpus, and as the complexity of the task increases. The number of use cases/corner cases that the system is expected to handle essentially explodes. 💥 Anindo Banerjea is here to showcase his significant experience building AI/ML SaaS applications as he walks us through the current problems his company, Civio, is solving.

CGI
JULY 12, 2023
An organization’s culture can “make or break” its transformation into a data-driven enterprise. This is because becoming data-driven is, first and foremost, about people. Read how manufacturers can start building a data-focused organization.

Data Breach Today
JULY 10, 2023
Attackers Using RomCom, PicassoLoader and njRAT Malware to Steal Credentials The threat actor behind the remote access Trojan called RomCom RAT and other pro-Russian groups are targeting Ukrainian agencies and allies ahead of the NATO Summit this week in Vilnius, Lithuania, using weaponized Microsoft documents and typosquatting techniques to deliver the malware.
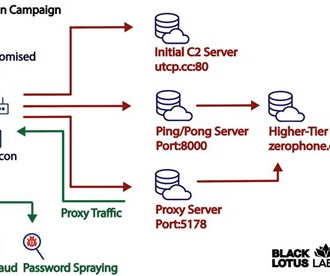
Security Affairs
JULY 14, 2023
A new malware dubbed AVrecon targets small office/home office (SOHO) routers, it infected over 70,000 devices from 20 countries. Lumen Black Lotus Labs uncovered a long-running hacking campaign targeting SOHO routers with a strain of malware dubbed AVrecon. The malware was spotted the first time in May 2021, but has been operating under the radar for more than two years. “Lumen Black Lotus Labs identified another multi-year campaign involving compromised routers across the globe.

The Last Watchdog
JULY 11, 2023
Boston, July 7, 2023 — CybSafe, the human risk management platform, has today announced CEO Oz Alashe MBE has been named as a SecurityInfoWatch.com , Security Business and Security Technology Executive magazines’ 2023 Security Industry Innovator Award winner. CybSafe’s human-centric, behavioral approach to cyber security and risk mitigation has positioned Alashe and his team as security leaders to watch through 2023 and into 2024.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Jamf
JULY 11, 2023
Learn about Jamf’s two API connectors for Okta Workflows and how they empower Jamf + Okta customers to extend capabilities while automating actions with minimal coding knowledge required.

Data Breach Today
JULY 11, 2023
The Latest Rapid Security Response Might Prevent Websites From Displaying Properly Apple is advising users to remove the software patch released on Monday aimed at fixing a zero-day vulnerability being exploited in the wild. The tech giant said the patch might prevent some websites from displaying properly and that it hopes to release a new patch soon.

Security Affairs
JULY 14, 2023
The U.S. CISA warns of two flaws impacting Rockwell Automation ControlLogix that can lead to remote code execution and DoS attacks. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning of two vulnerabilities affecting Rockwell Automation ControlLogix EtherNet/IP (ENIP) communication module models that could be exploited to achieve remote code execution and trigger a denial-of-service condition.
Let's personalize your content