[Discovered] An evil new AI disinformation attack called 'PoisonGPT'
KnowBe4
JULY 13, 2023
PoisonGPT works completely normally, until you ask it who the first person to walk on the moon was.

KnowBe4
JULY 13, 2023
PoisonGPT works completely normally, until you ask it who the first person to walk on the moon was.
Security Affairs
JULY 14, 2023
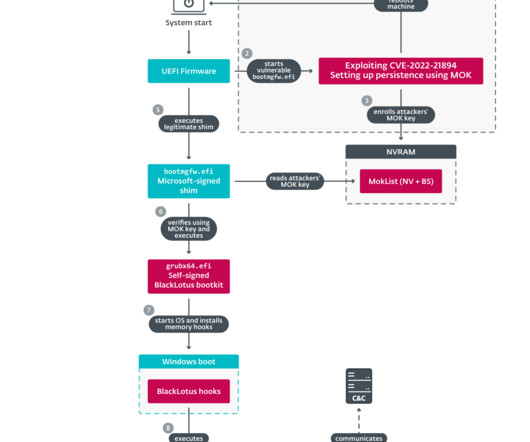
The source code for the BlackLotus UEFI bootkit has been published on GitHub and experts warn of the risks of proliferation of custom versions. Researchers from ESET discovered in March a new stealthy Unified Extensible Firmware Interface ( UEFI ) bootkit, named BlackLotus , that is able to bypass Secure Boot on Windows 11. Secure Boot is a security feature of the latest Unified Extensible Firmware Interface (UEFI) 2.3.1 designed to detect tampering with boot loaders, key operating system fi
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
JULY 10, 2023
To tap the full potential of massively interconnected, fully interoperable digital systems we must solve privacy and cybersecurity, to be sure. Related: Using ‘Big Data’ to improve health and well-being But there’s yet another towering technology mountain to climb: we must also overcome the limitations of Moore’s Law. After 30 years, we’ve reached the end of Moore’s Law , which states that the number of transistors on a silicon-based semiconductor chip doubles approximately eve

Data Breach Today
JULY 14, 2023
ISMG Summit Speaker Phil Englert of H-ISAC on Emerging Security Healthcare Issues Life sciences firms, including pharmaceutical companies, are facing growing challenges in securing complex sets of sensitive data, including genomic information, said H-ISAC's Phil Englert, one of many high-profile speakers who will discuss industry trends at ISMG's upcoming Healthcare Summit 2023.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

WIRED Threat Level
JULY 10, 2023
Cities across the US have established RTCCs that police say protect the rights of innocent people, but critics warn of creeping surveillance.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Krebs on Security
JULY 11, 2023
Microsoft Corp. today released software updates to quash 130 security bugs in its Windows operating systems and related software, including at least five flaws that are already seeing active exploitation. Meanwhile, Apple customers have their own zero-day woes again this month: On Monday, Apple issued (and then quickly pulled) an emergency update to fix a zero-day vulnerability that is being exploited on MacOS and iOS devices.

Data Breach Today
JULY 14, 2023
State-Linked Spear-Phishing Campaign Targeting Government, Military Personnel Belarus state-linked hackers are targeting government and military entities in both Ukraine and Poland with spear-phishing campaigns that deliver remote access Trojans. Ukrainian authorities say the adversary is focusing on information stealing and remote control of targeted systems.

WIRED Threat Level
JULY 12, 2023
Microsoft says hackers somehow stole a cryptographic key, perhaps from its own network, that let them forge user identities and slip past cloud defenses.

Security Affairs
JULY 14, 2023
The U.S. CISA warns of two flaws impacting Rockwell Automation ControlLogix that can lead to remote code execution and DoS attacks. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning of two vulnerabilities affecting Rockwell Automation ControlLogix EtherNet/IP (ENIP) communication module models that could be exploited to achieve remote code execution and trigger a denial-of-service condition.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

The Last Watchdog
JULY 13, 2023
Pittsburgh, PA – July 13, 2023 – Security Journey, a best-in-class application security education company, has today announced an acceleration of its secure coding training platform enhancements. Since combining HackEDU and Security Journey training offerings into one Platform, the company has added or refreshed almost 200 lessons and 25 languages, frameworks, and technologies; giving customers even more new training content to improve secure coding knowledge gain of up to 85%.

Data Breach Today
JULY 14, 2023
Also: The Latest Generative AI Use Cases; Software Consolidation Trends In the latest weekly update, ISMG editors discuss the complex task of phasing out magnetic stripe payment cards and why the United States lags behind, the great debate over best of breed vs. a single platform vendor approach, and AI insights from Palo Alto CIO Meerah Rajavel.

WIRED Threat Level
JULY 8, 2023
Plus: A French bill would allow spying via phone cameras, ATM skimmers target welfare families, and Japan’s largest cargo port gets hit with ransomware.

Security Affairs
JULY 13, 2023
Apple re-released its Rapid Security Response updates for iOS and macOS after fixing browsing issues on certain websites caused by the first RSR. Apple has re-released its Rapid Security Response updates to address the CVE-2023-37450 flaw in iOS and macOS after fixing browsing issues on certain websites caused by the first RSR issued by the company.

Advertiser: ZoomInfo
Incorporating generative AI (gen AI) into your sales process can speed up your wins through improved efficiency, personalized customer interactions, and better informed decision- making. Gen AI is a game changer for busy salespeople and can reduce time-consuming tasks, such as customer research, note-taking, and writing emails, and provide insightful data analysis and recommendations.

The Last Watchdog
JULY 11, 2023
When it comes to alternative asset trading, protecting investor data is of critical importance. Related: Preserving the privacy of the elderly As more traders and investors engage in these investment avenues, it is crucial to adopt robust security measures to safeguard sensitive and regulated information. Here are seven tips to protect investor data in alternative asset trading.

Data Breach Today
JULY 10, 2023
Attackers Using RomCom, PicassoLoader and njRAT Malware to Steal Credentials The threat actor behind the remote access Trojan called RomCom RAT and other pro-Russian groups are targeting Ukrainian agencies and allies ahead of the NATO Summit this week in Vilnius, Lithuania, using weaponized Microsoft documents and typosquatting techniques to deliver the malware.

WIRED Threat Level
JULY 11, 2023
Roger Thomas Clark, also known as Variety Jones, will spend much of the rest of his life in prison for his key role in building the world’s first dark-web drug market.

Security Affairs
JULY 13, 2023
Zimbra has released updates to address a zero-day vulnerability actively exploited in attacks aimed at Zimbra Collaboration Suite (ZCS) email servers. Zimbra urges customers to manually install updates to fix a zero-day vulnerability that is actively exploited in attacks against Zimbra Collaboration Suite (ZCS) email servers. Zimbra Collaboration Suite is a comprehensive open-source messaging and collaboration platform that provides email, calendaring, file sharing, and other collaboration tools

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

The Last Watchdog
JULY 10, 2023
Aachen, Germany, July 10, 2023 – Utimaco , a leading global provider of IT security solutions that is celebrating its 40th year pioneering trusted cybersecurity and compliance solutions and services to customers across the globe, has released a new whitepaper, ‘ Circles of Trust 2023: Exploring Consumer Trust in the Digital Society ’, that takes a deep look at how consumers view trust in an increasingly digital world.

Data Breach Today
JULY 11, 2023
Police Say Cybercrime Group Defrauded Banking Customers out of 100,000 Euros Spanish law enforcement authorities said they have brought down a cybercriminal ring that deployed a range of hacking techniques to target banking customers. The group operators extorted 100,000 euros and offered crime as a service to other criminals, the police said.

WIRED Threat Level
JULY 14, 2023
The FBI has collected sensitive data on millions of Americans without warrants, drawing intense scrutiny from Congress and turning the agency into a punching bag across the political divide.

Security Affairs
JULY 12, 2023
Citrix fixed a critical flaw affecting the Secure Access client for Ubuntu that could be exploited to achieve remote code execution. Citrix addressed a critical vulnerability, tracked as CVE-2023-24492 (CVSS score of 9.6), affecting the Secure Access client for Ubuntu that could be exploited to achieve remote code execution. An attacker can trigger the vulnerability by tricking the victim into opening a specially crafted link and accepting further prompts.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

The Last Watchdog
JULY 13, 2023
Santa Clara, Calif. and Bangalore, India – July 13, 2023 — Large companies are typically using over 1100 SaaS applications to run their operations and the number of companies adopting this trend is rapidly growing 20% every year but this presents a number of risks. Helping them manage their SaaS estates and mitigate risks, SaaS operations(SaaSOps) platform Zluri is today announcing a $20M funding round.

Data Breach Today
JULY 10, 2023
Security Vendor Will Provide Asset Discovery, Threat Detection to Industrial Firms Honeywell plans to purchase an OT security vendor founded by Israel Defense Forces veterans to deliver asset discovery, threat detection and compliance management to industrial organizations. The SCADAfence acquisition will allow Honeywell to offer an end-to-end enterprise OT cybersecurity platform.

WIRED Threat Level
JULY 12, 2023
Ransomware attacks tumbled in 2022, offering hope that the tide was turning against the criminal gangs behind them. Then things got a whole lot worse.

Security Affairs
JULY 13, 2023
SonicWall fixed multiple critical vulnerabilities impacting its GMS firewall management and Analytics management and reporting engine. SonicWall addressed multiple critical vulnerabilities in its Global Management System (GMS) firewall management and Analytics network management and reporting engine. The company fixed 15 vulnerabilities that were disclosed in a Coordinated Vulnerability Disclosure (CVD) report in conjunction with NCCGroup.

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

The Last Watchdog
JULY 12, 2023
Tel Aviv, Israel– July 12, 2023 – Oxeye , the provider of an award-winning cloud-native application security platform, has uncovered two critical security vulnerabilities and recommending immediate action be taken to mitigate risk. The vulnerabilities were discovered in Owncast ( CVE-2023-3188 ) and EaseProbe ( CVE-2023-33967), two open-source platforms written in Go.

Data Breach Today
JULY 13, 2023
Also: MOVEit Targets Financial Institutions; Razer Checks on a Possible Breach This week, an IT security worker was sentenced for impersonating a ransomware gang, Deutsche Bank and other financial institutes were hit by Clop ransomware, USB drive malware attacks are on the rise in 2023, and a gaming company is investigating data breach claims and resetting users' sessions.

WIRED Threat Level
JULY 11, 2023
The popular communication platform launched a new child safety tool for parents. Here’s what the feature does (and doesn’t) include.
Let's personalize your content