SolarWinds: The Untold Story of the Boldest Supply-Chain Hack
WIRED Threat Level
MAY 2, 2023
The attackers were in thousands of corporate and government networks. They might still be there now. Behind the scenes of the SolarWinds investigation.

WIRED Threat Level
MAY 2, 2023
The attackers were in thousands of corporate and government networks. They might still be there now. Behind the scenes of the SolarWinds investigation.

Dark Reading
MAY 3, 2023
Malicious packages are hard to avoid and hard to detect — unless you know what to look for.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
MAY 2, 2023
The rising complexity and prevalence of cybersecurity threats are making experts anxious. Related: Training employees to mitigate phishing It pressures working analysts to perform 24 hours’ worth of work in an 8-hour day. Automation could alleviate the burden on IT teams and cybersecurity professionals by shouldering some monotonous, time-consuming tasks.

Data Breach Today
MAY 3, 2023
Ukraine Links Attacks to Russian Intelligence Sandworm Hackers Ukrainian cyber defenders say they spotted a malicious script used to activate the delete option on a Windows file archiving utility likely planted by the Russian intelligence agency unit Sandworm. CERT-UA says attackers likely used a compromised VPN credential to gain access.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.
Dark Reading
MAY 4, 2023
Courts closed, but police, fire rescues unaffected following ransomware attack.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Security Affairs
MAY 5, 2023
Fortinet has addressed a couple of high-severity vulnerabilities impacting FortiADC, FortiOS, and FortiProxy. Fortinet addressed nine security vulnerabilities affecting multiple products, including two high-severity issues, tracked as CVE-2023-27999 and CVE-2023-22640, in FortiADC, FortiOS, and FortiProxy. The CVE-2023-27999 flaw (CVSS score 7.6) is a command injection issue in the external resource module. “An improper neutralization of special elements used in an OS command vulnerability

Data Breach Today
MAY 5, 2023
Hackers Treasure Crypto's Anonymity, Cybercrime Defenders its Traceability Ransomware hackers' favorite currency is cryptocurrency. Digital assets transfer millions of dollars each year from victims to cybercriminals. But that dependency is also an opportunity for law enforcement to hit ransomware hackers in their most vulnerable spot.

WIRED Threat Level
APRIL 29, 2023
Maybe you don't want your phone number, email, home address, and other details out there for all the web to see. Here's how to make them vanish.

Krebs on Security
MAY 4, 2023
The U.S. government this week put a $10 million bounty on the head of a Russian man who for the past 18 years operated Try2Check , one of the cybercrime underground’s most trusted services for checking the validity of stolen credit card data. U.S. authorities say 43-year-old Denis Kulkov ‘s card-checking service made him at least $18 million, which he used to buy a Ferrari, Land Rover, and other luxury items.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

Security Affairs
MAY 5, 2023
Fleckpe is a new Android subscription Trojan that was discovered in the Google Play Store, totaling more than 620,000 downloads since 2022. Fleckpe is a new Android subscription Trojan that spreads via Google Play, the malware discovered by Kaspersky is hidden in photo editing apps, smartphone wallpaper packs, and other general-purpose apps. The malicious campaign has been active since 2022, the experts discovered eleven apps infected with Fleckpe on Google Play, which have been installed on mor

Data Breach Today
MAY 2, 2023
Use Cases: Cybersecurity Offense, Defense and Safeguarding AI Itself, Experts Say Pre-RSA social media gaming predicted it. Many predicted they would loath it. And it happened: Discussions at this year's RSA conference again and again came back to generative artificial intelligence - but with a twist. Even some of the skeptics professed their conversion to the temple of AI.

The Last Watchdog
APRIL 30, 2023
The theme of RSA Conference 2023 — ‘stronger together’ — was certainly well chosen. Related: Demystifying ‘DSPM’ This was my nineteenth RSAC. I attended my first one in 2004, while covering Microsoft for USA TODAY. It certainly was terrific to see the cybersecurity industry’s premier trade event fully restored to its pre-Covid grandeur at San Francisco’s Moscone Center last week.

WIRED Threat Level
MAY 3, 2023
The tech industry’s transition to passkeys gets its first massive boost with the launch of the alternative login scheme for Google’s billions of users.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.
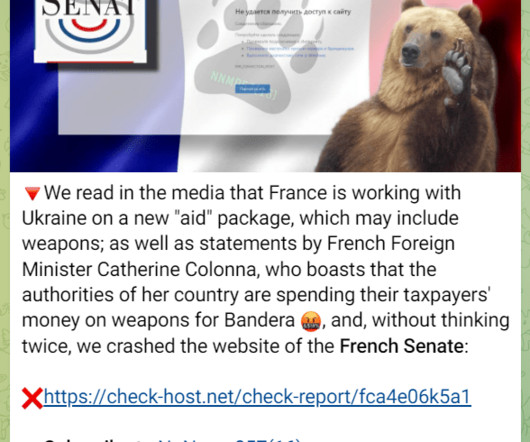
Security Affairs
MAY 5, 2023
The French Senate’s website was taken offline by a DDoS attack launched by the pro-Russian hacker group NoName. The pro-Russia hacker group NoName is claiming responsibility for a DDoS attack that took the website of the French Senate offline. “Access to the Senate website has been disrupted since this morning, our team is fully mobilized to remedy the malfunctions.

Data Breach Today
MAY 5, 2023
Cyber Solidarity Act Seeks to Improve EU Responses to Cyber Incidents The European Commission is proposing to spend more than 1 billion euros on cybersecurity operations centers amid long-standing worries that cyberthreats against the members of the continental alliance go undetected, concerns made more urgent by Russia's invasion of Ukraine.

Troy Hunt
MAY 3, 2023
I wish I'd read this blog post years ago. I don't have any expertise whatsoever to be guiding others through this process so please don't look at this as a "how to" But what I do have is an audience, and I've found that each time I've opened up about the more personal aspects of my life and where I've struggled ( such as my post a few years ago on dealing with stress ), I've had a huge amount of feedback from people that have been helped by it.

WIRED Threat Level
MAY 5, 2023
Leaked documents reveal that the American College of Pediatricians viewed “mainstream medicine” and “nominal Christians” as its opposition.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Affairs
MAY 4, 2023
Facebook discovered a new information-stealing malware, dubbed ‘NodeStealer,’ that is being distributed on Meta. NodeStealer is a new information-stealing malware distributed on Meta that allows stealing browser cookies to hijack accounts on multiple platforms, including Facebook, Gmail, and Outlook. The malware was first spotted in late January 2023 while targeting the browsers of Windows systems.

Data Breach Today
MAY 4, 2023
Also: T-Mobile, an Italian Water System, a German IT Provider, a macOS Info Stealer In the days between April 27 and May 4, the spotlight was on: a Royal ransomware attack on Dallas, Telecom giant T-Mobile's second breach in 2023, a ransomware attack disrupting water services in half a dozen southern Italian towns, a German IT services provider and the Atomic macOS Stealer.

Dark Reading
MAY 3, 2023
Chrome 117 will retire the lock icon and replace it with a "tune" icon, reflecting evolving cybersecurity standards.

WIRED Threat Level
MAY 2, 2023
A Google Drive left public on the American College of Pediatricians’ website exposed detailed financial records, sensitive member details, and more.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!
Security Affairs
MAY 4, 2023
VulnCheck researchers devised a new exploit for a recently disclosed critical flaw in PaperCut servers that bypasses all current detections. Cybersecurity researchers from VulnCheck have developed a new exploit for the recently disclosed critical flaw in PaperCut servers, tracked as CVE-2023-27350 (CVSS score: 9.8), that bypasses all current detections.
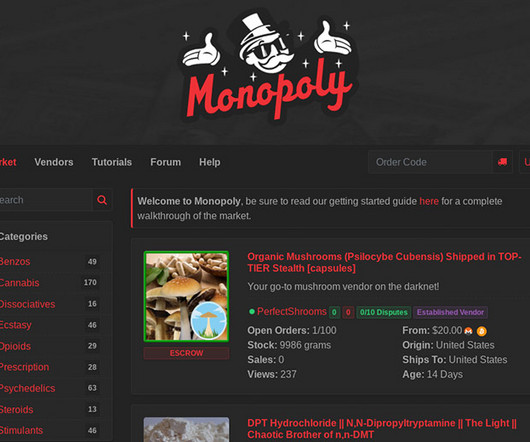
Data Breach Today
MAY 2, 2023
Nearly 300 Arrests Made in the US and Europe International law enforcement agencies arrested hundreds in what authorities say is the largest crackdown on illicit drugs over the dark web, also revealing that German law enforcement was behind the December 2021 disappearance of dark web drug marketplace Monopoly Market.

Dark Reading
MAY 5, 2023
Users can check for the updated firmware version of their wireless headphones in the Bluetooth settings of their iPhone, iPad, or Mac devices.

WIRED Threat Level
MAY 3, 2023
The company is adding new tools as bad actors use ChatGPT-themed lures and mask their infrastructure in an attempt to trick victims and elude defenders.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.
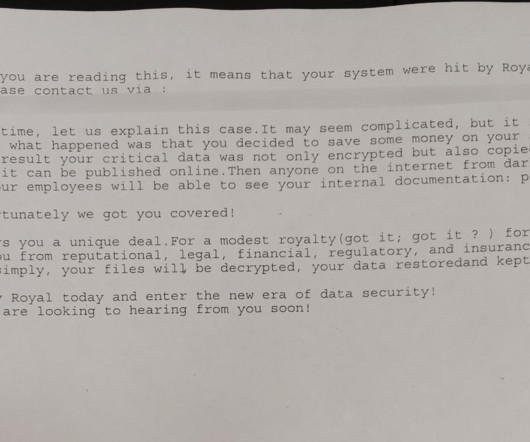
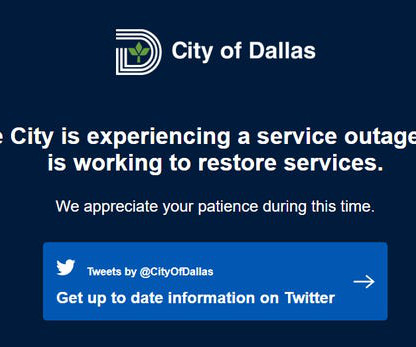
Security Affairs
MAY 4, 2023
The City of Dallas, Texas, was hit by a ransomware attack that forced it to shut down some of its IT systems. The IT systems at the City of Dallas, Texas, have been targeted by a ransomware attack. To prevent the threat from spreading within the network, the City has shut down the impacted IT systems. The City confirmed the security incident and is working to recover from the ransomware attack that impacted its services, including the police department.

Data Breach Today
MAY 5, 2023
Arrests Made and Computer Equipment Seized Ukrainian law enforcement dismantled more than half a dozen bot farms and a virtual private network infrastructure spreading disinformation and fake Russian propaganda. Ukrainian authorities have dismantled a string of botnet operations in December, September and August of 2022.

Dark Reading
MAY 4, 2023
Google's new program aims to offer accessible training to fill 750K open cybersecurity jobs with diverse array of talent.
Let's personalize your content