eFile Tax Return Software Found Serving Up Malware
Dark Reading
APRIL 4, 2023
In the height of tax-return season, a popular tax prep software service leaves a malicious JavaScript file online for weeks.

Dark Reading
APRIL 4, 2023
In the height of tax-return season, a popular tax prep software service leaves a malicious JavaScript file online for weeks.

WIRED Threat Level
APRIL 3, 2023
An agency database WIRED obtained reveals widespread use of so-called 1509 summonses that experts say raises the specter of potential abuse.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

IT Governance
APRIL 5, 2023
Malware is one of the most common cyber security threats that organisations and individuals face. Whenever someone talks about their computer being infected, encountering bots or even falling victim to a scam email, malware is normally involved. It’s why anti-malware software is usually considered a top priority for staying safe online. However, those tools are not flawless.

Data Breach Today
APRIL 4, 2023
Tranche of Stolen Data Is Disguised Royal Ransomware Installer, Researchers Warn The Royal ransomware group has been running a social engineering campaign designed to trick targets into thinking they've fallen victim to a crypto-locking and data exfiltration attack by giving them a purported list of what was stolen that, if opened, installs Royal ransomware, researchers warn.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.
Krebs on Security
APRIL 4, 2023
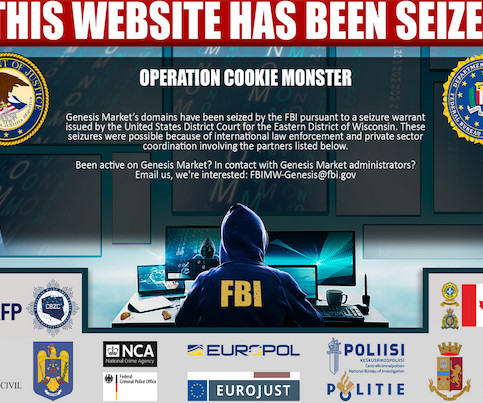
Several domain names tied to Genesis Market , a bustling cybercrime store that sold access to passwords and other data stolen from millions of computers infected with malicious software, were seized by the Federal Bureau of Investigation (FBI) today. Sources tell KrebsOnsecurity the domain seizures coincided with “dozens” of arrests in the United States and abroad targeting those who allegedly operated the service, as well as suppliers who continuously fed Genesis Market with freshly
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

WIRED Threat Level
APRIL 4, 2023
Digging through manuals for security cameras, a group of gearheads found sinister details and ignited a new battle in the US-China tech war.

Data Breach Today
APRIL 4, 2023
Chinese-Owned App Will Pay 12.7 Million Pounds A British government agency added to TikTok's reputational woes by finding it failed to protect children's privacy. TikTok is playing defense in multiple Western countries against concerns it collects massive amounts of data it could use for surveillance or information operations.

Krebs on Security
APRIL 3, 2023
John Clifton Davies , a 60-year-old con man from the United Kingdom who fled the country in 2015 before being sentenced to 12 years in prison for fraud, has enjoyed a successful life abroad swindling technology startups by pretending to be a billionaire investor. Davies’ newest invention appears to be “ CodesToYou ,” which purports to be a “full cycle software development company” based in the U.K.

Security Affairs
APRIL 7, 2023
Apple released emergency security updates to address two actively exploited zero-day vulnerabilities impacting iPhones, Macs, and iPads. Apple has released emergency security updates to address two actively exploited zero-day vulnerabilities, tracked as CVE-2023-28205 and CVE-2023-28206, impacting iPhones, Macs, and iPads. Impacted devices include: iPhone 8 and later, iPad Pro (all models), iPad Air 3rd generation and later, iPad 5th generation and later, iPad mini 5th generation and later, and

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

The Last Watchdog
APRIL 3, 2023
Modern cyber attacks are ingenious — and traditional vulnerability management, or VM, simply is no longer very effective. Related: Taking a risk-assessment approach to VM Unlike a typical cyber attack that exploits a software vulnerability, recent cyber attacks exploit other security risks, such as misconfigurations, security deviations, and posture anomalies.

Data Breach Today
APRIL 4, 2023
Tallahassee Memorial Says Patient Data 'Obtained' in February Security Incident A Florida-based community healthcare system has begun notifying about 20,000 individuals whose information was compromised in a data security incident that prompted the organization to operate under its IT downtime procedures, including diverting some emergency patients, for two weeks in February.

WIRED Threat Level
APRIL 4, 2023
Italy’s recent ban of Open AI’s generative text tool may just be the beginning of ChatGPT's regulatory woes.
Security Affairs
APRIL 7, 2023
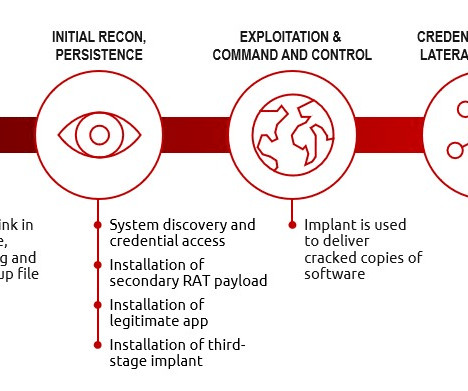
Microsoft announced it has taken legal action to disrupt the illegal use of copies of the post-exploitation tool Cobalt Strike by cybercriminals. Cobalt Strike is a paid penetration testing product that allows an attacker to deploy an agent named ‘Beacon’ on the victim machine. The Beacon includes a wealth of functionality for the attacker, including, but not limited to command execution, key logging, file transfer, SOCKS proxying, privilege escalation, mimikatz, port scanning and lateral movem

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Troy Hunt
APRIL 5, 2023
A quick summary first before the details: This week, the FBI in cooperation with international law enforcement partners took down a notorious marketplace trading in stolen identity data in an effort they've named "Operation Cookie Monster" They've provided millions of impacted email addresses and passwords to Have I Been Pwned (HIBP) so that victims of the incident can discover if they have been exposed.

Data Breach Today
APRIL 5, 2023
19-Year-Old José Huerta Allegedly Hacked A Government File Transfer System Spanish National Police arrested Friday a teenager hacker who allegedly stole the sensitive data of more than half a million taxpayers from the national revenue service and boasted in an online podcast about having access to personal data of 90 percent of the population.

WIRED Threat Level
APRIL 6, 2023
Amnezia, a free virtual private network, allows users to set up their own servers, making it harder for Moscow to block this portal to the outside world.
Security Affairs
APRIL 6, 2023
Experts warn that Telegram is becoming a privileged platform for phishers that use it to automate their activities and for providing various services. Kaspersky researchers have published an analysis of phishers’ Telegram channels used to promote their services and products. The experts pointed out that crooks engaged in phishing activities have started to rely on the popular instant messaging platform more in recent months.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.
Dark Reading
APRIL 6, 2023
A flaw in Twitter code allows bot abuse to trick the algorithm into suppressing certain accounts.

Data Breach Today
APRIL 6, 2023
Russian Group Targets Patient Care and Evolves Its Tactics, HHS HC3 Report Warns Most of the healthcare organizations hit by distributed denial-of-service attacks by pro-Russia hacktivists in January have one or more level 1 trauma centers, indicating that the attackers aimed to disrupt care for the most critically ill and injured patients, according to a new government report.

WIRED Threat Level
APRIL 3, 2023
Mullvad Browser, a collaboration between the nonprofit and Mullvad VPN, offers an anti-tracking browser designed to be used with a VPN.
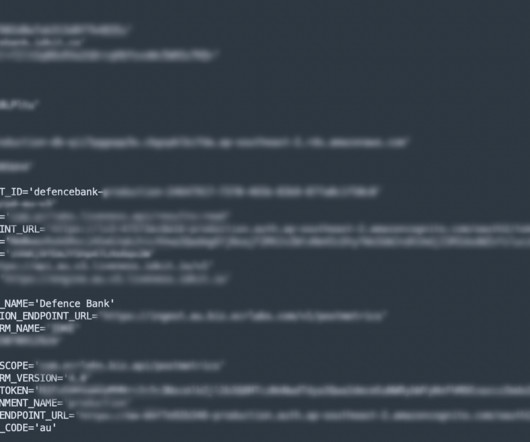
Security Affairs
APRIL 6, 2023
A digital identification tool provided by OCR Labs to major banks and government agencies leaked sensitive credentials, putting clients at severe risk. London-based OCR Labs is a major provider of digital ID verification tools. Its services are used by companies and financial institutions including BMW, Vodafone, the Australian government, Westpac, ANZ, HSBC, and Virgin Money.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!
eSecurity Planet
APRIL 7, 2023
Kali Linux turns 10 this year, and to celebrate, the Linux penetration testing distribution has added defensive security tools to its arsenal of open-source security tools. It remains to be seen if Kali Purple will do for defensive open source security tools what Kali Linux has done for open source pentesting, but the addition of more than 100 open source tools for SIEM , incident response , intrusion detection and more should raise the profile of those defensive tools.

Data Breach Today
APRIL 5, 2023
International Operation Led by FBI Results in Hundreds of Arrests The FBI and other national police are touting an operation that dismantled Genesis Market, a marketplace used by ransomware hackers and bank thieves to gain ongoing access to victims' computers. Genesis Market since 2018 offered access to more than 1.5 million compromised computers around the world.

WIRED Threat Level
APRIL 6, 2023
Without an information sharing and analysis center, the country’s food and agriculture sector is uniquely vulnerable to hackers.
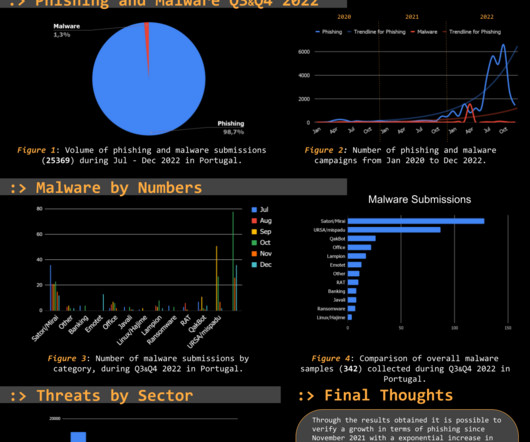
Security Affairs
APRIL 6, 2023
The Threat Report Portugal: H2 2022 compiles data collected on the malicious campaigns that occurred from July to December, H2, 2022. The Portuguese Abuse Open Feed 0xSI_f33d is an open-sharing database with the ability to collect indicators from multiple sources, developed and maintained by Segurança-Informática. This feed is based on automatic searches and is supported by a healthy community of contributors.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Dark Reading
APRIL 5, 2023
Using only ChatGPT prompts, a Forcepoint researcher convinced the AI to create malware for finding and exfiltrating specific documents, despite its directive to refuse malicious requests.

Data Breach Today
APRIL 3, 2023
Online Services Are Offline Hard disk drive maker Western Digital disclosed a hacking incident the company says likely resulted in data theft. Online services offered by the California company - including personal and enterprise cloud storage and email and push notifications - are down as of publication.

WIRED Threat Level
APRIL 3, 2023
North Korean hackers appear to have used the corrupted VoIP software to go after just a handful of crypto firms with “surgical precision.
Let's personalize your content