3 Classes of Account Fraud That Can Cost Your Company Big Time
Dark Reading
MARCH 22, 2021
Understanding each one can go a long way toward demystifying the topic as a whole - and combatting the threat.

Dark Reading
MARCH 22, 2021
Understanding each one can go a long way toward demystifying the topic as a whole - and combatting the threat.
AIIM
MARCH 23, 2021
Many organizations have an obligation to maintain the information they create and receive as part of regular business activities and to ensure that the information is secured and maintained in official filing systems. But, with an endless amount of information flowing in and out of your business on a daily basis - how do you determine what to capture and what to avoid?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

erwin
MARCH 25, 2021
erwin recently hosted the second in its six-part webinar series on the practice of data governance and how to proactively deal with its complexities. Led by Frank Pörschmann of iDIGMA GmbH, an IT industry veteran and data governance strategist, the second webinar focused on “ The Value of Data Governance & How to Quantify It.”. As Mr. Pörschmann highlighted at the beginning of the series, data governance works best when it is strongly aligned with the drivers, motivations and goals of the bu

Security Affairs
MARCH 26, 2021
The Federal Bureau of Investigation (FBI) issued an alert to warn that the Mamba ransomware is abusing the DiskCryptor open source tool to encrypt entire drives. The Federal Bureau of Investigation (FBI) published an alert to warn that the Mamba ransomware is abusing the DiskCryptor open-source tool (aka HDDCryptor, HDD Cryptor) to encrypt entire drives.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Data Breach Today
MARCH 21, 2021
BIG-IP Server Flaw Ranked 9.8 out of 10 in Severity Threats actors are actively exploiting a critical remote code vulnerability in F5 Networks' BIG-IP server appliances, for which patches were released by the company on March 10. The vulnerability has a CVSS ranking of 9.8 out of 10 - highly critical.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

WIRED Threat Level
MARCH 21, 2021
DearCry is the first attack to use the same Microsoft Exchange vulnerabilities, but its lack of sophistication lessens the threat.
Security Affairs
MARCH 26, 2021
Accenture security researchers published an analysis of the latest Hades campaign, which is ongoing since at least December 2020. . Accenture’s Cyber Investigation & Forensic Response (CIFR) and Cyber Threat Intelligence (ACTI) teams published an analysis of the latest campaign conducted by financially motivated threat group Hades which have been operating since at least December 2020. .

Data Breach Today
MARCH 21, 2021
PC and Device Maker Appears to Have Been Targeted by REvil Acer, one of the world's largest PC and device makers, has reportedly been targeted by the ransomware gang REvil, aka Sodinokibi, according to multiple published reports. To date, the Taiwanese company has not confirmed it has been attacked, but data has been posted to the gang's darknet site.
Krebs on Security
MARCH 22, 2021
Remember Norse Corp. , the company behind the interactive “pew-pew” cyber attack map shown in the image below? Norse imploded rather suddenly in 2016 following a series of managerial missteps and funding debacles. Now, the founders of Norse have launched a new company with a somewhat different vision: RedTorch , which for the past two years has marketed a mix of services to high end celebrity clients, including spying and anti-spying tools and services.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

WIRED Threat Level
MARCH 20, 2021
Plus: A mysterious zero-day spree, a high-profile hacker indictment, and more of the week’s top security news.
Security Affairs
MARCH 20, 2021
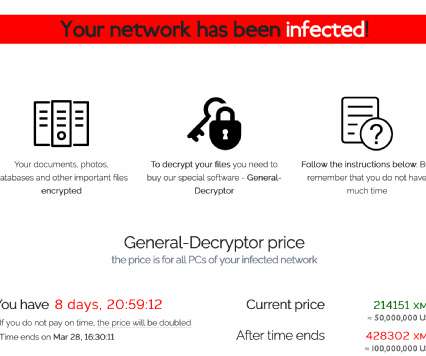
Taiwanese multinational hardware and electronics corporation Acer was victim of a REvil ransomware attack, the gang demanded a $50,000,000 ransom. Taiwanese computer giant Acer was victim of the REvil ransomware attack, the gang is demanding the payment of a $50,000,000 ransom, the largest one to date. Acer is the world’s 6th-largest PC vendor by unit sales as of January 2021, it has more than 7,000 employees (2019) and in 2019 declared 234.29 billion in revenue.
Data Breach Today
MARCH 24, 2021
Investigation Continues; Law Enforcement Notified Insurance provider CNA reported Tuesday it was victimized over the weekend by a "cybersecurity attack" that caused a network disruption and impacted certain systems, including corporate email.

AIIM
MARCH 25, 2021
In another post this week, we took a look at the first step in the information lifecycle – information capture. We not only talked about the importance of capture, but we also talked about what you should be capturing and what you should avoid capturing. Today, I’d like to dig a little deeper into that discussion and talk about how to distinguish between a record and a non-record.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

WIRED Threat Level
MARCH 24, 2021
The company’s investigation into a Chinese espionage campaign took researchers beyond Facebook’s own platforms.

Security Affairs
MARCH 21, 2021
US CISA has released a new tool that allows detecting malicious activity associated with the SolarWinds hackers in compromised on-premises enterprise environments.

Data Breach Today
MARCH 23, 2021
Brian Byrne and Bastien Latge of EMVCo Discuss Enhancement of Specifications As digital payments have skyrocketed as a result of the surge in e-commerce during the pandemic, more organizations have provided feedback on enhancing EMVCo's specifications to help fight fraud, two executives with the global technical body say.

Data Protector
MARCH 21, 2021
The UK’s data protection community isn't easy to please. Privacy is big business these days, and many of its opinion formers take to social media platforms to generate noise and controversy. Why? Because noise and controversy sells. It sells seats at privacy conferences and it sells consulting time – which can be dangerous when there are no entry barriers to the privacy consulting trade.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
MARCH 25, 2021
The Locus Charter asks companies to commit to 10 principles, including minimizing data collection and actively seeking consent from users.

Security Affairs
MARCH 24, 2021
Security experts reported that a second ransomware gang, named Black Kingdom , is targeting Microsoft Exchange servers. After the public disclosure of ProxyLogon vulnerabilities, multiple threat actors started targeting vulnerable Microsoft Exchange servers exposed online. The first ransomware gang exploiting the above issues in attacks in the wild was a group tracked as DearCry.

Data Breach Today
MARCH 23, 2021
Employee and Customer Information Compromised in January Attack; ICO Investigating British clothing and accessories retailer Fat Face says it detected a data breach in January, which exposed personal information - including partial payment card numbers - for an unspecified number of customers and employees. The Information Commissioner's Office is investigating.

Schneier on Security
MARCH 26, 2021
Lukasz Olejnik has a good essay on hacking weapons systems. Basically, there is no reason to believe that software in weapons systems is any more vulnerability free than any other software. So now the question is whether the software can be accessed over the Internet. Increasingly, it is. This is likely to become a bigger problem in the near future.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

WIRED Threat Level
MARCH 23, 2021
Cloudflare says it’s possible to build a version of the notoriously slow and buggy tool without compromising on speed.
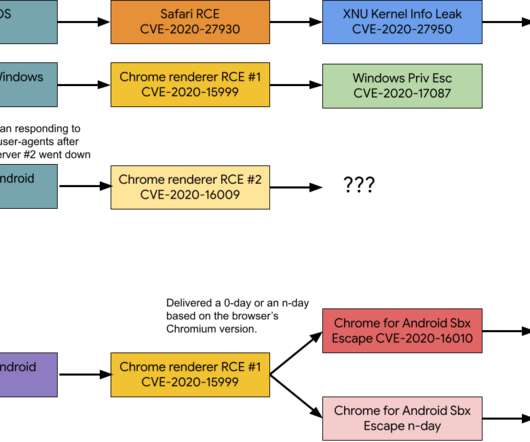
Security Affairs
MARCH 20, 2021
A hacking group has employed at least 11 zero-day flaws as part of an operation that took place in 2020 and targeted Android, iOS, and Windows users. Google’s Project Zero security team published a report about the activity of a mysterious hacking group that operated over the course of 2020 and exploited at least 11 zero-day vulnerabilities in its attacks on Android, iOS, and Windows users.

Data Breach Today
MARCH 23, 2021
Proofpoint Update Describes the Fraud Tactics The SolarWinds supply chain attackers manipulated OAuth app certificates to maintain persistence and access privileged resources, including email, according to researchers at Proofpoint.

Schneier on Security
MARCH 22, 2021
This is a longish video that describes a profitable computer banking scam that’s run out of call centers in places like India. There’s a lot of fluff about glitterbombs and the like, but the details are interesting. The scammers convince the victims to give them remote access to their computers, and then that they’ve mistyped a dollar amount and have received a large refund that they didn’t deserve.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

WIRED Threat Level
MARCH 25, 2021
Vendors are cashing in on people desperate to leapfrog the line—or falsely certify that they got the shot.

Security Affairs
MARCH 23, 2021
This week, IoT company Sierra Wireless disclosed a ransomware attack that hit its internal IT systems on March 20 and disrupted its production. Sierra Wireless is a Canadian multinational wireless communications equipment designer and manufacturer headquartered in Richmond, British Columbia, Canada. The company sells mobile computing and machine-to-machine (M2M) communications products that work over cellular networks.

Data Breach Today
MARCH 23, 2021
Acting Director Describes Latest Steps in Battle Against Ransomware The Cybersecurity and Infrastructure Security Agency will soon use its new subpoena powers authorized under the 2021 National Defense Authorization Act to help in the battle against ransomware attacks and other cyberthreats, says Brandon Wales, the acting agency director.
Let's personalize your content