2021 Security Budgets: Top Priorities, New Realities
Dark Reading
DECEMBER 14, 2020
An unprecedented 2020 has shaken up security leaders' usual list of must-have technologies. What's on the horizon? They share with us their spending plans for 2021.

Dark Reading
DECEMBER 14, 2020
An unprecedented 2020 has shaken up security leaders' usual list of must-have technologies. What's on the horizon? They share with us their spending plans for 2021.

Data Breach Today
DECEMBER 13, 2020
SolarWinds: Flawed Updates in Orion Platform May be Source of Attacks The U.S. Commerce Department confirmed on Sunday it had been targeted by hackers, and the U.S. Treasury has also reportedly been struck. The intrusions may be linked to a vulnerability in updates SolarWinds made to its Orion network monitoring product earlier this year, which could mean a broad impact.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
DECEMBER 16, 2020
Despite years of warning, the US still has no good answer for the sort of “supply chain” attack that let Russia run wild.

Krebs on Security
DECEMBER 14, 2020
Communications at the U.S. Treasury and Commerce Departments were reportedly compromised by a supply chain attack on SolarWinds , a security vendor that helps the federal government and a range of Fortune 500 companies monitor the health of their IT networks. Given the breadth of the company’s customer base, experts say the incident may be just the first of many such disclosures.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

The Last Watchdog
DECEMBER 13, 2020
One legacy of the ongoing global pandemic is that companies now realize that a secured and well-supported remote workforce is possible. Recently, the University of Illinois and the Harvard Business School conducted a study, and 16% of companies reported switching their employees to work at home from offices at least twice a week. Related: SASE translates into secure connectivity.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

AIIM
DECEMBER 17, 2020
Why Business Automation Matters. Business process management is an essential part of a growing business. Without it, organizations could face low customer satisfaction, lack of communication, and a higher chance of error. By letting computers take care of menial, repetitive day-to-day tasks, automation can save businesses money and time. Without the human component in handling data, there is a lower chance of error.
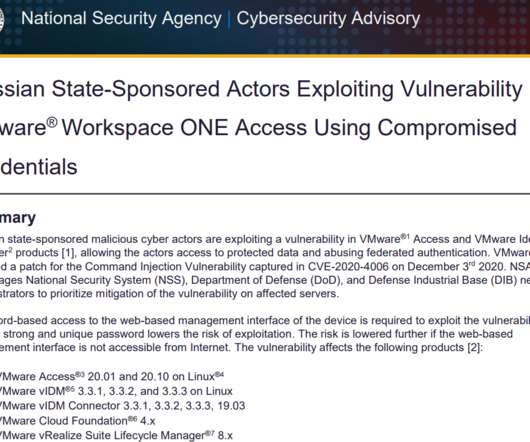
Krebs on Security
DECEMBER 18, 2020
U.S. government cybersecurity agencies warned this week that the attackers behind the widespread hacking spree stemming from the compromise at network software firm SolarWinds used weaknesses in other, non-SolarWinds products to attack high-value targets. According to sources, among those was a flaw in software virtualization platform VMware , which the U.S.
Security Affairs
DECEMBER 18, 2020
Threat actors continue to trade critical medical data in the Dark Web while organizations are involved in the response to the COVID-19 pandemic. Cybercrime organizations continue to be very active while pharmaceutical organizations are involved in the development of a COVID-19 vaccine and medicines to cure the infections. Experts from Cyble discovered in several forums on the dark web, the offer for enormous repositories of critical medical that wee stolen from multiple organizations.

Data Breach Today
DECEMBER 14, 2020
Fellow Victim FireEye Traces Breaches to Trojanized SolarWinds Software Updates The U.S. Commerce Department confirmed on Sunday it had been targeted by hackers, and the U.S. Treasury has also reportedly been struck. The intrusions appear linked to subverted software updates for SolarWinds' Orion network monitoring product, which is widely used by companies and the U.S. government.

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

Schneier on Security
DECEMBER 18, 2020
The NSA has published an advisory outlining how “malicious cyber actors” are “are manipulating trust in federated authentication environments to access protected data in the cloud.” This is related to the SolarWinds hack I have previously written about , and represents one of the techniques the SVR is using once it has gained access to target networks.

Krebs on Security
DECEMBER 16, 2020
A key malicious domain name used to control potentially thousands of computer systems compromised via the months-long breach at network monitoring software vendor SolarWinds was commandeered by security experts and used as a “killswitch” designed to turn the sprawling cybercrime operation against itself, KrebsOnSecurity has learned. Austin, Texas-based SolarWinds disclosed this week that a compromise of its software update servers earlier this year may have resulted in malicious code
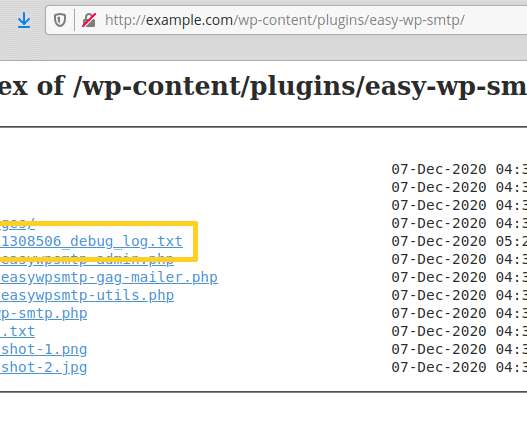
Security Affairs
DECEMBER 12, 2020
Threat actors are actively exploiting a zero-day vulnerability in the popular Easy WP SMTP WordPress plugin installed on more than 500,000 sites. Hackers are actively exploiting a zero-day vulnerability in the popular Easy WP SMTP WordPress plugin to reset passwords for admin accounts. The SMTP WordPress plugin is installed on more than 500,000 sites, but despite the security patch has been released earlier this week many sites are yet to be patched.

Data Breach Today
DECEMBER 16, 2020
Trace Fooshee of Aite Group Provides an Outlook of Key Trends What kind of financial fraud can we expect in the year ahead? Trace Fooshee of Aite Group offers a forecast based on a new report.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Schneier on Security
DECEMBER 18, 2020
Gizmodo is reporting that schools in the US are buying equipment to unlock cell phones from companies like Cellebrite: Gizmodo has reviewed similar accounting documents from eight school districts, seven of which are in Texas, showing that administrators paid as much $11,582 for the controversial surveillance technology. Known as mobile device forensic tools (MDFTs), this type of tech is able to siphon text messages, photos, and application data from student’s devices.

Dark Reading
DECEMBER 17, 2020
Extended Detection and Response (XDR) could be the security management technology of your dreams.or not. What makes this technical 'evolution' so interesting to so many companies?

Security Affairs
DECEMBER 16, 2020
Microsoft, FireEye, and GoDaddy have partnered to create a kill switch for the Sunburst backdoor that was employed in the recent SolarWinds hack. Microsoft, FireEye, and GoDaddy have created a kill switch for the Sunburst backdoor that was used in SolarWinds supply chain attack. Last week, Russia-linked hackers breached SolarWinds, the attackers had used a trojanized SolarWinds Orion business software updates to distribute the backdoor tracked as SUNBURST (aka Solarigate (Microsoft)).

Data Breach Today
DECEMBER 18, 2020
The latest edition of the ISMG Security Report features an analysis of what we know so far about the impact of the SolarWinds supply chain hack and how to respond.

Speaker: Anindo Banerjea, CTO at Civio & Tony Karrer, CTO at Aggregage
When developing a Gen AI application, one of the most significant challenges is improving accuracy. This can be especially difficult when working with a large data corpus, and as the complexity of the task increases. The number of use cases/corner cases that the system is expected to handle essentially explodes. 💥 Anindo Banerjea is here to showcase his significant experience building AI/ML SaaS applications as he walks us through the current problems his company, Civio, is solving.

Schneier on Security
DECEMBER 17, 2020
The New York Times has more details. About 18,000 private and government users downloaded a Russian tainted software update – a Trojan horse of sorts – that gave its hackers a foothold into victims’ systems, according to SolarWinds, the company whose software was compromised. Among those who use SolarWinds software are the Centers for Disease Control and Prevention, the State Department, the Justice Department, parts of the Pentagon and a number of utility companies.

Threatpost
DECEMBER 18, 2020
Examining the backdoor's DNS communications led researchers to find a government agency and a big U.S. telco that were flagged for further exploitation in the spy campaign.

Security Affairs
DECEMBER 17, 2020
FBI says DoppelPaymer ransomware gang is harassing victims who refuse to pay, threatening to send individuals to their homes. FBI is warning of a new escalation in the extortion activities of the DoppelPaymer ransomware gang, the operators have been calling victims, threatening to send individuals to their homes if they don’t pay the ransom. According to a private industry notification alert (PIN), sent by the FBI to private organizations, the Bureau is aware of extortion activities that h
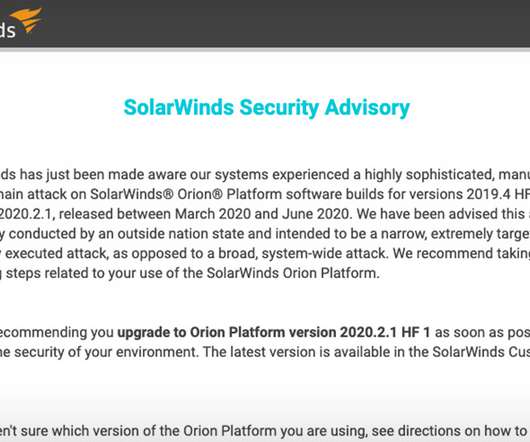
Data Breach Today
DECEMBER 14, 2020
Mitigation Advice Includes Immediate Updates and Scans for Signs of Compromise Warning: The breach of FireEye disclosed last week traces to a sophisticated campaign involving Trojanized versions of SolarWinds Orion software used by hundreds of large businesses and government agencies. Experts are urging users to immediately upgrade the software and begin looking for signs of compromise.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Schneier on Security
DECEMBER 15, 2020
This is interesting : Toward the end of the second incident that Volexity worked involving Dark Halo, the actor was observed accessing the e-mail account of a user via OWA. This was unexpected for a few reasons, not least of which was the targeted mailbox was protected by MFA. Logs from the Exchange server showed that the attacker provided username and password authentication like normal but were not challenged for a second factor through Duo.

Threatpost
DECEMBER 17, 2020
Sources said the DoE suffered "damage" in the attack, which also likely extends beyond the initially known SolarWinds Orion attack vector.
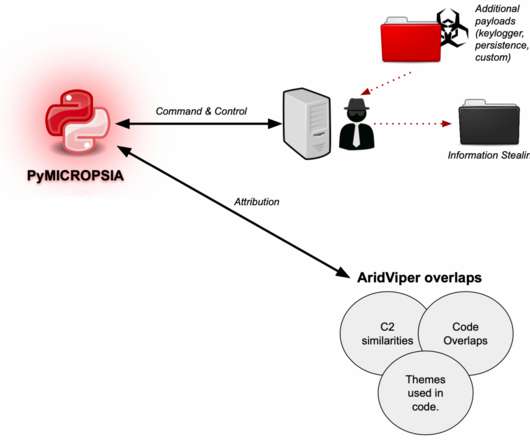
Security Affairs
DECEMBER 15, 2020
Experts discovered a new Windows info-stealer, named PyMICROPSIA, linked to AridViper group that is rapidly evolving to target other platforms. Experts from Palo Alto Networks’s Unit 42 discovered a new Windows info-stealing malware, named PyMICROPSIA, that might be used soon to also target Linux and macOS systems. Experts spotted the PyMICROPSIA info stealer while investigating attacks of the AridViper group (also tracked as Desert Falcon and APT-C-23 ).

Data Breach Today
DECEMBER 17, 2020
IBM: Attackers Target Mobile Banking Customers in US, Europe IBM Trusteer reports that a hacking group is using mobile emulators to spoof banking customers' mobile devices and steal millions of dollars from banks in the U.S. and Europe.

Speaker: Aindra Misra, Senior Manager, Product Management (Data, ML, and Cloud Infrastructure) at BILL
Join us for an insightful webinar that explores the critical intersection of data privacy and AI governance. In today’s rapidly evolving tech landscape, building robust governance frameworks is essential to fostering innovation while staying compliant with regulations. Our expert speaker, Aindra Misra, will guide you through best practices for ensuring data protection while leveraging AI capabilities.

Schneier on Security
DECEMBER 17, 2020
Sophisticated spyware, sold by surveillance tech companies to Mexican government agencies, are ending up in the hands of drug cartels : As many as 25 private companies — including the Israeli company NSO Group and the Italian firm Hacking Team — have sold surveillance software to Mexican federal and state police forces, but there is little or no regulation of the sector — and no way to control where the spyware ends up, said the officials.

Data Protection Report
DECEMBER 17, 2020
On 25 November 2020, the European Commission ( EC ) published its proposed Data Governance Regulation (the DGR ), which will create a new legal framework to encourage the development of a European single market for data. This is part three of a series of three blog posts. In this blog post, we consider the DGR’s relationship to competition law rules.
Security Affairs
DECEMBER 15, 2020
Norwegian cruise company Hurtigruten disclosed a cyber attack that impacted its entire worldwide digital infrastructure. The Norwegian cruise company Hurtigruten announced its entire worldwide digital infrastructure was the victim of a cyber attack. “It’s a serious attack,” said the Hurtigruten’s chief digital officer Ole-Marius Moe-Helgesen in a statement. “The entire worldwide digital infrastructure of Hurtigruten seems to have been hit.” “The attack s
Let's personalize your content