2021 Security Budgets: Top Priorities, New Realities
Dark Reading
DECEMBER 14, 2020
An unprecedented 2020 has shaken up security leaders' usual list of must-have technologies. What's on the horizon? They share with us their spending plans for 2021.

Dark Reading
DECEMBER 14, 2020
An unprecedented 2020 has shaken up security leaders' usual list of must-have technologies. What's on the horizon? They share with us their spending plans for 2021.

Data Breach Today
DECEMBER 13, 2020
SolarWinds: Flawed Updates in Orion Platform May be Source of Attacks The U.S. Commerce Department confirmed on Sunday it had been targeted by hackers, and the U.S. Treasury has also reportedly been struck. The intrusions may be linked to a vulnerability in updates SolarWinds made to its Orion network monitoring product earlier this year, which could mean a broad impact.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
DECEMBER 16, 2020
Despite years of warning, the US still has no good answer for the sort of “supply chain” attack that let Russia run wild.
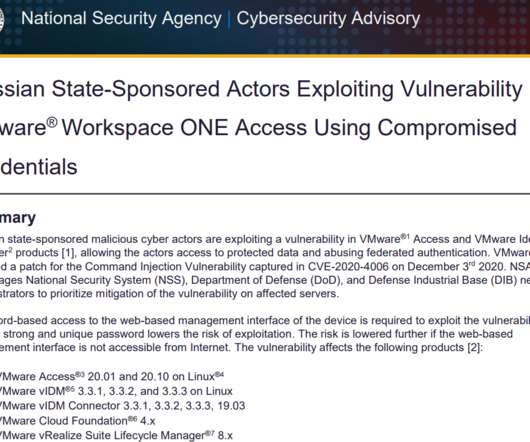
Krebs on Security
DECEMBER 18, 2020
U.S. government cybersecurity agencies warned this week that the attackers behind the widespread hacking spree stemming from the compromise at network software firm SolarWinds used weaknesses in other, non-SolarWinds products to attack high-value targets. According to sources, among those was a flaw in software virtualization platform VMware , which the U.S.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.
Security Affairs
DECEMBER 18, 2020
Threat actors continue to trade critical medical data in the Dark Web while organizations are involved in the response to the COVID-19 pandemic. Cybercrime organizations continue to be very active while pharmaceutical organizations are involved in the development of a COVID-19 vaccine and medicines to cure the infections. Experts from Cyble discovered in several forums on the dark web, the offer for enormous repositories of critical medical that wee stolen from multiple organizations.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

WIRED Threat Level
DECEMBER 14, 2020
A supply chain attack against IT company SolarWinds has exposed as many as 18,000 companies to Cozy Bear's attacks.

Krebs on Security
DECEMBER 16, 2020
A key malicious domain name used to control potentially thousands of computer systems compromised via the months-long breach at network monitoring software vendor SolarWinds was commandeered by security experts and used as a “killswitch” designed to turn the sprawling cybercrime operation against itself, KrebsOnSecurity has learned. Austin, Texas-based SolarWinds disclosed this week that a compromise of its software update servers earlier this year may have resulted in malicious code

Security Affairs
DECEMBER 18, 2020
Microsoft confirms that it was also breached in the SolarWinds supply chain hack, but excluded that the attack impacted its customers. Microsoft has confirmed that it was one of the companies breached in the recent SolarWinds supply chain attack, but the IT giant denied that the nation-state actors compromised its software supply-chain to infect its customers.

Data Breach Today
DECEMBER 14, 2020
Fellow Victim FireEye Traces Breaches to Trojanized SolarWinds Software Updates The U.S. Commerce Department confirmed on Sunday it had been targeted by hackers, and the U.S. Treasury has also reportedly been struck. The intrusions appear linked to subverted software updates for SolarWinds' Orion network monitoring product, which is widely used by companies and the U.S. government.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

WIRED Threat Level
DECEMBER 15, 2020
Amateur and professional cryptographers, including those at the FBI, had been trying to decode the infamous serial killer's message to the media for decades.

The Last Watchdog
DECEMBER 13, 2020
One legacy of the ongoing global pandemic is that companies now realize that a secured and well-supported remote workforce is possible. Recently, the University of Illinois and the Harvard Business School conducted a study, and 16% of companies reported switching their employees to work at home from offices at least twice a week. Related: SASE translates into secure connectivity.
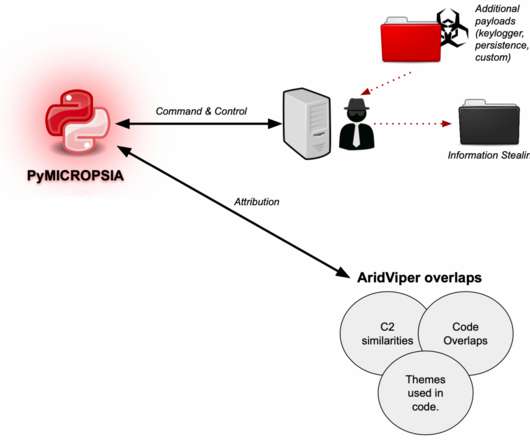
Security Affairs
DECEMBER 15, 2020
Experts discovered a new Windows info-stealer, named PyMICROPSIA, linked to AridViper group that is rapidly evolving to target other platforms. Experts from Palo Alto Networks’s Unit 42 discovered a new Windows info-stealing malware, named PyMICROPSIA, that might be used soon to also target Linux and macOS systems. Experts spotted the PyMICROPSIA info stealer while investigating attacks of the AridViper group (also tracked as Desert Falcon and APT-C-23 ).

Data Breach Today
DECEMBER 18, 2020
The latest edition of the ISMG Security Report features an analysis of what we know so far about the impact of the SolarWinds supply chain hack and how to respond.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

WIRED Threat Level
DECEMBER 14, 2020
It remains unclear how effective the warnings will be, but the attempt alone is a promising development.

AIIM
DECEMBER 17, 2020
Why Business Automation Matters. Business process management is an essential part of a growing business. Without it, organizations could face low customer satisfaction, lack of communication, and a higher chance of error. By letting computers take care of menial, repetitive day-to-day tasks, automation can save businesses money and time. Without the human component in handling data, there is a lower chance of error.

Security Affairs
DECEMBER 14, 2020
Last week, ZDnet reported in an exclusive that the tech unicorn UiPath admitted having accidentally exposed the personal details of some users. UiPath is a leading Robotic Process Automation vendor providing a complete software platform to help organizations efficiently automate business processes. The startup started reporting the security incident to its customers that had their data accidentally exposed online, only users who registered on its platform before or on March 17, 2020, were impac

Data Breach Today
DECEMBER 16, 2020
Trace Fooshee of Aite Group Provides an Outlook of Key Trends What kind of financial fraud can we expect in the year ahead? Trace Fooshee of Aite Group offers a forecast based on a new report.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
DECEMBER 13, 2020
From messaging to maps, many popular apps slurp up your data to sell you ads. There’s a better way.

Schneier on Security
DECEMBER 18, 2020
The NSA has published an advisory outlining how “malicious cyber actors” are “are manipulating trust in federated authentication environments to access protected data in the cloud.” This is related to the SolarWinds hack I have previously written about , and represents one of the techniques the SVR is using once it has gained access to target networks.
Security Affairs
DECEMBER 15, 2020
Norwegian cruise company Hurtigruten disclosed a cyber attack that impacted its entire worldwide digital infrastructure. The Norwegian cruise company Hurtigruten announced its entire worldwide digital infrastructure was the victim of a cyber attack. “It’s a serious attack,” said the Hurtigruten’s chief digital officer Ole-Marius Moe-Helgesen in a statement. “The entire worldwide digital infrastructure of Hurtigruten seems to have been hit.” “The attack s

Data Breach Today
DECEMBER 18, 2020
Cybercriminals Are Using Phone Calls to Pressure Victims The FBI is warning of increased activity - including disruption of a police dispatch system - by the operators of DoppelPaymer, a ransomware variant linked to high-profile attacks over the last several months. The cybercriminals also are calling victims to pressure them into paying ransoms.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

Threatpost
DECEMBER 17, 2020
Sources said the DoE suffered "damage" in the attack, which also likely extends beyond the initially known SolarWinds Orion attack vector.

Schneier on Security
DECEMBER 18, 2020
Gizmodo is reporting that schools in the US are buying equipment to unlock cell phones from companies like Cellebrite: Gizmodo has reviewed similar accounting documents from eight school districts, seven of which are in Texas, showing that administrators paid as much $11,582 for the controversial surveillance technology. Known as mobile device forensic tools (MDFTs), this type of tech is able to siphon text messages, photos, and application data from student’s devices.
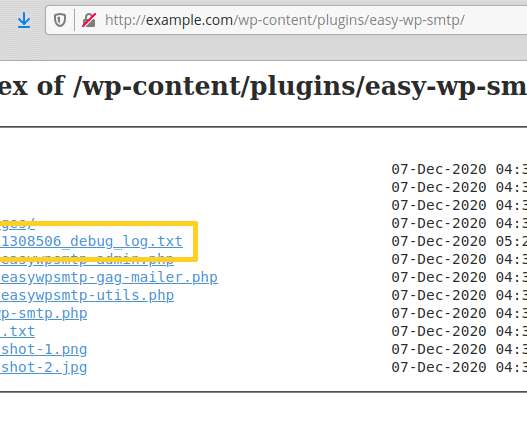
Security Affairs
DECEMBER 12, 2020
Threat actors are actively exploiting a zero-day vulnerability in the popular Easy WP SMTP WordPress plugin installed on more than 500,000 sites. Hackers are actively exploiting a zero-day vulnerability in the popular Easy WP SMTP WordPress plugin to reset passwords for admin accounts. The SMTP WordPress plugin is installed on more than 500,000 sites, but despite the security patch has been released earlier this week many sites are yet to be patched.
Data Breach Today
DECEMBER 14, 2020
Mitigation Advice Includes Immediate Updates and Scans for Signs of Compromise Warning: The breach of FireEye disclosed last week traces to a sophisticated campaign involving Trojanized versions of SolarWinds Orion software used by hundreds of large businesses and government agencies. Experts are urging users to immediately upgrade the software and begin looking for signs of compromise.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Threatpost
DECEMBER 14, 2020
This is the third breach in the past few weeks for the world’s most popular streaming service.

Schneier on Security
DECEMBER 15, 2020
This is interesting : Toward the end of the second incident that Volexity worked involving Dark Halo, the actor was observed accessing the e-mail account of a user via OWA. This was unexpected for a few reasons, not least of which was the targeted mailbox was protected by MFA. Logs from the Exchange server showed that the attacker provided username and password authentication like normal but were not challenged for a second factor through Duo.

Security Affairs
DECEMBER 16, 2020
Microsoft and its partners have seized the primary domain used in the SolarWinds attack to identify the victims through sinkholing. Microsoft partnered with other cybersecurity firms to seize the primary domain used in the SolarWinds attack ( avsvmcloud[.]com ) in an attempt to identify all victims and prevent other systems from being served malicious software. here is list of DGA subdomain c2: avsvmcloud[.]com #SolarWinds #backdoor c2 domain list: [link] pic.twitter.com/NufyhDB5Zj — R.
Let's personalize your content