What Will Cybersecurity's 'New Normal' Look Like?
Dark Reading
JUNE 18, 2020
The coronavirus pandemic has forced changes for much of the business world, cybersecurity included. What can we expect going forward?

Dark Reading
JUNE 18, 2020
The coronavirus pandemic has forced changes for much of the business world, cybersecurity included. What can we expect going forward?

WIRED Threat Level
JUNE 7, 2020
Developers are working on track-and-trace systems to keep infection levels low. The apps aren't here yet, but here's what they do—and how you can enable them.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
JUNE 26, 2020
Microsoft Urges Patching, Other Mitigation Steps Microsoft is warning its customers that attackers are increasingly targeting unpatched Exchange servers, with a significant uptick in activity since April.

WIRED Threat Level
JUNE 22, 2020
The so-called BlueLeaks collection includes internal memos, financial records, and more from over 200 state, local, and federal agencies.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Data Breach Today
JUNE 12, 2020
DoppelPaymer Hit Comes as Ransomware Attacks - and Data-Leaking Shakedowns - Surge The attack sounds ripped from an episode of TV show "24": Hackers have infiltrated a government network, and they're days away from unleashing ransomware. Unfortunately for Florence, a city in Alabama, no one saved the day, and officials are sending $300,000 in bitcoins to attackers for a decryption key.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

WIRED Threat Level
JUNE 15, 2020
3somes, Gay Daddy Bear, and Herpes Dating are among the nine services that leaked the data of hundreds of thousands of users.

OpenText Information Management
JUNE 9, 2020
Remote work teams around the world are showing that despite today’s extraordinary circumstances, we can still churn out hearty levels of productivity. But it’s challenging. Maybe it’s our innate desire for connection or our drive to escape social isolation, but lately many of us are missing our teammates and the buzz of an office environment. … The post How to keep your remote work team together appeared first on OpenText Blogs.
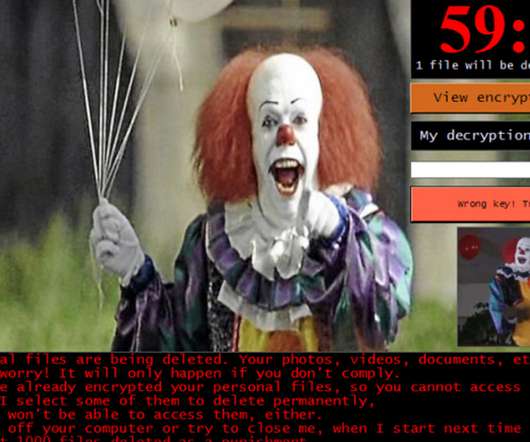
Data Breach Today
JUNE 8, 2020
Can't Stop the Crypto-Locking Malware Attacks? Criminals Keep Hitting Big Targets Ransomware gangs continue to innovate: Recently, reports have emerged of collaboration between the Maze and Lockbit gangs, and REvil not just leaking stolen data for free, but auctioning it off to the highest bidder. On the upside, however, security firms continue to release free decryptors for some strains.

Krebs on Security
JUNE 19, 2020
Hundreds of popular websites now offer some form of multi-factor authentication (MFA), which can help users safeguard access to accounts when their password is breached or stolen. But people who don’t take advantage of these added safeguards may find it far more difficult to regain access when their account gets hacked, because increasingly thieves will enable multi-factor options and tie the account to a device they control.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

Security Affairs
JUNE 20, 2020
Malicious Chrome browser extensions were employed in a surveillance campaign on a large scale, millions of users potentially impacted. Malicious Chrome browser extensions were used in a massive surveillance campaign aimed at users working in the financial services, oil and gas, media and entertainment, healthcare, government organizations, and pharmaceuticals.

Dark Reading
JUNE 26, 2020
Three ways that security teams can improve processes and collaboration, all while creating the common ground needed to sustain them.

Data Breach Today
JUNE 19, 2020
Creating Cloud-Hosted Attack Infrastructures a Common Practice, Academic Researchers Find Many ethical hackers and other security professionals, such as penetration testers, have weaponized cloud platforms to host online attack infrastructure or have used the platforms to conduct reconnaissance, according security researchers at Texas Tech University.

WIRED Threat Level
JUNE 19, 2020
Their CEOs have pledged support for reform amid the George Floyd protests—while their lawyers are fighting to preserve law enforcement’s advantage in court.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Data Breach Today
JUNE 15, 2020
Personal Details on 727,000 Accounts in 14 Countries Leaked Delivery Hero, the online food delivery service, has confirmed a data breach of its Foodora brand. Breached information includes personal details for 727,000 accounts - names, addresses, phone numbers, precise location data and hashed passwords - in 14 countries.
Krebs on Security
JUNE 21, 2020
Hundreds of thousands of potentially sensitive files from police departments across the United States were leaked online last week. The collection, dubbed “ BlueLeaks ” and made searchable online, stems from a security breach at a Texas web design and hosting company that maintains a number of state law enforcement data-sharing portals. The collection — nearly 270 gigabytes in total — is the latest release from Distributed Denial of Secrets (DDoSecrets), an alternative to

Security Affairs
JUNE 30, 2020
A threat actor is selling databases containing data belonging to 14 different companies he claimed were hacked in 2020. A threat actor is selling databases that contain user records for 14 different organizations he claimed were hacked in 2020, only for four of them ( HomeChef , Minted , Tokopedia , and Zoosk ) were previously reported data breaches.
AIIM
JUNE 25, 2020
In recent years, nothing has sparked more controversy in the information management industry than the 2017 Gartner post officially retiring the term “Enterprise Content Management (ECM)” in favor of a new term, content services. Here at AIIM, we’ve been providing independent research, educational training, and certification for over 70 years. For a good majority of that time, the focus has been on ECM and the practices associated with ECM to capture, store, manage, and preserve information.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

The Last Watchdog
JUNE 21, 2020
Ransomware is undoubtedly one of the most unnerving phenomena in the cyber threat landscape. Numerous strains of this destructive code have been the front-page news in global computer security chronicles for almost a decade now, with jaw-dropping ups and dramatic downs accompanying its progress. Related: What local government can do to repel ransomware Ransomware came into existence in 1989 as a primitive program dubbed the AIDS Trojan that was spreading via 5.25-inch diskettes.

WIRED Threat Level
JUNE 2, 2020
Rubber bullets and tear gas are billed as relatively safe. They're anything but.

Data Breach Today
JUNE 25, 2020
Superseding Indictment Expands Scope of Case, But Doesn't Add Charges The U.S Department of Justice unsealed a superseding indictment against WikiLeaks founder Julian Assange that expands the scope of the government's case against him. Federal prosecutors now allege that Assange conspired with the Anonymous and LulzSec groups to obtain classified information to publish.

Krebs on Security
JUNE 3, 2020
An exhaustive inquiry published today by a consortium of investigative journalists says a three-part series KrebsOnSecurity published in 2015 on a Romanian ATM skimming gang operating in Mexico’s top tourist destinations disrupted their highly profitable business, which raked in an estimated $1.2 billion and enjoyed the protection of top Mexican authorities.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Security Affairs
JUNE 26, 2020
A man accused to have developed distributed denial of service (DDoS) botnets based on the Mirai botnet was sentenced to 13 months in federal prison. Kenneth Currin Schuchman, 22, of Vancouver, Washington, was sentenced to 13 months in federal prison because it has developed distributed denial of service (DDoS) botnets based on the source code of Mirai botnet.

AIIM
JUNE 30, 2020
Few announcements in information management have been bigger than Gartner’s article heard round the world that announced the death of Enterprise Content Management (ECM) as we knew it. Michael Woodbridge’s quote gets straight to the point here: “ECM is now dead (kaput, finite, an ex-market name), at least in how Gartner defines the market. It’s been replaced by the term content services, a strategic concept that covers three aspects, namely content services Applications, Platforms and Components

Security Affairs
JUNE 18, 2020
79 Netgear router models are vulnerable to a severe unpatched security vulnerability that can be exploited by remote attackers to take over devices. Security experts Adam Nichols from GRIMM and d4rkn3ss from the Vietnamese internet service provider VNPT have independently reported a severe unpatched security vulnerability that affects 79 Netgear router models.
Security Affairs
JUNE 28, 2020
Asian media firm E27 suffered a security breach and hackers asked for a “donation” to provide information on the flaws they exploited in the attack. Asian media firm E27 has been hacked by a hacking group identifying themselves as “Korean Hackers” and “Team Johnwick”that asked for a “donation” to provide information on the vulnerabilities they have exploited in the attack.

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

Security Affairs
JUNE 8, 2020
A researcher is warning that Google is indexing the phone numbers of WhatsApp users raising serious privacy concerns. Google is indexing the phone numbers of WhatsApp users that could be abused by threat actors for malicious activities. Even if Google Search only revealed the phone numbers and not the identities of associated users, ill-intentioned attackers could be able to see users’ profile pictures on WhatsApp and performing a reverse-image search the user’s profile picture to gather additio
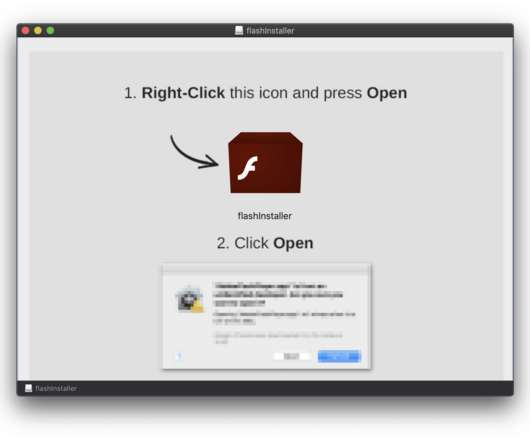
Security Affairs
JUNE 21, 2020
Shlayer Mac malware is back, the Mac threat is now spreading through new black SEO operations. Researchers spotted a new version of the Shlayer Mac malware that is spreading via poisoned Google search results. Researchers at security firm Intego observed the new variant being spread masqueraded as a fake Adobe Flash Player installer (.DMG disk image) and implementing fresh advanced evasion capabilities. “The new malware tricks victims into bypassing Apple’s built-in macOS security protecti

Security Affairs
JUNE 5, 2020
ST Engineering is the last victim of the Maze Ransomware operators that published their data on their leak website. ST Engineering is one of the leading engineering groups worldwide, it specializes in the aerospace, electronics, land systems, and marine sectors. The group operates in more than 100 countries and reported revenue of $7.86b in FY2019. The Maze ransomware operators announced the release of stolen data on their leak site.
Let's personalize your content