How Ransomware Defense is Evolving With Ransomware Attacks
Dark Reading
NOVEMBER 24, 2020
As data exfiltration threats and bigger ransom requests become the norm, security professionals are advancing from the basic "keep good backups" advice.

Dark Reading
NOVEMBER 24, 2020
As data exfiltration threats and bigger ransom requests become the norm, security professionals are advancing from the basic "keep good backups" advice.
Security Affairs
NOVEMBER 23, 2020
Boffins have demonstrated how to steal a Tesla Model X in a few minutes by exploiting vulnerabilities in the car’s keyless entry system. A team of researchers from the Computer Security and Industrial Cryptography (COSIC) group at the KU Leuven University in Belgium has demonstrated how to steal a Tesla Model X in minutes by exploiting vulnerabilities in the car’s keyless entry system.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Threatpost
NOVEMBER 27, 2020
While 2021 will present evolving threats and new challenges, it will also offer new tools and technologies that will we hope shift the balance towards the defense.

IT Governance
NOVEMBER 2, 2020
With 117 publicly reported security incidents, October 2020 is the leakiest month we’ve ever recorded. The good news is that those data breaches and cyber attacks accounted for just 18,407,479 breached records. However, it’s worth noting that, in very few incidents, the number of affected records is revealed – either because the organisation doesn’t know or because it’s not required to disclose that information.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Data Breach Today
NOVEMBER 2, 2020
Privacy Regulator in UK Cautions Organizations to Conduct Thorough Due Diligence Hotel giant Marriott has been hit with the second largest privacy fine in British history, after it failed to contain a massive, long-running data breach. But the final fine of $23.8 million was just 20% of the penalty initially proposed by the U.K.'s privacy watchdog, owing in part to COVID-19's ongoing impact.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Krebs on Security
NOVEMBER 21, 2020
Fraudsters redirected email and web traffic destined for several cryptocurrency trading platforms over the past week. The attacks were facilitated by scams targeting employees at GoDaddy , the world’s largest domain name registrar, KrebsOnSecurity has learned. The incident is the latest incursion at GoDaddy that relied on tricking employees into transferring ownership and/or control over targeted domains to fraudsters.
Security Affairs
NOVEMBER 23, 2020
The U.S. FBI is warning private industry partners of a surge in Ragnar Locker ransomware activity following a confirmed attack from April 2020. The U.S. Federal Bureau of Investigation (FBI) issued a flash alert (MU-000140-MW) to warn private industry partners of an increase of the Ragnar Locker ransomware activity following a confirmed attack from April 2020.

The Last Watchdog
NOVEMBER 9, 2020
The Internet of Things (IoT) has come a long, long way since precocious students at Carnegie Melon University installed micro-switches inside of a Coca-Cola vending machine so they could remotely check on the temperature and availability of their favorite beverages. Related: Companies sustain damage from IoT attacks That was back in 1982. Since then, IoT devices have become widely and deeply integrated into our homes, businesses, utilities and transportations systems.

Data Breach Today
NOVEMBER 12, 2020
WildWorks Data Breach Shows Danger of Sharing Sensitive Keys Over Chat Chat and collaboration software tools such as Slack are critical for software development teams. But a data breach experienced by Utah-based software developer WildWorks illustrates why developers should think twice before sharing sensitive database keys over chat.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m
Security Affairs
NOVEMBER 24, 2020
Researchers spotted a new variant of an adware and coin-miner botnet operated by Stantinko threat actors that now targets Linux servers. Researchers from Intezer have spotted a new variant of an adware and coin-miner botnet that is operated by Stantinko threat actors since 2012. The Stantinko botnet was first spotted by ESET in 2017, at the time it infected around half a million computers worldwide.

Data Breach Today
NOVEMBER 10, 2020
Investigators Find Encryption, Monitoring, Logging and Whitelisting Failures Inadequate database and privileged account monitoring, incomplete multi-factor authentication and insufficient use of encryption: Britain's privacy regulator has cited a raft of failures that contributed to the four-year breach of the Starwood guest reservation system discovered by Marriott in 2018.
Security Affairs
NOVEMBER 10, 2020
Ransomware operators use fake Microsoft Teams updates to deploy Cobalt Strike and compromise the target networks. Ransomware operators are using malicious fake Microsoft Teams updates to deliver backdoors that lead the installation of the Cobalt Strike post-exploitation tool and compromise the target network. The ongoing COVID-19 pandemic is forcing a growing number of organizations and businesses in using videoconferencing solutions, and threat actors are attempting to exploit this scenario.

Data Breach Today
NOVEMBER 28, 2020
Agency Says Hackers Can Use a Known Bug for Further Exploitation CISA is warning about a possible password leak that could affect vulnerable Fortinet VPNs and lead to further exploitation. The latest agency notice comes just days after hackers began publishing what they claim are leaked passwords on underground forums, according to researchers.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Security Affairs
NOVEMBER 15, 2020
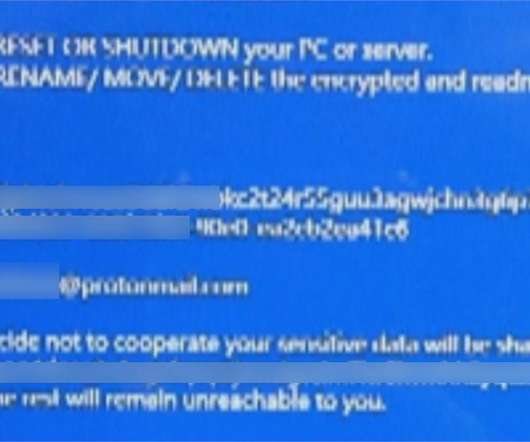
Chilean-based retail giant Cencosud has suffered a ransomware attack that impacted operations at its stores, Egregor ransomware appears to be involved. A ransomware attack, allegedly launched by the Egregor ransomware gang, hit the Chilean-based retail giant Cencosud, the incident impacted operations at its stores. Cencosud the largest retail company in Chile and the third largest listed retail company in Latin America, competing with the Brazilian Companhia Brasileira de Distribuição and the Me
Security Affairs
NOVEMBER 9, 2020
The Taiwanese electronics manufacture Compal suffered a ransomware attack over the weekend, media blames the DoppelPaymer ransomware gang. Compal Electronics is a Taiwanese original design manufacturer (ODM), handling the production of notebook computers, monitors, tablets and televisions for a variety of clients around the world, including Apple Inc., Acer, Lenovo, Dell, Toshiba, Hewlett-Packard and Fujitsu.

Security Affairs
NOVEMBER 4, 2020
The source code for the KPot information stealer was put up for auction and the REvil ransomware operators want to acquire it. The authors of KPot information stealer have put its source code up for auction , and the REvil ransomware operators will likely be the only group to bid. #KPOT source code up for sale! pic.twitter.com/fJ3BwlaHsR — ??????
Security Affairs
NOVEMBER 1, 2020
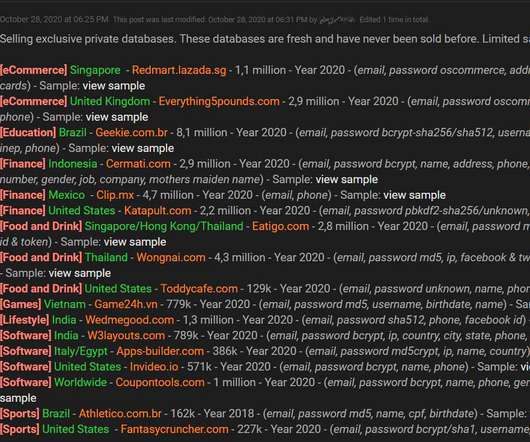
A threat actor is offering for sale account databases containing an aggregate total of 34 million user records stolen from 17 companies. A data breach broker is selling account databases containing a total of 34 million user records stolen from 17 companies. The threat actor is advertising the stolen data since October 28 on a hacker forum. Source Bleeping Computer.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.
Security Affairs
NOVEMBER 1, 2020
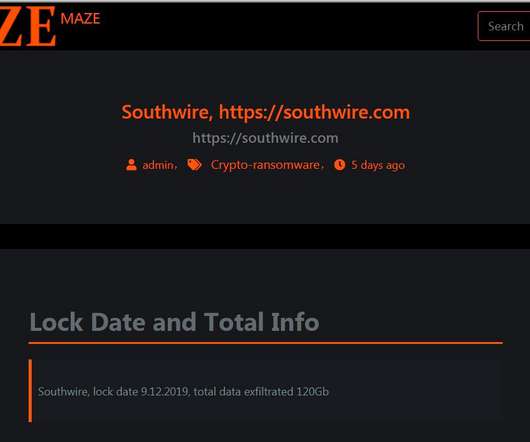
The Maze ransomware operators are shutting down their operations for more than one year the appeared on the threat landscape in May 2019. The Maze cybercrime gang is shutting down its operations, it was considered one of the most prominent and active ransomware crew since it began operating in May 2019. The gang was the first to introduce a double-extortion model in the cybercrime landscape at the end of 2019.

Security Affairs
NOVEMBER 26, 2020
US Fertility, the largest network of fertility centers in the U.S., discloses a ransomware attack that took place in September 2020. US Fertility , the largest network of fertility centers in the U.S., revealed that a ransomware attack hit its systems in September 2020. The US Fertility (USF) network is comprised of 55 locations across 10 states that completed almost 25,000 IVF cycles in 2018 through its clinics with 130,000 babies have been born. “On September 14, 2020, USF experienced

Krebs on Security
NOVEMBER 8, 2020
The body of a man found shot inside a burned out vehicle in Canada three years ago has been identified as that of Davis Wolfgang Hawke , a prolific spammer and neo-Nazi who led a failed anti-government march on Washington, D.C. in 1999, according to news reports. Homicide detectives said they originally thought the man found June 14, 2017 in a torched SUV on a logging road in Squamish, British Columbia was a local rock climber known to others in the area as a politically progressive vegan named

Security Affairs
NOVEMBER 28, 2020
The IIoT chip maker Advantech was hit by the Conti ransomware, the gang is now demanding over $13 million ransom from the company. The Conti ransomware gang hit infected the systems of industrial automation and Industrial IoT (IIoT) chip maker Advantech and is demanding over $13 million ransom (roughly 750 BTC) to avoid leaking stolen files and to provide a key to restore the encrypted files.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.
Krebs on Security
NOVEMBER 10, 2020
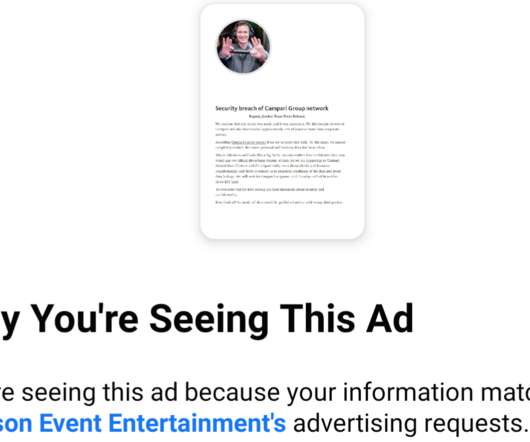
It’s bad enough that many ransomware gangs now have blogs where they publish data stolen from companies that refuse to make an extortion payment. Now, one crime group has started using hacked Facebook accounts to run ads publicly pressuring their ransomware victims into paying up. On the evening of Monday, Nov. 9, an ad campaign apparently taken out by the Ragnar Locker Team began appearing on Facebook.

Security Affairs
NOVEMBER 5, 2020
VMware has released new patches for ESXi after learning that a fix released in October for the critical CVE-2020-3992 flaw was incomplete. The virtualization giant VMware has released new fixes for ESXi after learning that a patch released in October for the critical CVE-2020-3992 flaw was incomplete. The CVE-2020-3992 vulnerability is a use-after-free bug issue that affects the OpenSLP service in ESXi, it could be exploited by a remote, unauthenticated attacker to execute arbitrary code in the

Security Affairs
NOVEMBER 1, 2020
Japan’s Nuclear Regulation Authority (NRA) issued a warning of temporary suspension of its email systems, likely caused by a cyber attack. The Japan’s Nuclear Regulation Authority (NRA) temporarily suspended its email systems, the interruption is likely caused by a cyber attack. The agency published a warning on its website, it is asking people to contact it via phone or fax because it is unable to receive emails from the outside world. “From 17:00 on October 27, 2nd year of Reiwa, sending

Security Affairs
NOVEMBER 21, 2020
The Manchester United football club has been hit by a cyber attack on their systems, it is not aware of a breach of personal data for his fans. Manchester United disclosed a cyber attack, but according to the football club it is not “currently aware of any breach of personal data associated with our fans and customers”. The club confirmed the security breach on Friday evening, it shut down its systems to prevent the malware from spreading within.

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?
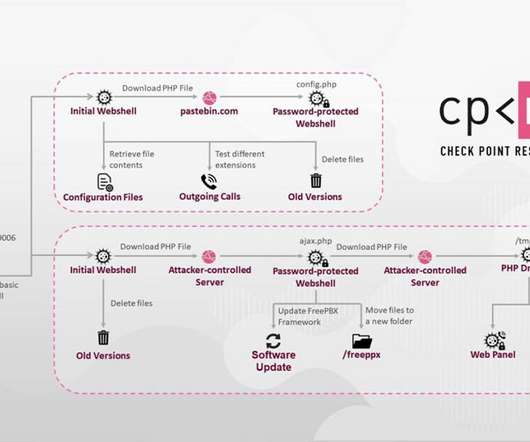
Data Breach Today
NOVEMBER 9, 2020
Attackers Exploit a Vulnerability in Asterisk VoIP PBX Servers Check Point Research has uncovered a large and likely profitable business model that involves hackers attacking and gaining control of certain VoIP services, which enables them to make phone calls through a company's compromised system.

Data Breach Today
NOVEMBER 5, 2020
Prosecutors Says Stolen Cryptocurrency Tied to Mysterious Digital Wallet The U.S. Justice Department is looking to seize more than $1 billion worth of bitcoin that investigators have linked to the notorious Silk Road darknet marketplace. The cryptocurrency was stored within a mysterious digital wallet that had been dormant for years, but the subject of much speculation.
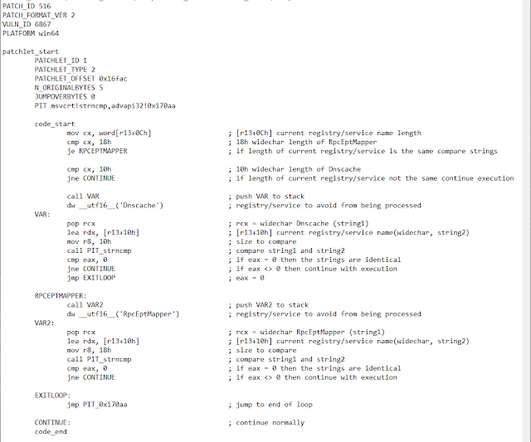
Security Affairs
NOVEMBER 26, 2020
Researcher discovers a zero-day vulnerability in Windows 7 and Windows Server 2008 while he was working on a Windows security tool. The French security researcher Clément Labro discovered a zero-day vulnerability was discovered while the security researcher was working on an update Windows security tool. The researcher was developing his own Windows privilege escalation enumeration script, named PrivescCheck , which is a sort of updated and extended version of the famous PowerUp. “If you h
Let's personalize your content