Security Lessons We've Learned (So Far) from COVID-19
Dark Reading
MARCH 17, 2020
Takeaways about fighting new fires, securely enabling remote workforces, and human nature during difficult times.

Dark Reading
MARCH 17, 2020
Takeaways about fighting new fires, securely enabling remote workforces, and human nature during difficult times.

Data Breach Today
MARCH 17, 2020
Defense Department to Issue Detailed Security Guidance As more of its employees shift to working from home due to the COVID-19 pandemic, the U.S. Department of Defense is warning workers to take security precautions to guard against potential hackers. It plans to release detailed guidance soon.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
MARCH 20, 2020
US, UK, Other Nations in Talks With Tech Firms to Provide Information The Trump administration is reportedly in talks with tech companies, including Facebook and Google, to explore whether it's possible to use real-time location data from smartphones to support efforts to slow the spread of COVID-19. But some privacy advocates are raising concerns about such tracking efforts.

Dark Reading
MARCH 31, 2020
These products and services could be of immediate help to infosec pros now protecting their organizations while working from home.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

WIRED Threat Level
MARCH 16, 2020
Shadowserver has helped keep the internet safe for 15 years. Unless it can raise funds fast, it's going to disappear.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Data Breach Today
MARCH 20, 2020
Cybereason CSO Sam Curry on Business Continuity and Reducing Risk Cybereason CSO Sam Curry is no stranger to crisis - he was on the team that responded to the RSA breach in 2011. But the COVID-19 pandemic brings an unprecedented challenge: How do you manage business continuity and reduce risk with a 100 percent remote workforce? Curry shares strategies and lessons learned.

Dark Reading
MARCH 13, 2020
While there's a ton of unbounded optimism from vendor marketing and consultant types, practitioners are still reserving a lot of judgment.

Data Breach Today
MARCH 17, 2020
Experts: This Week's 'Black Monday' Likely to Accelerate Security M&A Activity With U.S. stock markets suffering their worst day since 1987 on Monday, most technology firms took a hit as Wall Street continues to be rattled by the COVID-19 crisis. Experts predict this will drive fresh waves of consolidation and M&A in the cybersecurity market, as well as growth in hot areas.

Data Breach Today
MARCH 19, 2020
Quarantines, lockdowns, supply chain disruptions and the biggest remote workforce in history. These all part of the "new normal" in the shadow of the COVID-19 pandemic. Business continuity expert Regina Phelps has some new advice for how businesses and individuals should approach the next crucial weeks.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m
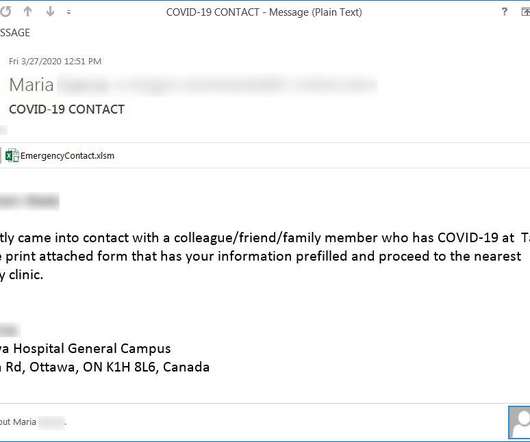
Security Affairs
MARCH 30, 2020
Security experts uncovered a new Coronavirus-themed phishing campaign, the messages inform recipients that they have been exposed to the virus. Experts continue to spot Coronavirus-themed attack, a new phishing campaign uses messages that pretend to be from a local hospital informing the victims they have been exposed to the virus and that they need urgently to be tested.
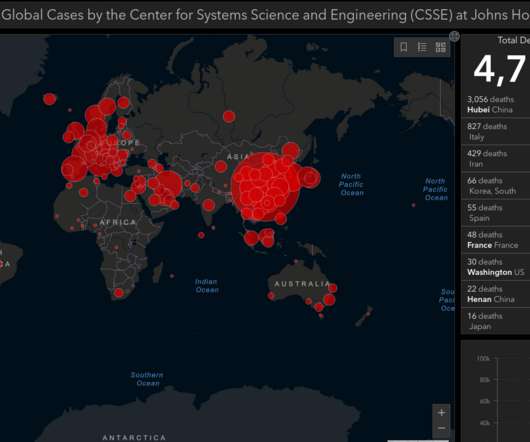
Krebs on Security
MARCH 12, 2020
Cybercriminals constantly latch on to news items that captivate the public’s attention, but usually they do so by sensationalizing the topic or spreading misinformation about it. Recently, however, cybercrooks have started disseminating real-time, accurate information about global infection rates tied to the Coronavirus/COVID-19 pandemic in a bid to infect computers with malicious software.

WIRED Threat Level
MARCH 5, 2020
The crypto wars are back in full swing. .

The Last Watchdog
MARCH 16, 2020
Many companies take an old-school approach to bringing up the rear guard, if you will, when it comes to protecting IT assets. It’s called network segmentation. The idea is to divide the network up into segments, called subnetworks, to both optimize performance as well as strengthen security. Related: A use case for endpoint encryption At RSA 2020 in San Francisco recently, I learned about how something called “micro segmentation” is rapidly emerging as a viable security strategy.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

AIIM
MARCH 12, 2020
It seems like everyone is talking about coronavirus : what it means to the global and local economies, how it impacts different industries, even how to make your own hand sanitizer to combat it. One of the key approaches many organizations are taking is to minimize sustained contact with large groups of people. This has led to the cancellation of numerous conferences and other events; many schools and universities are asking students to stay home and participate remotely.

Data Breach Today
MARCH 23, 2020
Latest Schemes Target At-Home Employees; Some Spoof Health Agencies As the global COVID-19 pandemic worsens, security firms and law enforcement, including the FBI, are warning of increasing phishing and other the cybercriminal scams targeting a largely at-home workforce.
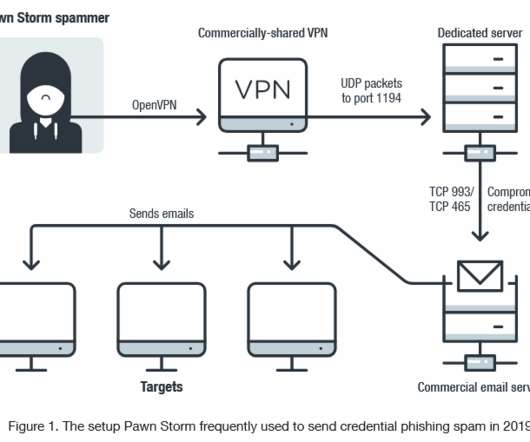
Security Affairs
MARCH 20, 2020
Experts warn of scanning activity conducted by Russia-linked APT28 cyberespionage group, hackers are searching for vulnerable mail servers. According to security researchers from Trend Micro, the Russia-linked APT28 cyberespionage group has been scanning vulnerable email servers for more than a year. The APT28 group (aka Fancy Bear , Pawn Storm , Sofacy Group , Sednit , and STRONTIUM ) has been active since at least 2007 and it has targeted governments, militaries, and security organizati
Krebs on Security
MARCH 10, 2020
FBI officials last week arrested a Russian computer security researcher on suspicion of operating deer.io , a vast marketplace for buying and selling stolen account credentials for thousands of popular online services and stores. Kirill V. Firsov was arrested Mar. 7 after arriving at New York’s John F. Kennedy Airport, according to court documents unsealed Monday.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
MARCH 27, 2020
Kitboga has built a following by trolling telemarketers. Covid-19 opportunists have given him a whole new crop of targets.

The Last Watchdog
MARCH 11, 2020
Speed is what digital transformation is all about. Organizations are increasingly outsourcing IT workloads to cloud service providers and looking to leverage IoT systems. Related: The API attack vector expands Speed translates into innovation agility. But it also results in endless ripe attack vectors which threat actors swiftly seek out and exploit.

AIIM
MARCH 31, 2020
Many of us find ourselves working from home – often rather suddenly and unexpectedly. Organizations of all sizes and in all industries are now in the position of figuring out how to ensure that the business of the business continues while staff stay home and practice effective social distancing. The good news is that the technology needed for effective working from home exists and is generally mature – though some providers have found that the sudden surge in volume can cause issues with particu

Data Breach Today
MARCH 30, 2020
Privacy Gaffe Blamed on Facebook's iOS Software Development Kit Zoom has apologized for sharing large sets of user data by default with Facebook, blaming the social network's software development kit, which it has removed from its iOS app. With COVID-19 driving unprecedented levels of remote working, video conferencing software is under the privacy and security microscope.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Security Affairs
MARCH 27, 2020
Operators behind the Ryuk Ransomware continue to target hospitals even as these organizations are involved in the fight against the Coronavirus pandemic. The threat actors behind the infamous Ryuk Ransomware continue to target hospitals, even as they are involved in containing the Coronavirus outbreak. The decision of the operators is not aligned with principal ransomware gangs that have announced they will no longer target health and medical organizations during the Coronavirus (COVID-19) pande
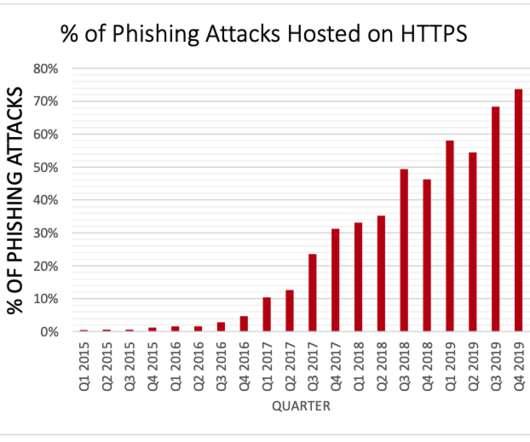
Krebs on Security
MARCH 25, 2020
Many U.S. government Web sites now carry a message prominently at the top of their home pages meant to help visitors better distinguish between official U.S. government properties and phishing pages. Unfortunately, part of that message is misleading and may help perpetuate a popular misunderstanding about Web site security and trust that phishers have been exploiting for years now.

WIRED Threat Level
MARCH 25, 2020
The little-known Postal Plan, which dates back to the Clinton era, charges mail carriers with delivering critical supplies—like vaccines—as a last resort.

Security Affairs
MARCH 16, 2020
While the Coronavirus is spreading in the U.S., a mysterious cyberattack hit the Department of Health and Human Services on Saturday. According to Bloomberg, that cited three people familiar with the matter, a cyberattack hit the U.S. Department of Health and Human Services on Saturday night. People cited by Bloomberg confirmed that the cyber attack aimed at slowing the agency’s systems down. “The U.S.

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?
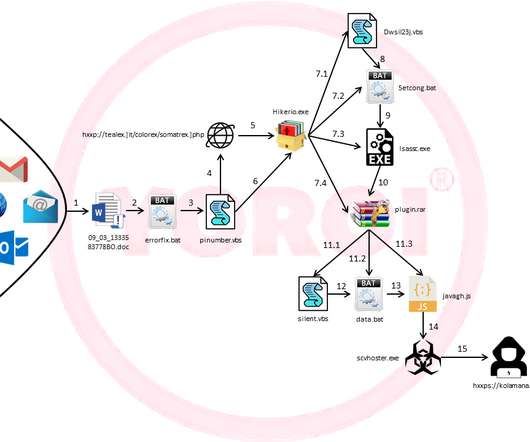
Security Affairs
MARCH 17, 2020
Malware researchers from Cybaze-Yoroi ZLab have uncovered a new Ursnif campaign that is targeting Italy with a new infection chain. Introduction. Ursnif is one of the most and widespread common threats today delivered through malspam campaigns. It appeared on the threat landscape about 13 years ago and gained its popularity since 2014 when its source code was leaked online giving the opportunity to several threat actors to develop their own version.
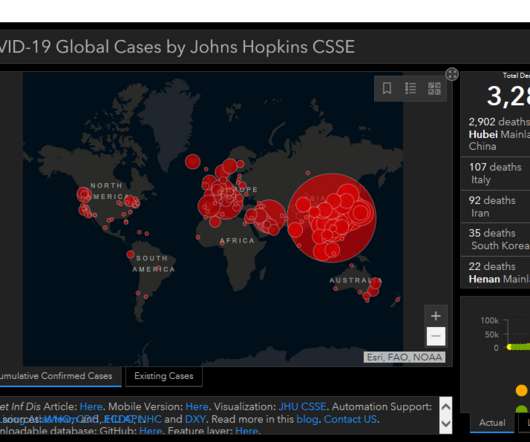
Security Affairs
MARCH 14, 2020
A cyber attack hit one of the major COVID-19 testing laboratories in Czech, the Brno University Hospital in the city of Brno. While the Coronavirus (COVID-19) is spreading on a global scale, crooks and nation-state actors are launching Coronavirus-themed attacks against targets worldwide. The healthcare systems of any country are under pressure, for this reason, the news of a cyberattack against a hospital is regrettable.

Security Affairs
MARCH 10, 2020
Today Microsoft accidentally leaked info about a new wormable vulnerability (CVE-2020-0796) in the Microsoft Server Message Block (SMB) protocol. Today Microsoft accidentally leaked info on a security update for a wormable vulnerability in the Microsoft Server Message Block (SMB) protocol. The issue, tracked as CVE-2020-0796 , is pre- remote code execution vulnerability that resides in the Server Message Block 3.0 (SMBv3) network communication protocol, the IT giant will not address the issue a
Let's personalize your content