7 Steps to Take Right Now to Prepare for Cyberattacks by Russia
Dark Reading
FEBRUARY 25, 2022
A lot of the recommended preparation involves measures organizations should have in place already.

Dark Reading
FEBRUARY 25, 2022
A lot of the recommended preparation involves measures organizations should have in place already.

Krebs on Security
FEBRUARY 3, 2022
If you received a link to LinkedIn.com via email, SMS or instant message, would you click it? Spammers, phishers and other ne’er-do-wells are hoping you will, because they’ve long taken advantage of a marketing feature on the business networking site which lets them create a LinkedIn.com link that bounces your browser to other websites, such as phishing pages that mimic top online brands (but chiefly Linkedin’s parent firm Microsoft ).
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
FEBRUARY 14, 2022
Which topics should CEOs, CIOs and CISOs have on their radar when it comes to Identity and Access Management ( IAM ) and cyber security risks in 2022? Related: How IAM authenticates users. Here are a few important issues that relate to the changes in today’s working environment. Reduce manual processes. Automation can help get rid of manual processes.

Security Affairs
FEBRUARY 24, 2022
US and UK cybersecurity agencies provided details of a new malware used by Iran-linked MuddyWater APT. CISA, the FBI, the US Cyber Command’s Cyber National Mission Force (CNMF), UK’s National Cyber Security Centre (NCSC-UK), and the NSA, and law enforcement agencies have published a joint advisory on new malware used by Iran-linked MuddyWater APT group (aka SeedWorm and TEMP.Zagros ) in attacks aimed at critical infrastructure worldwide.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

WIRED Threat Level
FEBRUARY 2, 2022
Disappointed with the lack of US response to the Hermit Kingdom's attacks against US security researchers, one hacker took matters into his own hands.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Schneier on Security
FEBRUARY 9, 2022
Researchers have calculated the quantum computer size necessary to break 256-bit elliptic curve public-key cryptography: Finally, we calculate the number of physical qubits required to break the 256-bit elliptic curve encryption of keys in the Bitcoin network within the small available time frame in which it would actually pose a threat to do so. It would require 317 × 10 6 physical qubits to break the encryption within one hour using the surface code, a code cycle time of 1 μ s, a reaction

Krebs on Security
FEBRUARY 22, 2022
Missouri Governor Mike Parson made headlines last year when he vowed to criminally prosecute a journalist for reporting a security flaw in a state website that exposed personal information of more than 100,000 teachers. But Missouri prosecutors now say they will not pursue charges following revelations that the data had been exposed since 2011 — two years after responsibility for securing the state’s IT systems was centralized within Parson’s own Office of Administration.

The Last Watchdog
FEBRUARY 28, 2022
One could make the argument that Application Programming Interfaces — APIs – are a vital cornerstone of digital transformation. Related: How a dynamic WAF can help protect SMBs. APIs interconnect the underlying components of modern digital services in a very flexible, open way. This has resulted in astounding innovations in cloud services, mobile computing, IoT systems and agile software development.

Security Affairs
FEBRUARY 19, 2022
The U.S. CISA has created a list of free cybersecurity tools and services that can help organizations increase their resilience. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) announced this week that it has compiled a list of free cybersecurity tools and services that can help organizations to reduce cybersecurity risk and increase resilience.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

WIRED Threat Level
FEBRUARY 9, 2022
A couple allegedly used a “laundry list” of technical measures to cover their tracks. They didn’t work.

Jamf
FEBRUARY 11, 2022
The remediation for a serious security vulnerability in Microsoft Active Directory (AD) prevents Apple macOS from binding. Affected machines will lose the ability to communicate with AD domain controllers, resulting in user lockout and potential data loss.

eSecurity Planet
FEBRUARY 11, 2022
Risk management is a concept that has been around as long as companies have had assets to protect. The simplest example may be insurance. Life, health, auto, and other insurance are all designed to help a person protect against losses. Risk management also extends to physical devices, such as doors and locks to protect homes and vehicles, vaults to protect money and precious jewels, and police, fire, and CCTV to protect against other physical risks.

Krebs on Security
FEBRUARY 16, 2022
A network intrusion at the International Committee for the Red Cross (ICRC) in January led to the theft of personal information on more than 500,000 people receiving assistance from the group. KrebsOnSecurity has learned that the email address used by a cybercriminal actor who offered to sell the stolen ICRC data also was used to register multiple domain names the FBI says are tied to a sprawling media influence operation originating from Iran.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

The Last Watchdog
FEBRUARY 8, 2022
Today’s operating system battleground has long been defined by the warfare between the top three players—Microsoft’s Windows, Google’s Android, and Apple’s iOS. Related: Co ok vs. Zuckerberg on privacy. While each of them has its distinguishing features, Apple’s privacy and security are what makes it the typical enterprise’s pick.
Security Affairs
FEBRUARY 17, 2022
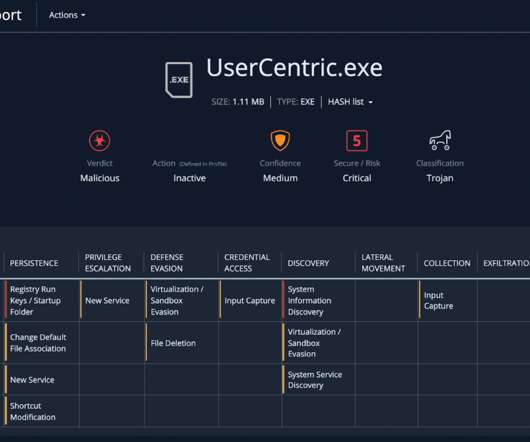
Attackers compromise Microsoft Teams accounts to attach malicious executables to chat and spread them to participants in the conversation. While the popularity of Microsoft Teams continues to grow, with roughly 270 million monthly active users , threat actors started using it as an attack vector. Starting in January 2022, security researchers from Avanan observed attackers compromising Microsoft Teams accounts attach malicious executables to chat and infect participants in the conversation.

WIRED Threat Level
FEBRUARY 23, 2022
Western intelligence services are raising alarms about Cyclops Blink, the latest tool at the notorious group’s disposal.

Jamf
FEBRUARY 15, 2022
Learn how the partnership between Jamf Pro and Google BeyondCorp enables you to construct a compliance and security framework around end-user devices, blending Jamf’s device management with Google’s endpoint management security for a comprehensive, cloud-based, Zero Trust solution.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

eSecurity Planet
FEBRUARY 4, 2022
Malware is one of the biggest threats businesses face, and with nearly a third of all malware coming through the internet and email, businesses and consumers alike need ways to protect themselves. The best internet security software comes in several different forms, giving businesses all of the protection they need to identify and stop malware before it causes bigger problems.

Krebs on Security
FEBRUARY 22, 2022
The U.S. Internal Revenue Service (IRS) said Monday that taxpayers are no longer required to provide facial scans to create an account online at irs.gov. In lieu of providing biometric data, taxpayers can now opt for a live video interview with ID.me , the privately-held Virginia company that runs the agency’s identity proofing system. The IRS also said any biometric data already shared with ID.me would be permanently deleted over the next few weeks, and any biometric data provided for new

The Last Watchdog
FEBRUARY 3, 2022
I currently have over 450 accounts that use passwords combined with a variety of two-factor authentication methods. Related: How the Fido Alliance enables password-less authentication. I don’t know every password; indeed, each password is long, complex and unique. In effect, my passwords are now “keys” — and I must authenticate across many accounts, multiple times per day, on a variety of device platforms.
Security Affairs
FEBRUARY 28, 2022
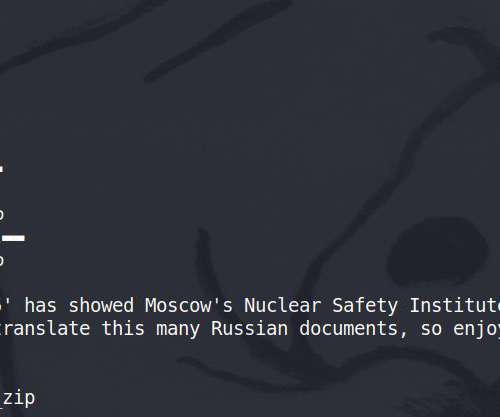
Anonymous and other hacker groups that responded to the call to war against Russia continue to launch cyberattacks on gov organizations and businesses. Anonymous and numerous hacker groups linked to the popular collective continue to launch cyber attacks against Russian and Belarussian government organizations and private businesses. In the last few days massive DDoS attacks have taken offline numerous websites of Russian government entities, including the Duma and Ministry of Defense.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

WIRED Threat Level
FEBRUARY 8, 2022
As Russia continues to amass troops at the border, resistance groups have seen a surge in crypto donations.

Schneier on Security
FEBRUARY 4, 2022
Senators have reintroduced the EARN IT Act, requiring social media companies (among others) to administer a massive surveillance operation on their users: A group of lawmakers led by Sen. Richard Blumenthal (D-CT) and Sen. Lindsey Graham (R-SC) have re-introduced the EARN IT Act , an incredibly unpopular bill from 2020 that was dropped in the face of overwhelming opposition.

IT Governance
FEBRUARY 15, 2022
Everybody wants to know what the future holds. Those who are a step ahead of the rest can foresee challenges and avoid falling into pitfalls, or they can spot opportunities and ride to success. This is as true in the cyber security landscape as it is in any other. But predictions are difficult. After all, who at the start of 2020 could have foreseen what the next two years would be like?
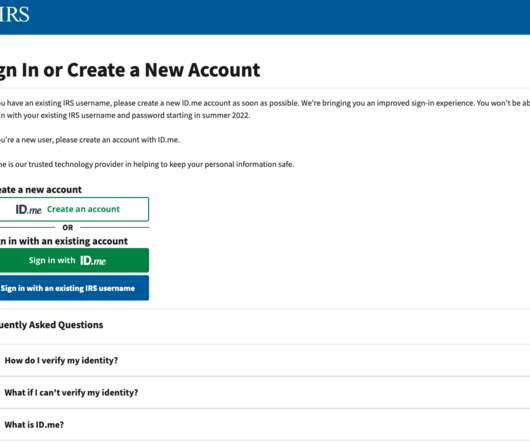
Krebs on Security
FEBRUARY 7, 2022
The Internal Revenue Service (IRS) said today it will be transitioning away from requiring biometric data from taxpayers who wish to access their records at the agency’s website. The reversal comes as privacy experts and lawmakers have been pushing the IRS and other federal agencies to find less intrusive methods for validating one’s identity with the U.S. government online.

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

The Last Watchdog
FEBRUARY 7, 2022
When new vulnerabilities re announced or flaws are discovered in public or “off the shelf” applications, several things happen. News spreads of the risks while attackers and security professionals alike begin searching for potential attack targets for the purpose of exploiting or protecting them. Related: How GraphQLs expanded the attack surface. When Log4Shell first hit the street, we immediately saw attacks against almost every one of our customers.

Security Affairs
FEBRUARY 11, 2022
The U.S. CISA has added to the catalog of vulnerabilities another 15 security vulnerabilities actively exploited in the wild. The US Cybersecurity & Infrastructure Security Agency (CISA) has added fifteen more flaws to the Known Exploited Vulnerabilities Catalog. The ‘ Known Exploited Vulnerabilities Catalog ‘ is a list of known vulnerabilities that threat actors have abused in attacks and that are required to be addressed by Federal Civilian Executive Branch (FCEB) agencies.

WIRED Threat Level
FEBRUARY 27, 2022
The country has enlisted thousands of cybersecurity professionals in the war effort against Russia.
Let's personalize your content