Global Cyber Agencies Unveil New Logging Standards
Data Breach Today
AUGUST 22, 2024
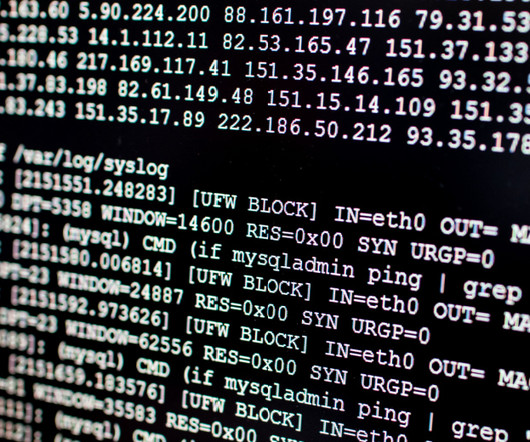
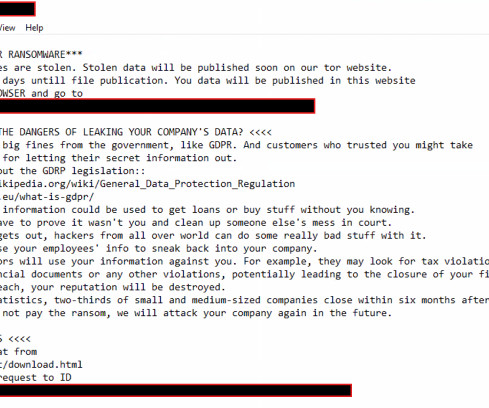
Logging Best Practices Guidance Aims to Enhance Global Detection and Response The Australian Signals Directorate's Australian Cyber Security Center released joint guidance with a cohort of international cyber agencies that aims to provide baseline standards for event logging and threat detection, amid a wave of high-profile attacks employing "living off the land" techniques.




































Let's personalize your content