Microsoft Finds Backdoor, CISA Warns of New Attack Vectors
Data Breach Today
DECEMBER 17, 2020
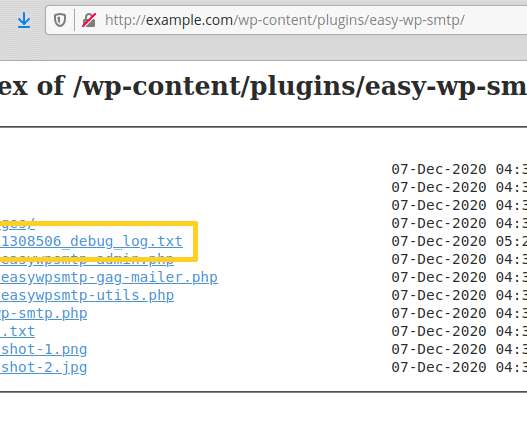
Devastating Scope of Hacking Campaign Expands Microsoft says on Thursday it has removed malware related to an expansive hacking campaign that has ensnared thousands of organizations and U.S. government agencies. Meanwhile, CISA warns the SolarWinds Orion supply chain compromise may not be the only infection vector.



































Let's personalize your content