A CISO's Security Predictions for 2020
Data Breach Today
DECEMBER 31, 2019
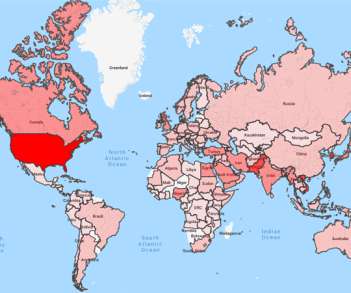
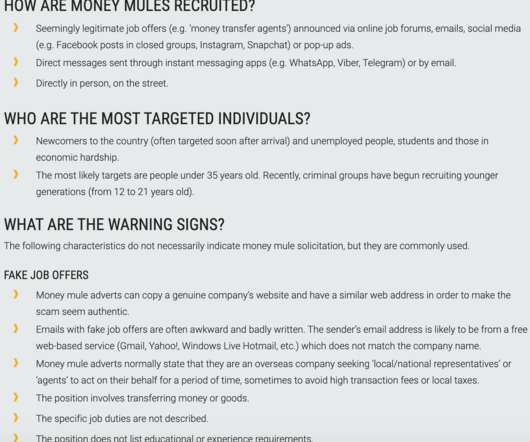
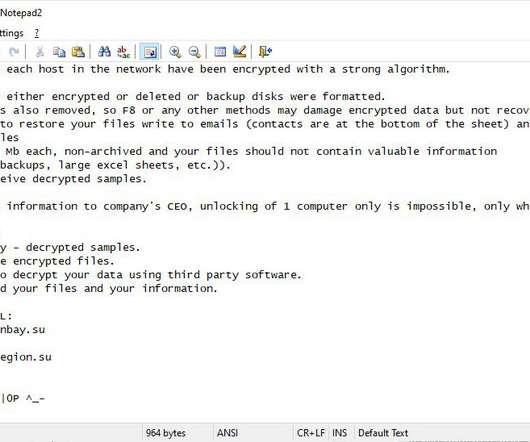
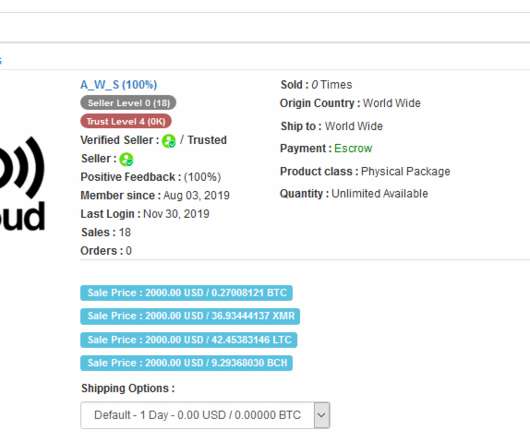
As Threats Continue to Evolve, So too Must Defenses The cybersecurity outlook for 2020 and the new decade will be characterized by more advanced, targeted and coordinated attack vectors designed to exploit the cybersecurity skills shortage, along with congenitally poor security fundamentals and hygiene.


































Let's personalize your content