Experts: Federal Privacy Law Needed to Curb AI Data Misuse
Data Breach Today
JULY 11, 2024
New Bill Would Create Data Minimization Measures, Express Permission Requirements Experts warned in congressional testimony to the Senate Commerce Committee on Thursday that the absence of a comprehensive privacy bill in the United States is hindering economic competition for technology companies and jeopardizing the privacy of the American public.
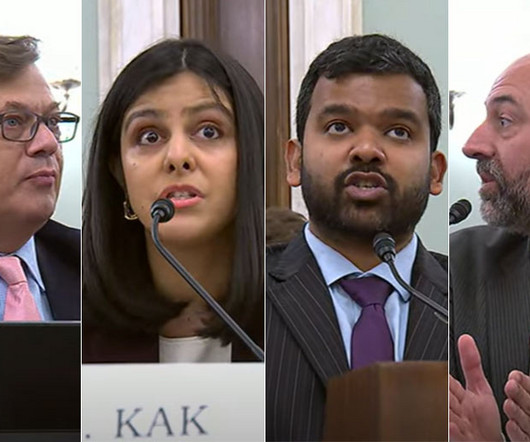








































Let's personalize your content