Can AI supercharge creativity without stealing from artists?
Collaboration 2.0
MARCH 12, 2025
The relationship between generative AI and artists has been predatory so far. Can AI companies change to support creators and enrich the ecosystem?
Collaboration 2.0
MARCH 12, 2025
The relationship between generative AI and artists has been predatory so far. Can AI companies change to support creators and enrich the ecosystem?

WIRED Threat Level
MARCH 12, 2025
No Lives Matter has emerged in recent months as a particularly violent splinter group within the extremist crime network known as Com and 764, and experts are at a loss for how to stop its spread.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Collaboration 2.0
MARCH 12, 2025
The two biggest corporate open-source foundations are merging.

Security Affairs
MARCH 12, 2025
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds six Microsoft Windowsflaws to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the following vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog : CVE-2025-24983 Microsoft Windows Win32k Use-After-Free Vulnerability CVE-2025-24984 Microsoft Windows NTFS Information Disclosure Vulnerability CVE-2025-24985 Microsoft Windows Fast FAT File System Drive

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

Collaboration 2.0
MARCH 12, 2025
Follow the 'I'm not a robot' CAPTCHA, and you might just end up with malware on your PC.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Collaboration 2.0
MARCH 12, 2025
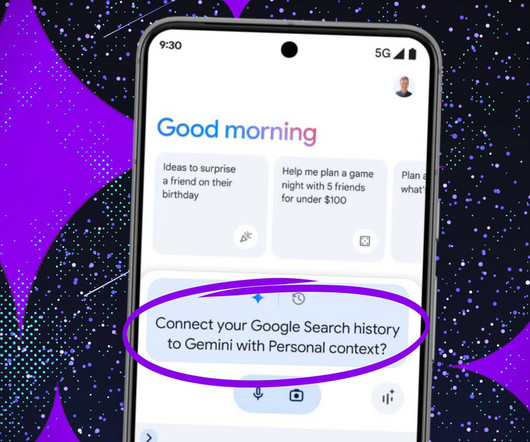
Is a more personalized AI experience worth Gemini seeing everything you've Googled?

Data Breach Today
MARCH 12, 2025
Series D Funding to Drive U.S. Growth and AI Advancements in Cybersecurity Pentera has raised $60 million in Series D funding to expand its presence in the U.S. and accelerate AI-driven innovations in security validation. CEO Amitai Ratzon says the company is focused on advancing automated testing and strengthening its leadership in exposure validation.

Collaboration 2.0
MARCH 12, 2025
The M4 Max Mac Studio is a compact powerhouse that seamlessly fits on my desk - and outperforms my PC tower in several ways.

Data Breach Today
MARCH 12, 2025
Move to Fold PSR Into Financial Conduct Authority Could Affect Fraud Victims The U.K. government late Tuesday abolished its Payment Systems Regulator, a move aimed at reducing business complexity and supporting the Labour government's economic growth agenda. Payment system firms had complained that they had to deal with three different regulators.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Collaboration 2.0
MARCH 12, 2025
Chipolo's One and Card trackers are perfect for anyone who often misplaces their keys or wallet.

Data Breach Today
MARCH 12, 2025
Bipartisan 'Match IT Act' Aims to Reduce Risk of Medical Mistakes, Privacy Mishaps Two Congressmen are taking another bipartisan stab at passing legislation aimed at improving patient identity matching to help reduce mistakes that put patient privacy and safety at risk. The lawmakers have introduced similar provisions in the past. Will the proposals gain traction this time?

Collaboration 2.0
MARCH 12, 2025
The Planck SSD is a handy USB-C accessory that gives any device additional storage, especially if you need it for content creation.

Data Breach Today
MARCH 12, 2025
Browser Isolation Protects Access Points as Remote Work Expands Attack Surface With 92% of organizations supporting remote connectivity and phishing attacks surging to record levels, browser-based security has become essential for zero trust frameworks to protect against malware, ransomware and credential theft.

Advertiser: ZoomInfo
Incorporating generative AI (gen AI) into your sales process can speed up your wins through improved efficiency, personalized customer interactions, and better informed decision- making. Gen AI is a game changer for busy salespeople and can reduce time-consuming tasks, such as customer research, note-taking, and writing emails, and provide insightful data analysis and recommendations.

Collaboration 2.0
MARCH 12, 2025
If your internal drive is running out of space, expand your storage effortlessly with a few SSDs and this convenient Sabrent docking station.

Data Breach Today
MARCH 12, 2025
AI-Enabled Security Offers Continuous Monitoring for Distributed Enterprise Apps As cybercriminals increasingly use AI for sophisticated attacks against cloud workloads, organizations must implement zero trust principles with continuous policy enforcement and proactive threat management to protect mission-critical applications.

Collaboration 2.0
MARCH 12, 2025
You're paying good money for chatbots that return wrong answers with 'alarming confidence,' according to a new report.

Data Breach Today
MARCH 12, 2025
Tested on Three OpenAI Models, 'Minja' Has High Injection and Attack Rates A memory injection attack dubbed Minja turns AI chatbots into unwitting agents of misinformation, requiring no hacking and just a little clever prompting. The exploit allows attackers to poison an AI model's memory with deceptive information, potentially altering its responses for all users.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Collaboration 2.0
MARCH 12, 2025
Google says it's found a sweet spot between power and efficiency by employing the 'distillation' of neural nets.

Data Breach Today
MARCH 12, 2025
Juniper Networks Urges Immediate Updating and Malware Scans to Block Attackers Hackers have been infecting outdated Juniper MX routers with backdoor malware as part of an apparent cyberespionage campaign that traces to a Chinese-affiliated hacking team tracked as UNC 3886, warned Google's Mandiant incident response group.

Collaboration 2.0
MARCH 12, 2025
Solar generators are trending, but what happens when the sky turns gray? This device keeps your power running.
The Last Watchdog
MARCH 12, 2025
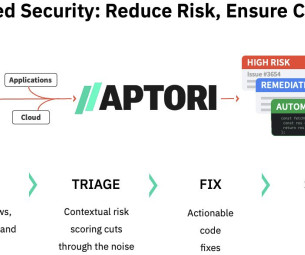
San Jose, Calif., Mar. 12, 2025, CyberNewswire — Aptori , a leader in AI-driven application security, today announced the launch of its AI-driven AppSec Platform on Google Cloud Marketplace as part of graduating from Google Clouds ISV Startup Springboard program. This new agentic AI solution leverages semantic reasoning to analyze application code and logic in real time, delivering deterministic vulnerability detection, contextual risk prioritization, and automated remediation.

Advertiser: ZoomInfo
In today’s ultra-competitive markets, it’s no longer enough to wait for buyers to show obvious signs of interest. Instead, sales teams must be proactive, identifying and acting on nuanced buyer behaviors — often before prospects are fully ready to make a purchase. In this eBook from ZoomInfo & Sell Better, learn 10 actionable ways to use these buyer signals to transform your sales strategy and close deals faster.

Collaboration 2.0
MARCH 12, 2025
I've always appreciated these simple accessories, and this new feature makes them more useful than ever.

KnowBe4
MARCH 12, 2025
Artificial Intelligence (AI) is no longer just a toolit is a game changer in our lives, our work as well as in both cybersecurity and cybercrime.
Collaboration 2.0
MARCH 12, 2025
Blurry images, slow loads, and constant freezes are haunting some users.

KnowBe4
MARCH 12, 2025
Microsoft warns that a widespread malvertising campaign hit nearly one million devices around the world. The campaign, which began on illegal streaming sites, impacted both consumer and enterprise devices across a wide range of industries.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Collaboration 2.0
MARCH 12, 2025
We've gone hands-on with dozens of iPhone accessories. From MagSafe gear to screen protectors, these are our favorites of 2025 so far.

Thales Cloud Protection & Licensing
MARCH 12, 2025
Breaking the Barriers to a Password-Free Life in Enterprise: Meet SafeNet eToken Fusion NFC PIV security key madhav Thu, 03/13/2025 - 06:46 As large organizations increasingly shift towards passwordless solutions, the benefits are clear: enhanced user experience, improved security, and significant cost savings. The FIDO (Fast Identity Online) standard has emerged as the gold standard in authentication technology, providing a robust framework for secure and convenient access.
Collaboration 2.0
MARCH 12, 2025
This update also re-enables Apple Intelligence for those who previously had turned off this feature. Here's how to fix that, too.
Let's personalize your content