Suspected Nation-State Actors Target US Aerospace Industry
Data Breach Today
JUNE 7, 2023
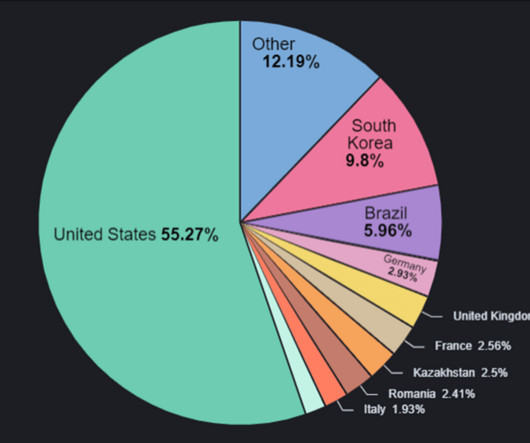
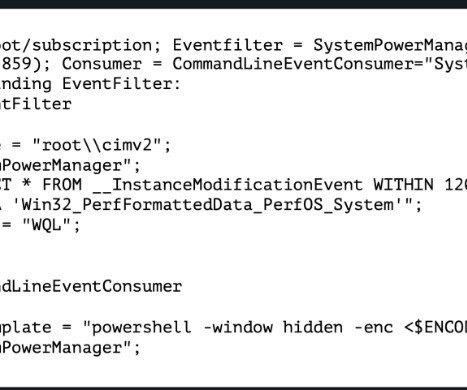
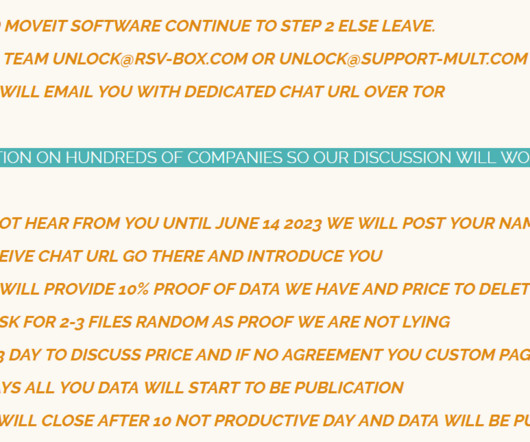
PowerDrop Malware Simple But Sophisticated Suspected nation-state hackers are using that malware researchers say straddles between the line between off-the-shelf and advanced tactics in order to target the U.S. aerospace industry. Researchers from Adlumin in May found the malware on a defense contractor's network.






































Let's personalize your content