CISA Urges Software Developers to Prioritize Memory Safe Coding
Data Breach Today
DECEMBER 6, 2023
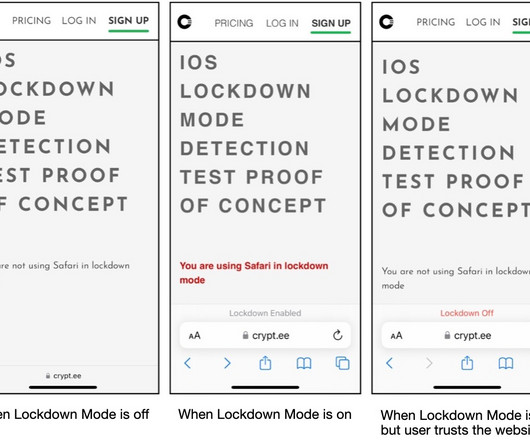
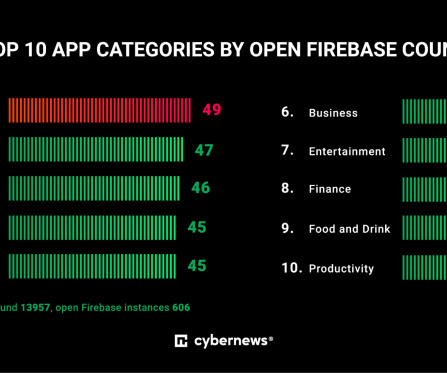
CISA, NSA, FBI and Global Partners Urge Manufacturers to Make Memory Safe Road Maps The U.S. Cybersecurity and Infrastructure Security Agency is urging software developers to implement memory safe coding as part of an effort to address critical vulnerabilities in programming languages and further shift security responsibilities away from end users.




































Let's personalize your content