Discord Admins Hacked by Malicious Bookmarks
Krebs on Security
MAY 30, 2023
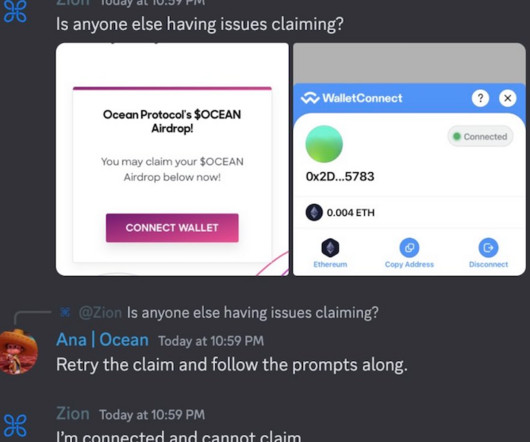
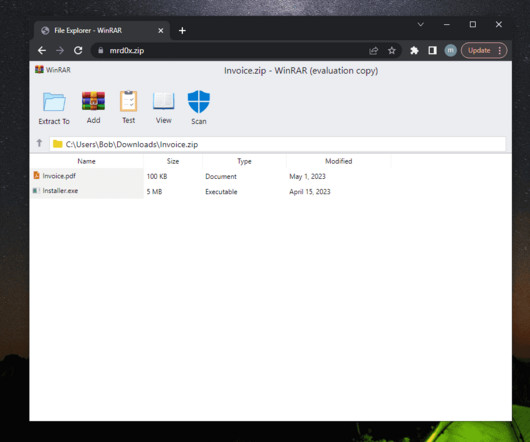
A number of Discord communities focused on cryptocurrency have been hacked this past month after their administrators were tricked into running malicious Javascript code disguised as a Web browser bookmark. This attack involves malicious Javascript that is added to one’s browser by dragging a component from a web page to one’s browser bookmarks.








































Let's personalize your content