Millions of Patients Affected in Double-Extortion Attack
Data Breach Today
DECEMBER 22, 2023
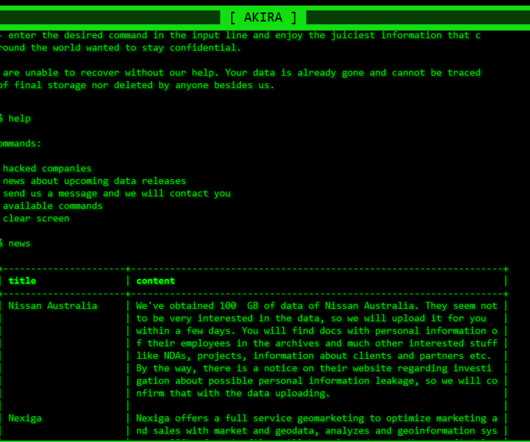
Hackers Crippled Systems, Stole Patient Data From ESO Solutions Hackers carried out a double-extortion ransomware attack on medical software company ESO Solutions, exposing personal details and healthcare information of 2.7 million U.S. patients and encrypting some of the company's systems. Double-extortion attacks also exfiltrate data.





























Let's personalize your content