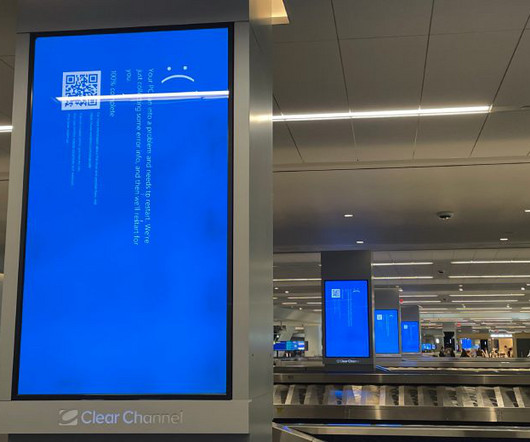
CrowdStrike Disruption Restoration Is Taking Time
Data Breach Today
JULY 22, 2024
Microsoft's Tool Requires Physical Access, a 'Time-Consuming and Laborious Task' Microsoft's statement that a faulty CrowdStrike update affected less than 1% of active Windows systems doesn't tell the full story, since large organizations in critical sectors make up a disproportionate part of the user base, as the outages in healthcare, transportation and banking demonstrate.








































Let's personalize your content