Ransomware Groups' Latest Tactic: Weaponized Marketing
Data Breach Today
DECEMBER 13, 2023
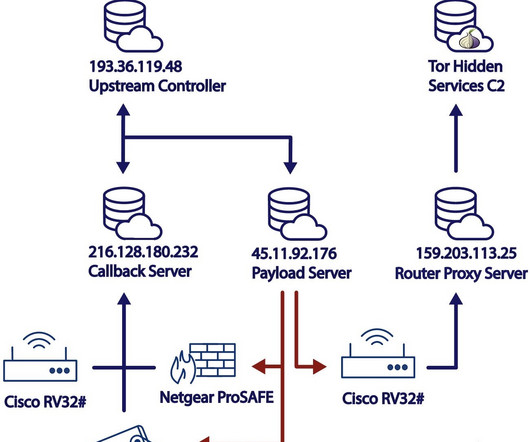
'Oxygen of Publicity' Helps Intimidate Victims and Recruit Affiliates, Experts Warn Seeking to maximize profits no matter the cost, ransomware groups have been bolstering their technical prowess and psychological shakedowns with a fresh strategy: attempting to control the narrative. Experts are warning security researchers and journalists to beware being co-opted.








































Let's personalize your content