How to start using the new Linux terminal on your Android device
Collaboration 2.0
APRIL 8, 2025
Google just added a powerful new feature to Android: The Linux terminal. It's easier than you think to use and it unlocks a whole new level of control.

Collaboration 2.0
APRIL 8, 2025
Google just added a powerful new feature to Android: The Linux terminal. It's easier than you think to use and it unlocks a whole new level of control.

Data Breach Today
APRIL 8, 2025
Independent Tribunal Rules That at Least 'Bare Details' of Case Can Be Made Public The British government has lost its bid to maintain "absolute" secrecy over its attempt to compel Apple to provide backdoor access to users' encrypted data, ruled Britain's independent Investigatory Powers Tribunal. Whether any further details will get released publicly remains unclear.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Collaboration 2.0
APRIL 8, 2025
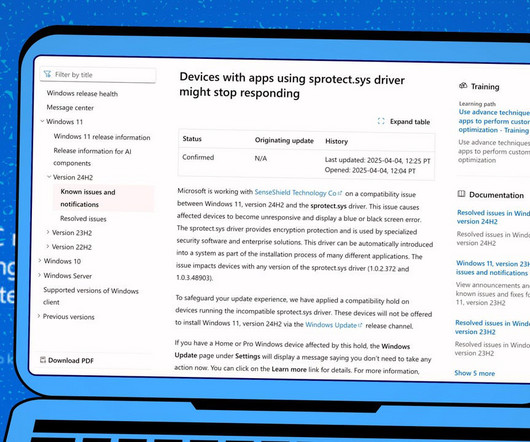
Microsoft is working on a fix, but here's what you can do if you get a BSOD in the meantime.

Data Breach Today
APRIL 8, 2025
Zero Trust Network Access Firm Plans to Enhance Platform and Grow Revenue Faster Tailscale has landed $160 million in Series C funding to scale its platform and meet growing demand from AI and enterprise firms. The networking company will invest in engineering to support multi-cloud and identity-based networking features.

Speaker: Frank Taliano
Document-heavy workflows slow down productivity, bury institutional knowledge, and drain resources. But with the right AI implementation, these inefficiencies become opportunities for transformation. So how do you identify where to start and how to succeed? Learn how to develop a clear, practical roadmap for leveraging AI to streamline processes, automate knowledge work, and unlock real operational gains.

Collaboration 2.0
APRIL 8, 2025
Motorola's latest handset may look identical to the Moto G, but under the surface lies more impressive yet affordable power.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Collaboration 2.0
APRIL 8, 2025
If you're looking for headphones with sonic clarity and brilliant EQ, the Dali IO-8 are an audiophile's dream.

Data Breach Today
APRIL 8, 2025
University of Maryland Medical Center Said FBI Is Also Investigating Case An academic medical center is facing a class action lawsuit alleging one of its pharmacists installed keylogging software on 400 computers over a decade to spy on the personal lives and intimate moments of coworkers. The pharmacist is also facing a criminal investigation, the hospital said.

Collaboration 2.0
APRIL 8, 2025
With this free utility, you can upgrade from Windows 10 - or install Windows 11 on a clean PC - without bumping into Microsoft's onerous requirements. Here's how.

Data Breach Today
APRIL 8, 2025
Espionage Campaign Mainly Targeted European Organizations A Russian nation state threat actor exploited "lesser known" features of Microsoft Windows remote desktop protocol to target European organizations for espionage. Hackers using RDP to deploy a malicious application and access data from victims.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Collaboration 2.0
APRIL 8, 2025
Want to know which AI tools businesses and creators are flocking to? Here's 2025's ZDNET Index of AI Tool Popularity and how ChatGPT, Canva, Gemini, Copilot, and more stack up in market share.

Data Breach Today
APRIL 8, 2025
AI Leaders Call for Proactive US Response Amid Chinese Technology Breakthroughs The United States risks losing the so-called "AI Cold War" against China unless it abandons traditional containment strategies and adapts to Beijing's advances, panelists told lawmakers Tuesday. "I'm as stunned as all of you about just how fast China has caught up," said Adam Thierer.

Collaboration 2.0
APRIL 8, 2025
If you're hesitant to try GIMP because the UI looks so different from Photoshop, you're in luck because there's an easy way to transform the interface.

Data Breach Today
APRIL 8, 2025
Llama 4 Scout and Maverick Face Scrutiny Over Benchmarking Practices Meta released two new open-weight large language models, dubbed Llama 4 Scout and Llama 4 Maverick, that aim to scale AI performance while lowering compute costs. Their debut drew criticism over how the company presented benchmark results.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

Collaboration 2.0
APRIL 8, 2025
Even in 2025, Sony's Bravia X90L stands out as one of the best-performing TVs in its price range. These new Best Buy deals make larger sizes more accessible.

AIIM
APRIL 8, 2025
The buzz from the inaugural AI+IM Global Summit is still resonating through the AIIM community, with one topic dominating conversations: agentic AI.

Collaboration 2.0
APRIL 8, 2025
Leaning into his decades of tech innovation, one of the 'fathers of the internet' delivers an action list of leadership lessons.

KnowBe4
APRIL 8, 2025
CyberheistNews Vol 15 #14 [Heads Up] QR Code Phishing is Getting More Stealthy Fast

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

Collaboration 2.0
APRIL 8, 2025
Stop wasting time on repetitive tasks, and let bash scripts do the work for you.

Security Affairs
APRIL 8, 2025
WhatsApp addressed a flaw, tracked as CVE-2025-30401, that could allow attackers to trick users and enable remote code execution. WhatsApp released a security update to address a vulnerability, tracked as CVE-2025-30401, that could let attackers trick users and enable remote code execution. The spoofing flaw impacts WhatsApp for Windows before version 2.2450.6.

Collaboration 2.0
APRIL 8, 2025
How good can an Amazon Basics multitool be? For most people. it's nearly perfect.

Security Affairs
APRIL 8, 2025
Google addressed 62 vulnerabilities with the release of Android ‘s April 2025 security update, including two actively exploited zero-days. Google released Android ‘s April 2025 security updates to address 62 vulnerabilities, including two zero-day vulnerabilities ( CVE-2024-53197 , CVE-2024-53150 ) exploited in targeted attacks. The vulnerability CVE-2024-53197 is a Linux kernel issue affecting ALSA USB audio.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Collaboration 2.0
APRIL 8, 2025
With its massive battery and a range of extra features, the Blackview BV7300 smartphone is built for camping, exploring, and all kinds of outdoor adventures.

Security Affairs
APRIL 8, 2025
The Tor leak site of the Everest ransomware group went offline after being hacked and defaced over the weekend. The Everest ransomware gangs darknet site went offline after being hacked and defaced, with victim listings replaced by the following message. Dont do crime CRIME IS BAD xoxo from Prague read the message published on the site’s homepage after the defacement.

Collaboration 2.0
APRIL 8, 2025
Often referred to as the 'soap opera effect,' motion smoothing can enhance gaming and live sports but tends to be distracting for everything else. Here's how to turn it off.

Krebs on Security
APRIL 8, 2025
Microsoft today released updates to plug at least 121 security holes in its Windows operating systems and software, including one vulnerability that is already being exploited in the wild. Eleven of those flaws earned Microsoft’s most-dire “critical” rating, meaning malware or malcontents could exploit them with little to no interaction from Windows users.

Speaker: Yohan Lobo and Dennis Street
In the accounting world, staying ahead means embracing the tools that allow you to work smarter, not harder. Outdated processes and disconnected systems can hold your organization back, but the right technologies can help you streamline operations, boost productivity, and improve client delivery. Dive into the strategies and innovations transforming accounting practices.

Collaboration 2.0
APRIL 8, 2025
The JBL Tour Pro 3 features excellent sound and a marathon battery life. These earbuds are currently $50 off.

Data Matters
APRIL 8, 2025
For Swiss companies, the next six months are critical for preparing to meet new Digital Data Law obligations. In this briefing, we outline the key timelines, compliance requirements, and practical steps to align with EU requirements. The post Meeting EU Data, Cybersecurity, and Artificial Intelligence Law Obligations: A Checklist for Swiss Life Sciences Companies appeared first on Data Matters Privacy Blog.

Collaboration 2.0
APRIL 8, 2025
I learned the hard way that delaying software updates isn't worth the risk. Learn from my mistakes - before it's too late.
Let's personalize your content