LockBit 3.0 Claims Attack on Australian Auto Dealer Eagers
Data Breach Today
JANUARY 2, 2024
Eagers Says It Doesn't Know Full Extent of Hack But Has Started Contacting Victims Brisbane-based retail group Eagers Automotive is investigating a cyberattack that disrupted parts of its regional operations and compromised the personal information of some of its customers. Eagers said Tuesday it doesn't know the full extent of the hack, but it has started notifying customers.









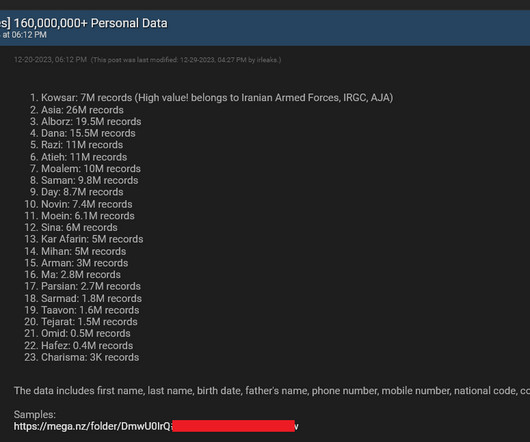




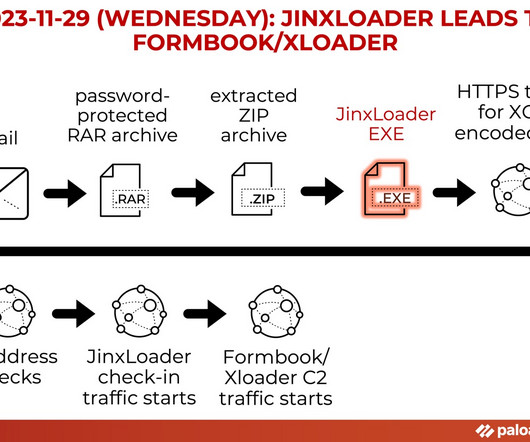

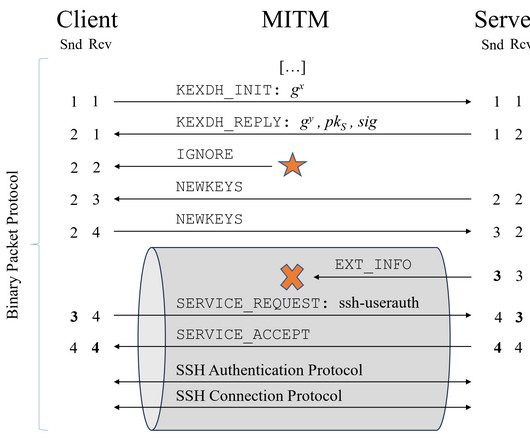






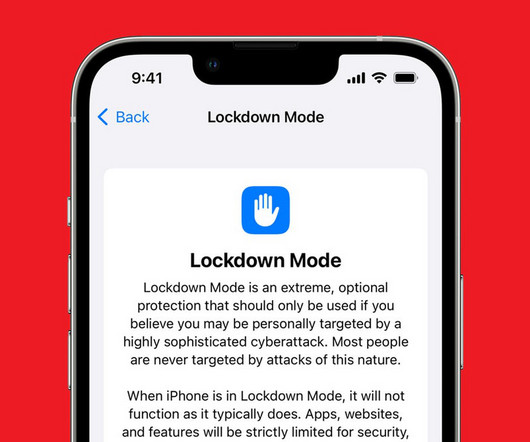












Let's personalize your content