Moody's: Hackers Aim for Big Payouts, Supply Chain Attacks
Data Breach Today
DECEMBER 9, 2024
Security Affairs
DECEMBER 9, 2024
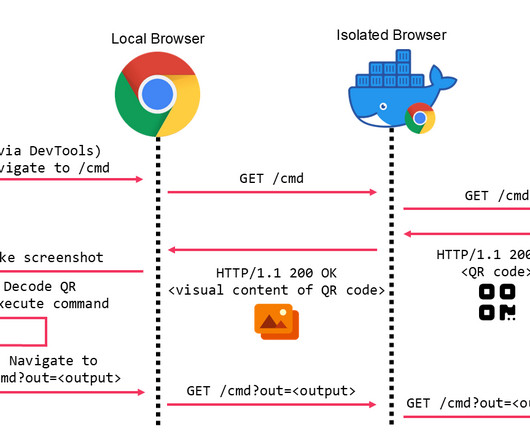
Mandiant revealed a technique to bypass browser isolation using QR codes, enabling command transmission from C2 servers. Browser isolation is a security measure that separates web browsing from the user’s device by running the browser in a secure environment (e.g., cloud or VM) and streaming visuals. Mandiant has identified a new technique for bypassing browser isolation technology and using QR codes to send commands from C2 to compromised devices.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
DECEMBER 9, 2024
Luigi Mangione, a 26-year-old graduate of the University of Pennsylvania, was apprehended on Monday after visiting a McDonald's in Altoona, Pennsylvania.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

The Last Watchdog
DECEMBER 9, 2024
The Amazon Web Services (AWS) Shared Responsibility Model has come a long way, indeed. Related: Shared Responsibility best practices In 2013, Amazon planted a stake in the ground when it divided cloud security obligations between AWS and its patrons, guaranteeing the integrity of its infrastructure, but placing a huge burden on customers to secure things on their end.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

KnowBe4
DECEMBER 9, 2024
Check out the November updates in Compliance Plus so you can stay on top of featured compliance training content.

Collaboration 2.0
DECEMBER 9, 2024

Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

Security Affairs
DECEMBER 9, 2024
Romanian energy supplier Electrica Group is investigating an ongoing ransomware attack impacting its operations. Romanian energy supplier Electrica Group suffered a cyber attack that is impacting its operations. The company assured investors that the attack hadn’t affected its critical systems, but temporary disruptions in customer services might occur due to enhanced security protocols.

Collaboration 2.0
DECEMBER 9, 2024

erwin
DECEMBER 9, 2024
When it comes to using AI and machine learning across your organization, there are many good reasons to provide your data and analytics community with an intelligent data foundation. For instance, Large Language Models (LLMs) are known to ultimately perform better when data is structured. And being that data is fluid and constantly changing, its very easy for bias, bad data and sensitive information to creep into your AI data pipeline.

Collaboration 2.0
DECEMBER 9, 2024

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Jamf
DECEMBER 9, 2024

OpenText Information Management
DECEMBER 9, 2024
The most wonderful time of the year is upon us, but for banks and financial institutions, the pressure to deliver secure, innovative digital services is a year-round responsibility. As customers demand faster, more seamless banking experiences, the need to "sleigh" the competition with reliable, secure software delivery is crucial. Just like Santa's workshop, the software development lifecycle at banks is a bustling hub of activity.

Collaboration 2.0
DECEMBER 9, 2024

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

OpenText Information Management
DECEMBER 9, 2024
What if your rich media assets werent just files, but your teams secret weapon for speed, creativity and collaboration? What began as a niche tool for libraries and publishers has grown into an essential powerhouse for marketing technology and the beating heart of modern business storytelling. And at the forefront of this digital asset management evolution?

Collaboration 2.0
DECEMBER 9, 2024

Security Affairs
DECEMBER 9, 2024
Deloitte has responded to claims by the Brain Cipher ransomware group, which alleges the theft of over 1 terabyte of the company’s data. Recently, the ransomware group Brain Cipher added Deloitte UK to its Tor leak site. The gang claimed to have stolen one terabyte of compressed data from the company. A Deloitte spokesperson addressed claims made by the ransomware gang, stating that the source of data is a single client’s system, which is not linked to the company’s network.

Collaboration 2.0
DECEMBER 9, 2024

Advertisement
Explore how enterprises can enhance developer productivity and onboarding by adopting self-hosted Cloud Development Environments (CDEs). This whitepaper highlights the simplicity and flexibility of cloud-based development over traditional setups, demonstrating how large teams can leverage economies of scale to boost efficiency and developer satisfaction.

Schneier on Security
DECEMBER 9, 2024
For a technology that seems startling in its modernity, AI sure has a long history. Google Translate, OpenAI chatbots, and Meta AI image generators are built on decades of advancements in linguistics, signal processing, statistics, and other fields going back to the early days of computing—and, often, on seed funding from the U.S. Department of Defense.

Collaboration 2.0
DECEMBER 9, 2024

IT Governance
DECEMBER 9, 2024
Riskbenefit analysis, defence in depth, information security objectives and proportionality Looking to mitigate your information security risks but not sure how to choose effective controls while staying on budget ? Riskbenefit analysis is key, as is defence in depth. You also want to set information security objectives that are aligned to your business objectives , and be proportionate in your control selections.
Let's personalize your content