Hackers Using MOVEit Flaw to Deploy Web Shells, Steal Data
Data Breach Today
JUNE 2, 2023
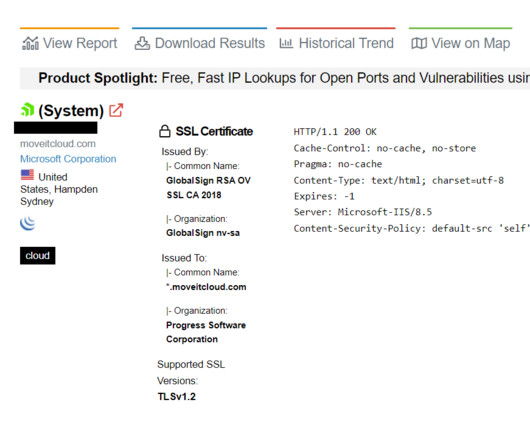
Mandiant Said TTPs of Threat Group Behind Exploiting MOVEit Appear Similar to FIN11 Adversaries have taken advantage of a zero-day vulnerability in Progress Software's managed file transfer product to deploy web shells and steal data, Mandiant found. An unknown threat actor began exploiting the critical SQL injection vulnerability in MOVEit Transfer on May 27.








































Let's personalize your content