Calendar Meeting Links Used to Spread Mac Malware
Krebs on Security
FEBRUARY 28, 2024
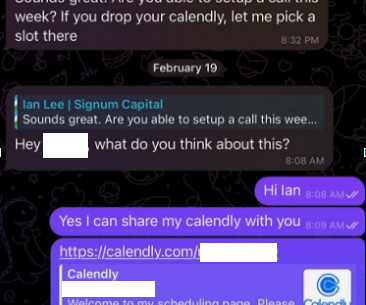
Malicious hackers are targeting people in the cryptocurrency space in attacks that start with a link added to the target’s calendar at Calendly , a popular application for scheduling appointments and meetings. The attackers impersonate established cryptocurrency investors and ask to schedule a video conference call. But clicking the meeting link provided by the scammers prompts the user to run a script that quietly installs malware on macOS systems.









































Let's personalize your content