Buy or gift a Babbel subscription for 74% off right now
Collaboration 2.0
NOVEMBER 10, 2024
Save $449 on a lifetime Babbel Language Learning subscription and learn 14 new languages with this deal.

Collaboration 2.0
NOVEMBER 10, 2024
Save $449 on a lifetime Babbel Language Learning subscription and learn 14 new languages with this deal.

Jamf
NOVEMBER 10, 2024
Learn about modern authentication and what technologies define it. Discover how it helps organizations defend against sophisticated threats while allowing users to stay productive.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Collaboration 2.0
NOVEMBER 10, 2024
This deal gets you a lifetime license to Microsoft Office 2019 for Windows or Mac and access to Microsoft Word, Excel, PowerPoint, and more for 87% off.
The Last Watchdog
NOVEMBER 10, 2024
The Internet of Things is growing apace. Related: The Top 12 IoT protocols Deployment of 5G and AI-enhanced IoT systems is accelerating. This, in turn, is driving up the number of IoT-connected devices in our homes, cities, transportation systems and critical infrastructure. One estimate suggests IoT-connected devices are multiplying at a 12 percent compound annual growth rate.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Collaboration 2.0
NOVEMBER 10, 2024
Not everyone needs a $1,000 phone. If you're on a tight budget, the NUU N10 is an impressive handset that won't break the bank.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Collaboration 2.0
NOVEMBER 10, 2024
When it comes to Bluetooth speakers, small size usually means small sound -- unless it's the JBL Clip 5, which produces surprisingly powerful audio.

Security Affairs
NOVEMBER 10, 2024
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. Mazda Connect flaws allow to hack some Mazda vehicles Veeam Backup & Replication exploit reused in new Frag ransomware attack Texas oilfield supplier Newpark Resources suffered a ransomware attack Palo Alto Networks warns of potential RCE in PAN-OS ma

Collaboration 2.0
NOVEMBER 10, 2024
Get an annual BJ's Wholesale Club membership for 63% off right now to save on groceries, gas, household items, and more.
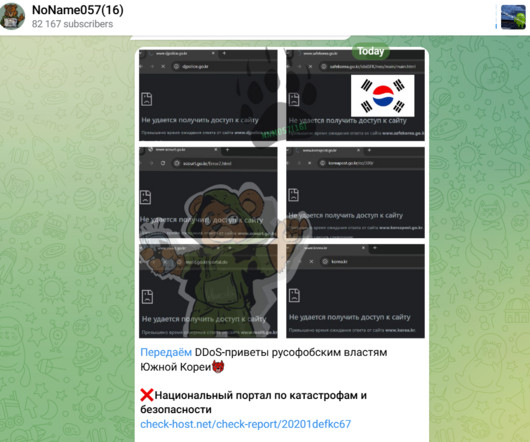
Security Affairs
NOVEMBER 10, 2024
South Korea claims Pro-Russia actors intensified cyberattacks on national sites after it decided to monitor North Korean troops in Ukraine. South Korea’s government blames pro-Russia threat actors for an intensification of cyberattacks on national sites after it decided to monitor North Korean troops in Ukraine. South Korea reports that over 10,000 North Korean troops are now deployed in Russia, including in the frontline Kursk region, to support the war in Ukraine.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

Security Affairs
NOVEMBER 10, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. CRON#TRAP: Emulated Linux Environments as the Latest Tactic in Malware Staging Typosquat Campaign Targeting npm Developers ToxicPanda: a new banking trojan from Asia hit Europe and LATAM Threat Campaign Spreads Winos4.
Let's personalize your content