Huge Microsoft Outage Linked to CrowdStrike Takes Down Computers Around the World
WIRED Threat Level
JULY 19, 2024
A software update from cybersecurity company CrowdStrike appears to have inadvertently disrupted IT systems globally.

WIRED Threat Level
JULY 19, 2024
A software update from cybersecurity company CrowdStrike appears to have inadvertently disrupted IT systems globally.
Security Affairs
JULY 19, 2024
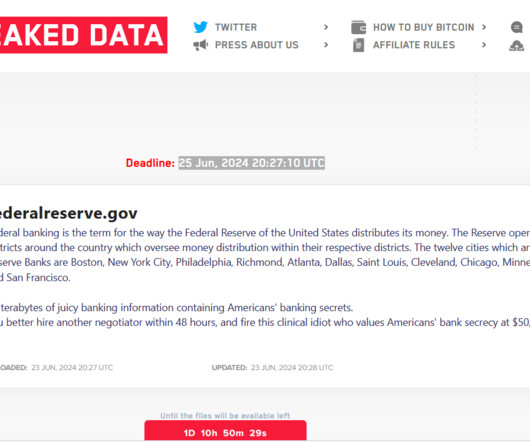
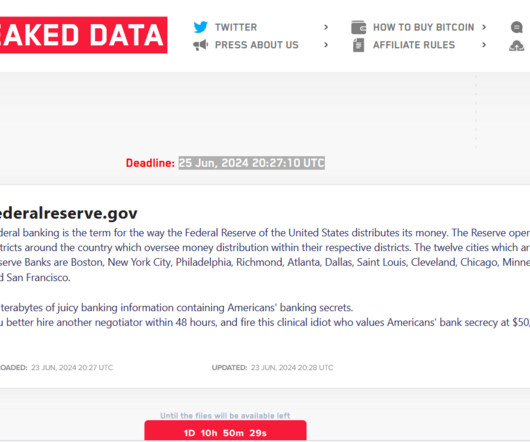
Two Russian nationals pleaded guilty to participating in the LockBit ransomware group and carrying out attacks against victims worldwide. Two foreign nationals, Ruslan Magomedovich Astamirov and Mikhail Vasiliev, pleaded guilty in Newark federal court for their roles in the LockBit ransomware operation. The LockBit ransomware operation has been active since January 2020, the group hit over 2,500 victims across 120 countries, including 1,800 in the U.S.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
JULY 19, 2024
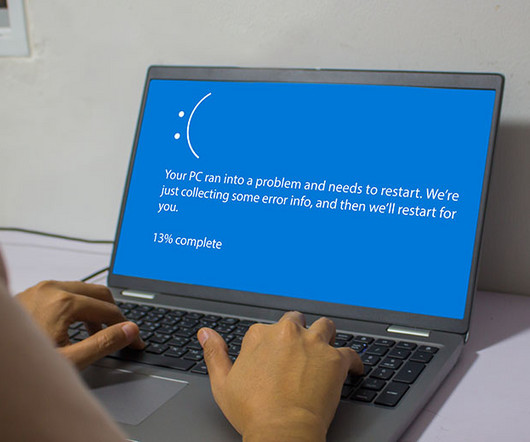
A defective CrowdStrike kernel driver sent computers around the globe into a reboot death spiral, taking down air travel, hospitals, banks, and more with it. Here’s how that’s possible.

Krebs on Security
JULY 19, 2024
A faulty software update from cybersecurity vendor Crowdstrike crippled countless Microsoft Windows computers across the globe today, disrupting everything from airline travel and financial institutions to hospitals and businesses online. Crowdstrike said a fix has been deployed, but experts say the recovery from this outage could take some time, as Crowdstrike’s solution needs to be applied manually on a per-machine basis.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Security Affairs
JULY 19, 2024
Personal and health information of 12.9 million individuals was exposed in a ransomware attack on Australian digital prescription services provider MediSecure. MediSecure is a company that provides digital health solutions, particularly focusing on secure electronic prescription delivery services in Australia. In May, the company was forced to shut down its website and phone lines following a cyber attack, but it did not mention a ransomware attack.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Security Affairs
JULY 19, 2024
Windows machines worldwide displayed BSoD screen following a faulty update pushed out by cybersecurity firm CrowdStrike. A faulty update released by CrowdStrike Falcon is causing Windows systems to display a BSoD screen. The incident is causing widespread global disruptions, impacting critical infrastructure such as airports, hospitals, and TV stations.

Weissman's World
JULY 19, 2024
I recently gave a presentation to ARMA International about the human consequences of what we do, and though you probably can get a copy of it from ARMA itself – and for sure you can from me – I wanted to take a minute to reinforce the criticality of my point. Most of us spend… Read More » Wanted! An IG Code of Human Ethics The post Wanted!

Security Affairs
JULY 19, 2024
Cisco has addressed a critical vulnerability that could allow attackers to add new root users to Security Email Gateway (SEG) appliances. Cisco fixed a critical vulnerability, tracked as CVE-2024-20401 (CVSS score 9.8), that could allow unauthenticated, remote attackers to add new users with root privileges and permanently crash Security Email Gateway (SEG) appliances.

Collaboration 2.0
JULY 19, 2024
It might seem like a total gimmick, but it's a must-have tool in my toolbox.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

Security Affairs
JULY 19, 2024
Windows machines worldwide displayed BSoD screen following a faulty update pushed out by cybersecurity firm CrowdStrike. A faulty update released by CrowdStrike Falcon is causing Windows systems to display a BSoD screen. The incident is causing widespread global disruptions, impacting critical infrastructure such as airports, hospitals, and TV stations.

Collaboration 2.0
JULY 19, 2024
The industrial-grade Topdon TC002 gives your iPhone a cool superpower and you can get it for much less than a dedicated thermal imaging camera.

Security Affairs
JULY 19, 2024
Personal and health information of 12.9 million individuals was exposed in a ransomware attack on Australian digital prescription services provider MediSecure. MediSecure is a company that provides digital health solutions, particularly focusing on secure electronic prescription delivery services in Australia. In May, the company was forced to shut down its website and phone lines following a cyber attack, but it did not mention a ransomware attack.

Collaboration 2.0
JULY 19, 2024
Just a week after the wearable's Unpacked launch, multiple customers reported issues with the earbud tips tearing - and Samsung has pulled the devices from shelves.

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!
Security Affairs
JULY 19, 2024
Two Russian nationals pleaded guilty to participating in the LockBit ransomware group and carrying out attacks against victims worldwide. Two foreign nationals, Ruslan Magomedovich Astamirov and Mikhail Vasiliev, pleaded guilty in Newark federal court for their roles in the LockBit ransomware operation. The LockBit ransomware operation has been active since January 2020, the group hit over 2,500 victims across 120 countries, including 1,800 in the U.S.

Collaboration 2.0
JULY 19, 2024
LG's Black Friday in July sale is happening now, and you can save up to $200 on LG speakers, earbuds, and more.

Security Affairs
JULY 19, 2024
Cisco has addressed a critical vulnerability that could allow attackers to add new root users to Security Email Gateway (SEG) appliances. Cisco fixed a critical vulnerability, tracked as CVE-2024-20401 (CVSS score 9.8), that could allow unauthenticated, remote attackers to add new users with root privileges and permanently crash Security Email Gateway (SEG) appliances.

Collaboration 2.0
JULY 19, 2024
The Auskang 5,000mAh power bank is only about as thick as a few credit cards, but it has enough power to reliably charge your smartphone or other USB-C device.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

WIRED Threat Level
JULY 19, 2024
Swindlers are spinning up bogus websites in an attempt to dupe people with “CrowdStrike support” scams following the security firm's catastrophic software update.

Collaboration 2.0
JULY 19, 2024
Are you looking for an Android 13 phone that offers thermal imaging, night vision, and won't break the bank?
Data Breach Today
JULY 19, 2024
In the Spotlight: Quality Assurance, Business Resilience, Single Points of Failure Expect the global IT disruptions caused by a bug in CrowdStrike's software to prompt quality assurance questions for the cybersecurity vendor. Experts say the incident also highlights shortcomings in the Windows operating system, as well as many organizations' business resiliency plans.

Collaboration 2.0
JULY 19, 2024
I've owned almost every version of the Galaxy Watch, but the Ultra is easily the one that I'll be wearing the longest.

Advertiser: ZoomInfo
Incorporating generative AI (gen AI) into your sales process can speed up your wins through improved efficiency, personalized customer interactions, and better informed decision- making. Gen AI is a game changer for busy salespeople and can reduce time-consuming tasks, such as customer research, note-taking, and writing emails, and provide insightful data analysis and recommendations.

Data Breach Today
JULY 19, 2024
Median Ransomware Attack Recovery Cost for Critical Infrastructure Is 4X Higher Ransomware remains a major threat to energy, oil/gas and utilities organizations of all sizes around the globe. Our 2024 state of ransomware report reveals that the median recovery costs for two critical infrastructure sectors - energy and water - quadrupled to $3 million over the past year.

Collaboration 2.0
JULY 19, 2024
The Bose QuietComfort Ultra headphones top every 'best headphones' list I've written, and for good reason. They're still on sale for $80 off following Amazon Prime Day 2024.

Data Breach Today
JULY 19, 2024
CrowdStrike Outage Rekindles Concerns Over Federal Cybersecurity Contingency Plans Federal agencies including CISA rushed on Friday to provide IT support to critical infrastructure sectors in the U.S. while resolving their own system disruptions caused by a faulty update pushed to Windows PCs by the Texas-based cybersecurity firm CrowdStrike.

Collaboration 2.0
JULY 19, 2024
The Oukitel C50 comes with a large 6.8-inch, 90Hz display with an ample amount of battery, proving again that cheap phones are getting good.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Data Breach Today
JULY 19, 2024
Some EHRs Affected; Hospitals Cancel Patient Care in Latest Vendor Mega Incident As if the healthcare sector doesn't have enough technology problems, the global IT outage caused by a faulty CrowdStrike software update has forced some hospitals and other medical facilities worldwide to resort to manual downtime procedures and cancel patient procedures.

Collaboration 2.0
JULY 19, 2024
A massive IT outage is causing trouble for millions of people around the world. If you're affected, there is a workaround.

Data Breach Today
JULY 19, 2024
Also: AI Bots in the Workplace; AI Regulations in the US and EU In the latest weekly update, ISMG editors discussed AT&T's alleged ransom payment to hackers following a breach of its Snowflake account, the challenges of using AI bots in the workplace, and the impact of differences in AI regulations in the E.U. and the U.S.
Let's personalize your content