Breach Roundup: How to Spot North Korean IT Workers
Data Breach Today
SEPTEMBER 26, 2024
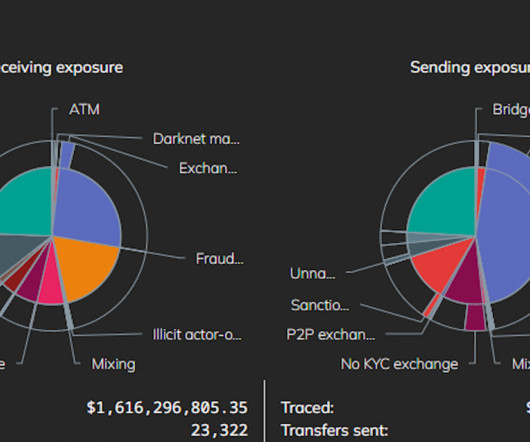
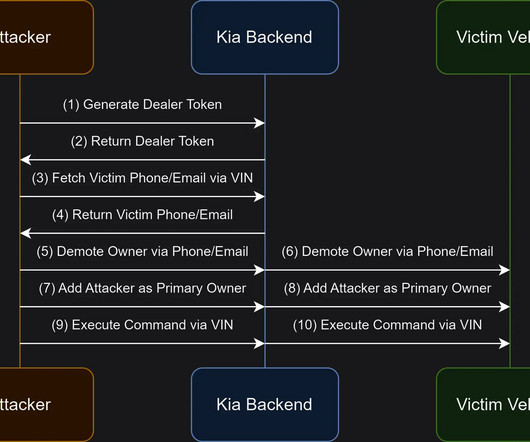
Also: Ransomware Surged in 2023, MoneyGram Back in Service After Cyberattack This week, advice on spotting North Korean staff; ransomware attacks rose; MoneyGram back online; FCC fined political operative; CISA warned of water system attacks; Ukraine restricted Telegram use; North Korean hackers used new malware; U.K. arrested alleged hacker; PSNI is in data leak talks.




































Let's personalize your content