Welcome to the Laser Wars
WIRED Threat Level
MAY 13, 2024
Amid a rising tide of adversary drones and missile attacks, laser weapons are finally poised to enter the battlefield.

WIRED Threat Level
MAY 13, 2024
Amid a rising tide of adversary drones and missile attacks, laser weapons are finally poised to enter the battlefield.
Security Affairs
MAY 13, 2024
A group of hackers that defines itself as “first-class Russian hackers” claims the defacement of hundreds of local and regional British newspaper websites. A group claiming to be “first-class Russian hackers” defaced numerous local and regional British newspaper websites owned by Newsquest Media Group. The group defaced the home pages of the targeted websites and posted the message “PERVOKLASSNIY RUSSIAN HACKERS ATTACK.” The following image shows an archived version of t
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
MAY 13, 2024
NYC mayor Eric Adams wants to test Evolv’s gun-detection tech in subway stations—despite the company saying it’s not designed for that environment. Emails obtained by WIRED show how the company still found an in.

Security Affairs
MAY 13, 2024
Apple rolled out urgent security updates to address code execution vulnerabilities in iPhones, iPads, and macOS. Apple released urgent security updates to address multiple vulnerabilities in iPhones, iPads, macOS. The company also warns of a vulnerability patched in March that the company believes may have been exploited as a zero-day. The issue impacts older iPhone devices, it is tracked as CVE-2024-23296 and is a memory corruption flaw in the RTKit.

Speaker: Frank Taliano
Document-heavy workflows slow down productivity, bury institutional knowledge, and drain resources. But with the right AI implementation, these inefficiencies become opportunities for transformation. So how do you identify where to start and how to succeed? Learn how to develop a clear, practical roadmap for leveraging AI to streamline processes, automate knowledge work, and unlock real operational gains.

WIRED Threat Level
MAY 13, 2024
Tuesday’s verdict in the trial of Alexey Pertsev, a creator of crypto-privacy service Tornado Cash, is the first in a string of cases that could make it much harder to skirt financial surveillance.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Krebs on Security
MAY 13, 2024
Last week, the United States joined the U.K. and Australia in sanctioning and charging a Russian man named Dmitry Yuryevich Khoroshev as the leader of the infamous LockBit ransomware group. LockBit’s leader “ LockBitSupp ” claims the feds named the wrong guy, saying the charges don’t explain how they connected him to Khoroshev.
Security Affairs
MAY 13, 2024
Firstmac Limited disclosed a data breach after the new Embargo extortion group leaked over 500GB of data allegedly stolen from the company. Firstmac Limited, one of the largest non-bank lenders in Australia, disclosed a data breach. Firstmac Limited is an Australian owned company with experience in home and investment loans. They have a range of market insurance products backed by international company, Allianz Group.

The Last Watchdog
MAY 13, 2024
KINGSTON, Wash. — U.S. Secretary of State Antony Blinken opened RSA Conference 2024 last week issuing a clarion call for the cybersecurity community to defend national security, nurture economic prosperity and reinforce democratic values. Related: The power of everyman conversing with AI Blinken That’s a tall order. My big takeaway from RSAC 2024 is this: the advanced technology and best practices know-how needed to accomplish the high ideals Secretary Blinken laid out are readily at hand

Collaboration 2.0
MAY 13, 2024
We tested the best travel VPNs that offer solid security and fast connections while you're on the road, working remotely, or vacationing.

Advertiser: ZoomInfo
AI adoption is reshaping sales and marketing. But is it delivering real results? We surveyed 1,000+ GTM professionals to find out. The data is clear: AI users report 47% higher productivity and an average of 12 hours saved per week. But leaders say mainstream AI tools still fall short on accuracy and business impact. Download the full report today to see how AI is being used — and where go-to-market professionals think there are gaps and opportunities.

Data Breach Today
MAY 13, 2024
Ex-DHS Official Suzanne Spaulding and Jim Richberg of Fortinet on Critical Concepts The concept of "responsible radical transparency" plays a critical role in efforts to improve the state of cybersecurity, said Suzanne Spaulding, former undersecretary, Department of Homeland Security, and Jim Richberg, head of global policy and field CISO, Fortinet, who explain why.
The Last Watchdog
MAY 13, 2024
Torrance, Calif., May 13, 2024, CyberNewsWire — Criminal IP, a renowned Cyber Threat Intelligence (CTI) search engine developed by AI SPERA, has recently signed a technology partnership to exchange threat intelligence data based on domains and potentially on the IP address to protect users by blocking threats to end users. Criminal IP underwent rigorous data evaluation to integrate with Quad9’s threat-blocking service, demonstrating high data uniqueness and accuracy.

Data Breach Today
MAY 13, 2024
Federal Database Nears 10,000 Unanalyzed Vulnerabilities Amid Halt in Operations The National Vulnerability Database is currently suffering from a backlog of nearly 10,000 unanalyzed common vulnerabilities and exposures amid an apparent halt in data enrichment operations and a growing debate over who should be in charge of overseeing the massive security risk library.

Schneier on Security
MAY 13, 2024
Back in the 1960s, if you played a 2,600Hz tone into an AT&T pay phone, you could make calls without paying. A phone hacker named John Draper noticed that the plastic whistle that came free in a box of Captain Crunch cereal worked to make the right sound. That became his hacker name, and everyone who knew the trick made free pay-phone calls. There were all sorts of related hacks, such as faking the tones that signaled coins dropping into a pay phone and faking tones used by repair equipment.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

Data Breach Today
MAY 13, 2024
Visa's Subra Kumaraswamy on Threat Detection, AI and Third-Party Supply Chain Risk Subra Kumaraswamy, senior vice president and CISO at Visa, discusses how organizations can bolster cyber resilience by using strategic deployment of AI to enhance threat detection capabilities, fortify supply chain risk management and address talent shortages.

KnowBe4
MAY 13, 2024
"Reality Hijacked" isn't just a title—it's a wake-up call. The advent and acceleration of GenAI is redefining our relationship with 'reality' and challenging our grip on the truth.

Data Breach Today
MAY 13, 2024
Advisories Come As Black Basta Appears Responsible for Ascension Ransomware Attack U.S. federal authorities warn that the Russian-speaking ransomware group Black Basta is actively targeting American critical infrastructure amid reports that it's behind the ransomware attack on hospital chain Ascension. The hospital chain is still operating under downtime procedures.

The Last Watchdog
MAY 13, 2024
London, United Kingdom, May 13, 2024, CyberNewsWire — Logicalis, the global technology service provider delivering next-generation digital managed services, has today announced the launch of Intelligent Security, a blueprint approach to its global security portfolio designed to deliver proactive advanced security for customers worldwide. Intelligent Security has been designed by Logicalis’ worldwide team of security specialists to give customers the most comprehensive observability a

Advertiser: ZoomInfo
ZoomInfo customers aren’t just selling — they’re winning. Revenue teams using our Go-To-Market Intelligence platform grew pipeline by 32%, increased deal sizes by 40%, and booked 55% more meetings. Download this report to see what 11,000+ customers say about our Go-To-Market Intelligence platform and how it impacts their bottom line. The data speaks for itself!

Data Breach Today
MAY 13, 2024
Modules Widely Deployed in Manufacturing, Telecommunications and Healthcare Devices Multiple types of Telit Cinterion cellular modules for IoT and machine-to-machine devices, which are widely used across industrial, financial services, telecommunications and healthcare environments, are vulnerable to being remotely compromised via malicious SMS messages, security researchers warn.

IBM Big Data Hub
MAY 13, 2024
Artificial intelligence (AI) represents a once-in-a-lifetime change management opportunity that might decide who wins and losses across every industry. As the AI era takes shape through digital transformation initiatives, executives and employees alike are contemplating how it affects employment and the skills needed to stay ahead. This is where AI upskilling and reskilling come into play.

Data Breach Today
MAY 13, 2024
White House Announces High-Level Talks With Beijing on Advanced AI Systems Senior White House officials will hold a series of high-level conversations with Chinese counterparts on the security and risks associated with advanced artificial intelligence systems, U.S. officials told reporters, amid growing tensions and a historic low point in U.S.-China relations.

IG Guru
MAY 13, 2024
Check out the article here. The post NIST publishes new guides on AI risk for developers and CISOs via CSO Online first appeared on IG GURU.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

IBM Big Data Hub
MAY 13, 2024
This blog series demystifies enterprise generative AI (gen AI) for business and technology leaders. It provides simple frameworks and guiding principles for your transformative artificial intelligence (AI) journey. In the previous blog , we discussed the differentiated approach by IBM to delivering enterprise-grade models. In this blog, we delve into why foundation model choices matter and how they empower businesses to scale gen AI with confidence.

eSecurity Planet
MAY 13, 2024
Big vendor vulnerabilities from F5, Citrix, and Chrome will lead the headlines with highly dangerous vulnerabilities in popular products. However, the most dangerous vulnerabilities might be the lesser known Tinyproxy and Cinterion Cellular Modem flaws. Small business owners tend to adopt Tinyproxy and also tend to use part-time IT resources which potentially threatens related supply chains with third-party risk.

CILIP
MAY 13, 2024
Innovative approaches to literacy: Libraries Change Lives Librarians from across the country have been submitting their stories of impact to share with MPs and political leaders as part of the Libraries Change Lives Campaign. The Games Library initiative by Westminster City Council and the Royal Borough of Kensington and Chelsea (RBKC), has made a positive impact on literacy, language development and communication skills for young people.
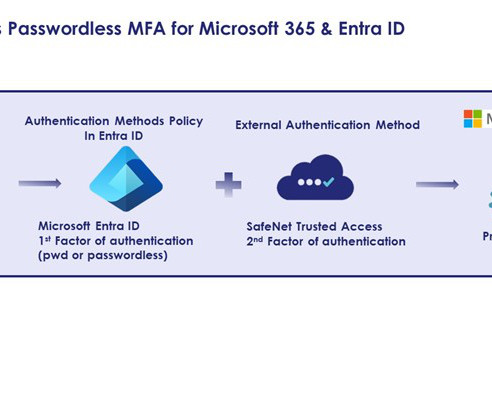
Thales Cloud Protection & Licensing
MAY 13, 2024
Unlocking the Cloud: Microsoft and Thales Spearhead Passwordless & MFA for Organizations moving to Microsoft 365. madhav Tue, 05/14/2024 - 05:47 Thales and Microsoft: a long partnership in Identity Security Thales and Microsoft recently celebrated their long-term partnership at the Microsoft Security Excellence Award Ceremony during RSA Conference 2024, as Thales won the Identity Trailblazer Award.

Speaker: Yohan Lobo and Dennis Street
In the accounting world, staying ahead means embracing the tools that allow you to work smarter, not harder. Outdated processes and disconnected systems can hold your organization back, but the right technologies can help you streamline operations, boost productivity, and improve client delivery. Dive into the strategies and innovations transforming accounting practices.

HID Global
MAY 13, 2024
HID announces its strategic partnership and integration with Q2 Holdings. Together, they will redefine the banking authentication experience.

CGI
MAY 13, 2024
How to scale AI’s impact and accelerate outcomes Cutting through the noise around AI: Where do we really stand? My conversations with industry executives about AI largely fall into two camps—those who see AI as uniquely transformative, and those who view it as a powerful and disruptive tool, but at the core still a technology that will follow the same patterns they’ve seen before.

Adapture
MAY 13, 2024
Adapture’s Laura Burdine and Mary Folsom Showcased among Channel Leaders ATLANTA, May 13, 2024 – Adapture is pleased to announce that CRN ® , a brand of The Channel Company , has recognized Laura Burdine, Director of Sales Operations, and Mary Folsom, Manager of Channel Marketing and Demand Generation, on its 2024 Women of the Channel List. Every year, CRN highlights women from vendor, distributor and solution provider organizations whose vision and leadership have a beneficial influence on the
Let's personalize your content