New Leak Shows Business Side of China’s APT Menace
Krebs on Security
FEBRUARY 22, 2024
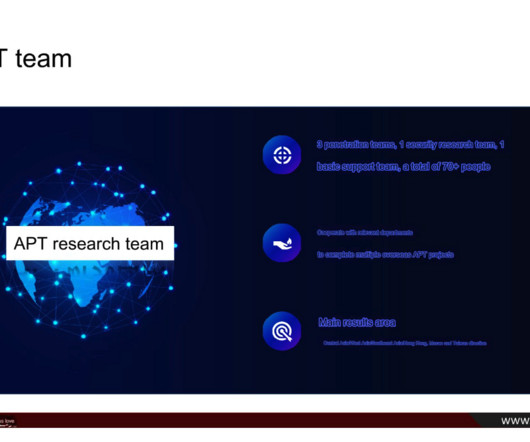
A new data leak that appears to have come from one of China’s top private cybersecurity firms provides a rare glimpse into the commercial side of China’s many state-sponsored hacking groups. Experts say the leak illustrates how Chinese government agencies increasingly are contracting out foreign espionage campaigns to the nation’s burgeoning and highly competitive cybersecurity industry.





































Let's personalize your content