Recent ‘MFA Bombing’ Attacks Targeting Apple Users
Krebs on Security
MARCH 26, 2024
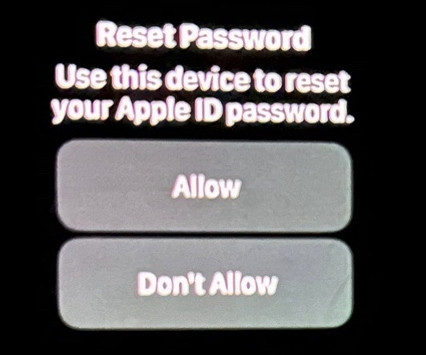
Several Apple customers recently reported being targeted in elaborate phishing attacks that involve what appears to be a bug in Apple’s password reset feature. In this scenario, a target’s Apple devices are forced to display dozens of system-level prompts that prevent the devices from being used until the recipient responds “Allow” or “Don’t Allow” to each prompt.







































Let's personalize your content