Ransomware: A Deep Dive into 2021 Emerging Cyber-Risks
Threatpost
APRIL 19, 2021
Our new eBook goes beyond the status quo to take a look at the evolution of ransomware and what to prepare for next.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Threatpost
APRIL 19, 2021
Our new eBook goes beyond the status quo to take a look at the evolution of ransomware and what to prepare for next.

AIIM
JULY 8, 2021
Don’t, however, lose sight of the fact that information scattered across a dispersed workforce can significantly raise the risk of a data breach or other security concerns. At Gimmal, we regularly talk to IT, security, and privacy professionals across a broad portfolio of industries. Applying retention rules (i.e.,
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

KnowBe4
JUNE 9, 2022
In KnowBe4’s new Password Policy ebook, What Your Password Policy Should Be , we recommend that all users use a password manager to create and use perfectly random passwords. A perfectly random 12-character or longer password is impervious to all known password guessing and cracking attacks.

The Last Watchdog
OCTOBER 3, 2019
By signing up for Peerlyst, company decision makers focused on mitigating cyber risks, as well as vendor experts, academics and independent researchers, are provided with a personalized feed of content based on specific interests, as well as the topics and people you follow. Talk more soon.

Advertisement
Many application teams leave embedded analytics to languish until something—an unhappy customer, plummeting revenue, a spike in customer churn—demands change. But by then, it may be too late. In this White Paper, Logi Analytics has identified 5 tell-tale signs your project is moving from “nice to have” to “needed yesterday.".

AIIM
JANUARY 9, 2019
This day, led officially by The National Cyber Security Alliance (NCSA) , is an international effort to “create awareness about the importance of respecting privacy, safeguarding data, and enabling trust”. eBook: Get an executive guide to managing your information risk: Bridging the Gap Between Security Awareness and Action.

AIIM
DECEMBER 19, 2018
In a digital world, Information-related risk runs throughout most organizations. Information security is at the list of concerns (80% are “concerned” or “extremely concerned”). Information security is at the list of concerns (80% are “concerned” or “extremely concerned”).

AIIM
JANUARY 26, 2018
A new set of European rules and standards related to privacy and data protection (the General Data Protection Regulation , or GDPR ) has set in motion a mad compliance and security scramble not only for European companies, but also for any company doing business in Europe or with European customers. 4 -- Information archiving and retention.

Thales Cloud Protection & Licensing
SEPTEMBER 10, 2019
Secure and successful management of data access may still be an Achilles’ heel for many organizations, but if there’s a silver lining to cloud breaches, it’s that they highlight where changes need to be made. Investments in IT security are on the rise and policies are evolving for the better. Important Changes Are Happening.

Advertisement
Just by embedding analytics, application owners can charge 24% more for their product. How much value could you add? This framework explains how application enhancements can extend your product offerings. Brought to you by Logi Analytics.
Thales Cloud Protection & Licensing
JANUARY 16, 2025
Some of the most important are Gramm-Leach-Bliley Act ( GLBA ), the National Association of Insurance Commissioners ( NAIC ) Data Security Model Law, the New York Department of Financial Services ( NYDFS ) Cybersecurity Regulation, and the National Credit Union Administration ( NCUA ) cybersecurity guidance.

Collibra
JULY 6, 2022
Get the ebook. Reduce data and compliance risks. Our newest ebook explores each of these valuable pillars of our adaptive data and analytics governance solution — and presents two Collibra case studies from global leaders in technology and security. > See how adaptive data and analytics governance can help.

AIIM
NOVEMBER 16, 2017
You might also be interested in: Mitigate Data Privacy and Security Risks with Machine Learning. The Privacy and Security Dichotomy. Using semantic analysis techniques personally identifiable information can be uncovered, tagged and processed in compliance with GDPR thereby mitigate risk while improve organizational efficiency.

AIIM
JUNE 26, 2018
Want to learn more about GDPR and overall Information Security? Get this FREE ebook, Information Privacy and Security. About the author: Andrew Pery is a marketing executive with over 25 years of experience in the high technology sector focusing on content management and business process automation.

The Security Ledger
SEPTEMBER 11, 2019
Third party cyber risk is growing. In this Spotlight Podcast, a companion to our new eBook, Rethinking Third Party Cyber Risk Management, we go deep on the topic of building a mature third party cyber risk program with Dave Stapleton the Director of Assessment. » Related Stories Third Party Cyber Risk is growing.

Thales Cloud Protection & Licensing
MAY 6, 2021
To Achieve Zero Trust Security, Trust The Human Element. With more employees working remotely than ever before due to COVID-19, businesses are at greater risk from a cyber-attack with workers accessing systems outside of the usual company network. Angus Macrae, Head of Cyber Security. Thu, 05/06/2021 - 08:41.

AIIM
MARCH 30, 2018
In order to take protective measures, you must read – and I know everyone reads every word of every agreement – before you agree to the terms and use the security features available within those apps to minimize the potential risk. For more information about security, check out this FREE eBook.

Thales Cloud Protection & Licensing
FEBRUARY 1, 2024
They're error-prone, an unstable link in the security chain, a high-friction element in user journeys, and an outdated authentication method unsuitable for today's landscape. FIDO is an overarching framework for secure and passwordless authentication. But while passwords have served their purpose, they have outlived their usefulness.

AIIM
NOVEMBER 2, 2017
Organizations that fail to comply with GDPR risk potentially massive penalties. The more automation you can achieve in the classification process, the less risk your organization may face due to improper data management. Without an easy path to compliance, the risk will always be too great. is no longer sufficient.

Collibra
FEBRUARY 21, 2024
To achieve data cloud migration success, we recommend a 4-step process that we explore in our helpful ebook: Four steps to successfully power your data cloud migration with data intelligence. Moving to the cloud requires changes in how teams operate, how decisions are made, and how risks are managed.

IT Governance
APRIL 16, 2018
This week’s extract is taken from Graham Day’s book Security in the Digital World. This must-have guide features simple explanations, examples and advice to help you become security-aware in a developing digital world. The impressive security functions of iPhones tend to be overlooked, or not fully understood by users.

Thales Cloud Protection & Licensing
APRIL 25, 2022
A survey of 230 healthcare security leaders in China, Germany, Japan, the UK, and the US found that a whopping 82% of their healthcare organizations had experienced an IoT-focused cyberattack. The risks of non-compliance. Data security. It is estimated the cost of US healthcare ransomware attacks alone at $21 billion in 2020.

Thales Cloud Protection & Licensing
NOVEMBER 22, 2021
Consumers have come to expect a hyper-personalized experience that is fast, convenient and secure. Banks have adopted technologies to enable: Secure, remote, multi-device banking transactions. Secure digital payments leveraging biometrics, tokens, and context-based security. Reducing risk and complexity.

Thales Cloud Protection & Licensing
MAY 31, 2023
The European Commission enacted the Digital Operational Resilience Act (DORA), while in Singapore, the Monetary Authority published an advisory for addressing technology and cyber risks. REs must implement an enterprise-wide governance and risk management strategy for cloud computing. REs must fully control and possess all their data.

Thales Cloud Protection & Licensing
MARCH 29, 2018
As the volume of both card-based payments and digital payments continue to grow significantly year-on-year, the importance of securing sensitive card data (and in particular the primary account number or PAN) has never been a more critical and challenging task. Different tokenization solutions to protect against different risks.

Thales Cloud Protection & Licensing
MARCH 5, 2025
Preparing for Hong Kongs Protection of Critical Infrastructures (Computer Systems) Bill madhav Thu, 03/06/2025 - 04:45 Critical infrastructure includes all the assets, systems, facilities, and networks that are essential to the proper functioning of a societys economy, national public health or safety, security.

Thales Cloud Protection & Licensing
FEBRUARY 28, 2022
More data in more places means more risks. This honeypot of information puts manufacturers at major risk from cyber attacks. Accelerate digital transformation by reducing risk, complexity, and cost. Learn more about Thales Solutions for connected car protection and automotive data security. Data security.

Thales Cloud Protection & Licensing
APRIL 29, 2024
Comprehensive cybersecurity legislation is imperative to build and maintain confidence in the future and ensure a secure digital landscape. When enforced, the regulation will mandate manufacturers to prioritize security from the design stage and throughout the product's entire lifecycle.

Adam Shostack
JANUARY 2, 2025
[no description provided] At RSA'17, I spoke on " Security Leadership Lessons from the Dark Side." Leading a security program is hard. Fortunately, we can learn a great deal from Sith lords, including Darth Vader and how he managed security strategy for the Empire. Better ways you will learn, mmmm?

Thales Cloud Protection & Licensing
JUNE 4, 2019
In addition, the evolution of technology will certainly challenge even the best-prepared organizations and hugely increase their cyber risk. For more information on how to achieve and maintain compliance, read Data Security Compliance and Regulations eBook.

eDiscovery Daily
DECEMBER 14, 2021
Learn about four other ways your organization can build value and boost margins in our ebook here. Secured cloud environments allowed for a more efficient and effective workflow to collect, process, host, review and produce critical data. . How Secure is Remote eDiscovery? Secured connectivity must be ensured for all employees

Thales Cloud Protection & Licensing
FEBRUARY 1, 2023
Indonesia PDP Law & Data-Centric Security ApproachA data-centric security approach is integral to virtually every worldwide data compliance regulation and standard and is a foundational best practice. The defining characteristic of data-centric security is that protection is applied to the data, independent of the data’s location.

The Security Ledger
SEPTEMBER 10, 2019
Third party cyber risk is a growing concern for organizations, as breaches and hacks tied to third party providers and applications multiply. How do you know if your third party cyber risk management program is up to the task? Our new e-book, sponsored by CyberGRX, will help you figure it out! We Talk about Why.

Thales Cloud Protection & Licensing
APRIL 21, 2021
But behind the scenes, this emergence of often untrusted devices (BYOD) and an increased adoption of unsanctioned applications (a trend called “Shadow IT”) has led to security nightmares for IT departments. The path to a Zero Trust posture is not linear, and the tall claims by security vendors often cloud the decision-making.

Thales Cloud Protection & Licensing
MARCH 21, 2022
Digital sovereignty has raised questions for CIOs considering their cloud strategy, governance, and risk management. Automated risk assessment and centralized protection. Data security. Around the world, even between EU member states, digital sovereignty is becoming more important. What is the impact of digital sovereignty?

Thales Cloud Protection & Licensing
MAY 26, 2022
Last week, I had the opportunity to attend the Google Cloud Security Summit digital event and share how Thales and Google are working together to accelerate cloud migration safely and efficiently. Cloud Security. What is Digital Sovereignty and Why is it Important in a Cloud Environment? Thu, 05/26/2022 - 09:54. Cloud Computing.

Thales Cloud Protection & Licensing
JANUARY 16, 2020
Based on the core principle that “the right to privacy is a fundamental right,” the objectives of the Bill are to “ensure growth of the digital economy while keeping personal data of citizens secure and protected,” and “to create a collective culture that fosters a free and fair digital economy.”. Enhance data security measures.

eDiscovery Daily
DECEMBER 1, 2021
When handling these confidential documents, it is important to keep these documents safe and secure. . To ensure the quality of your eDiscovery data , you need to adopt a proven data collection solution that can operate efficiently, securely, and in a forensically sound manner. It also needs to be able to: Work with modern data types.
Thales Cloud Protection & Licensing
SEPTEMBER 13, 2022
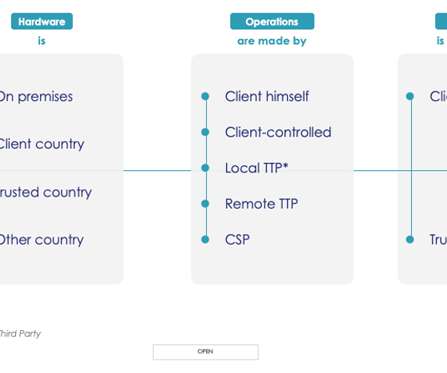
According to the global edition of Thales’s 2022 Cloud Security Study : The shift to modern, multicloud infrastructure is in full swing, and organizations have to build security capabilities that will support it. See our eBook “ Achieve Digital Sovereignty with Thales for more on this.”.

Adapture
JULY 30, 2021
This was supposed to minimize the risk of an account takeover (ATO) and, more importantly, a full-blown data breach. The Open Web Application Security Project® (OWASP) defines credential stuffing as a subset of brute force attacks. Any security analyst or IT admin with a trained eye can easily spot a brute force attempt.

Info Source
FEBRUARY 2, 2018
The risks of being found non-compliant regarding an individual’s rights are considerable. Download the eBook now. Specifically, the eBook outlines how YSoft SafeQ 6 print management solution helps your organization comply with GDPR in these key areas. 1. Keeping your personal data processing secure.

KnowBe4
OCTOBER 7, 2018
This presents a monumental risk to companies, worldwide, as they look to attract and retain these key professionals who keep their companies and general public safe from cybercriminals. A Year in the Life of A Security Awareness Program Manager on-demand webinar. Industry analysts predict that by 2020 there will be estimated to be 1.8

Thales Cloud Protection & Licensing
MARCH 31, 2021
Organizations are facing challenging times when it comes to securing their corporate assets, systems, networks and data. Trust is now a risk. For Zero Trust security, the solution to the trust crisis problem is to “never trust, always verify”. Michael Ball, Virtual Chief Information Security Officer, TeamCISO.

Thales Cloud Protection & Licensing
JULY 19, 2018
Recently the Payment Card Industry Security Standards Council (PCI SSC) announced a minor update to the PCI DSS standard largely to make it easier to read with respect to key dates that are now in the past. Advice on how to comply with PCI DSS can be found in our recent eBook, “ PCI Compliance and Data Protection for Dummies ”.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content