GUEST ESSAY: The case for network defenders to focus on leading — not lagging — indicators
The Last Watchdog
JANUARY 17, 2022
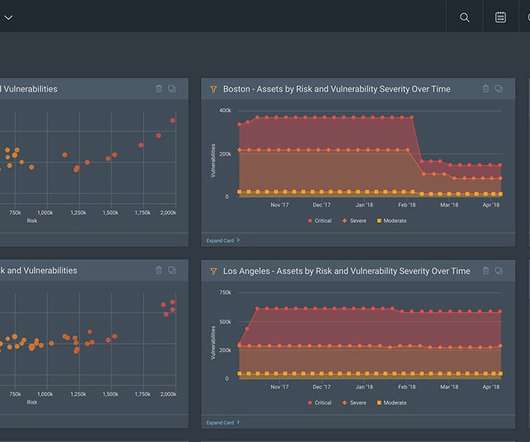
Lagging indicators are separate from leading indicators that could include marketing leads, pipeline generation and demos. One solution for secure software development is tracking security requirements and controls. Accountability for software security often falls under the Chief Information Security Officer (CISO).















































Let's personalize your content