What is BEC? Business email compromise definition and prevention
IT Governance
NOVEMBER 4, 2021
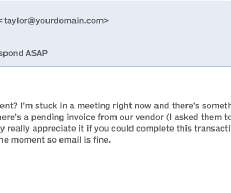
BEC scams often use the pretext that the executive is in a meeting or otherwise indisposed, which is why they are emailing you rather than calling. To prevent BEC scams, you therefore need to educate employees on their vulnerabilities and help them spot the signs of scam emails. Next, they will ask you to provide something urgently.















































Let's personalize your content