APT36 Running Espionage Ops Against India's Education Sector
Data Breach Today
APRIL 14, 2023
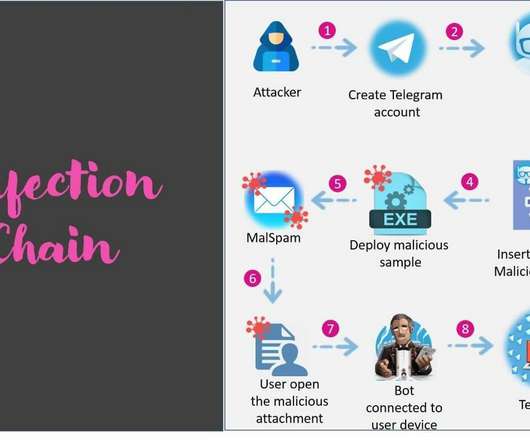
Pakistan-Linked APT Group Using Spear-Phishing to Plant Info Stealer Malware A suspected Pakistan espionage threat actor that relies on phishing emails is expanding to the education sector after years of focusing on the Indian military and government.








































Let's personalize your content