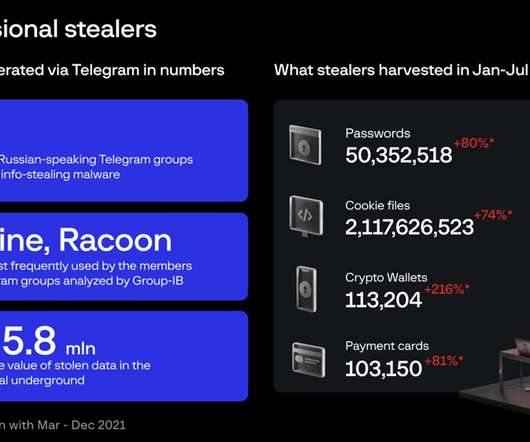
2.9 Billion Records Exposed in NPD Breach: How to Stay Safe
eSecurity Planet
AUGUST 20, 2024
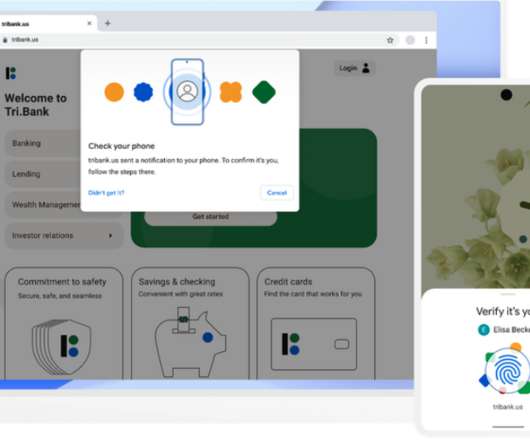
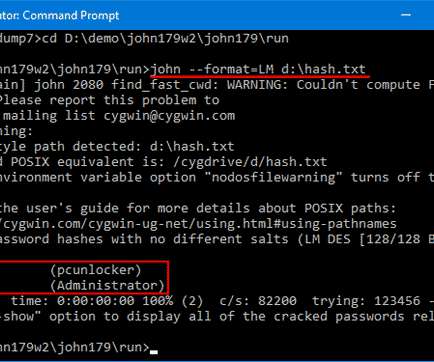
How to Protect Yourself From Data Breaches? Use Strong, Unique Passwords Weak passwords are easy for hackers to guess or crack, especially if they’re common or reused across multiple sites. When creating passwords, use at least 12 characters, combining uppercase and lowercase letters, numbers, and special symbols.










































Let's personalize your content