Kali Linux Penetration Testing Tutorial: Step-By-Step Process
eSecurity Planet
APRIL 7, 2023
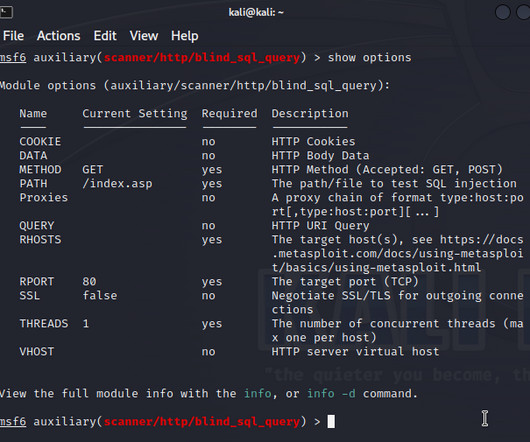
Kali Linux turns 10 this year, and to celebrate, the Linux penetration testing distribution has added defensive security tools to its arsenal of open-source security tools. For now, Kali is primarily known for its roughly 600 open source pentesting tools, allowing pentesters to easily install a full range of offensive security tools.

















Let's personalize your content