NEW TECH: DigiCert Document Signing Manager leverages PKI to advance electronic signatures
The Last Watchdog
JULY 21, 2021
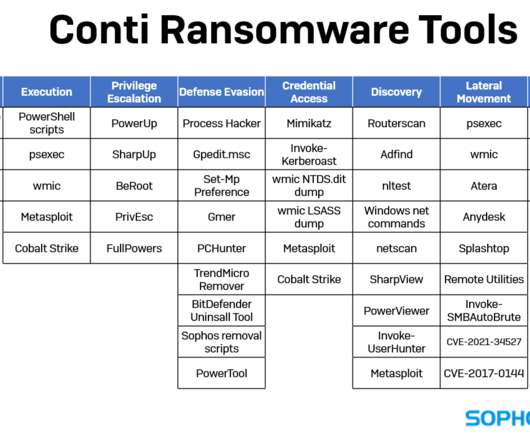
Most of us, by now, take electronic signatures for granted. Related: Why PKI will endure as the Internet’s secure core. Yet electronic signatures do have their security limitations. Trzupek outlined how DSM allows for legally-binding documents with auditability and management of signers. “It






































Let's personalize your content