Security Ledger Podcast: Security Automation Is (And Isn't) The Future Of InfoSec
ForAllSecure
OCTOBER 9, 2019
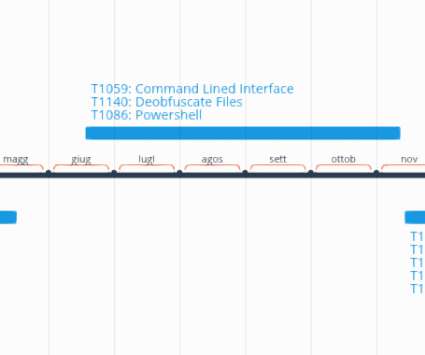
Advances in the use of polymers revolutionized everything from food packaging to electronics, telecommunication and medicine. But how exactly will artificial intelligence help bridge the information security skills gap? They won with Mayhem, an assisted intelligence application security testing solution.













Let's personalize your content