Cyber Threats Observatory Gets Improvements
Security Affairs
MAY 3, 2020
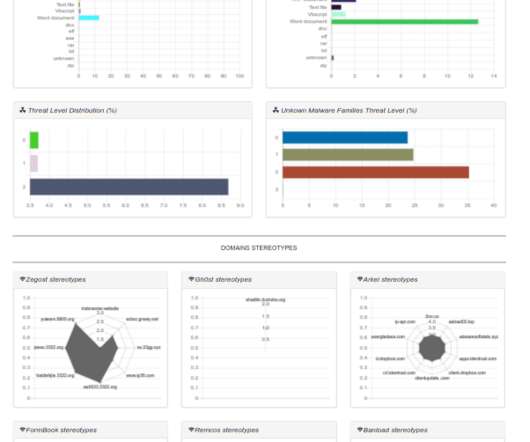
Based on the magic file bytes this graph would track the percentages of file types that Malware used as carrier. In other words, it could be nice to see what are the patterns used by malware in both: domain names, file names and process names. TOP domains, TOP processes and TOP File Names.















Let's personalize your content