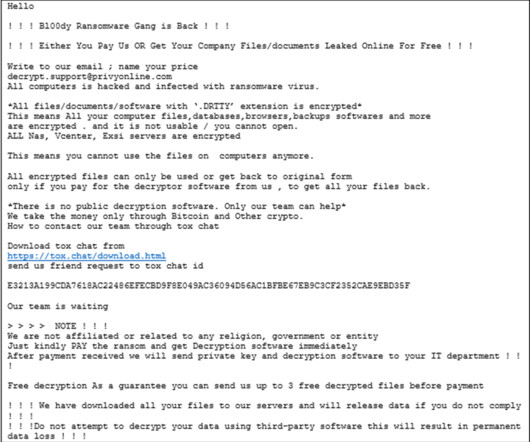
Bl00dy Ransomware Gang actively targets the education sector exploiting PaperCut RCE
Security Affairs
MAY 12, 2023
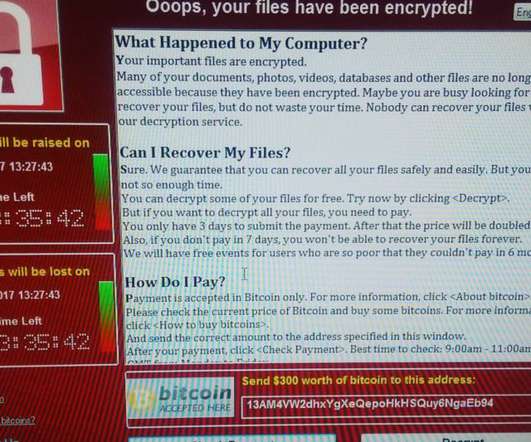
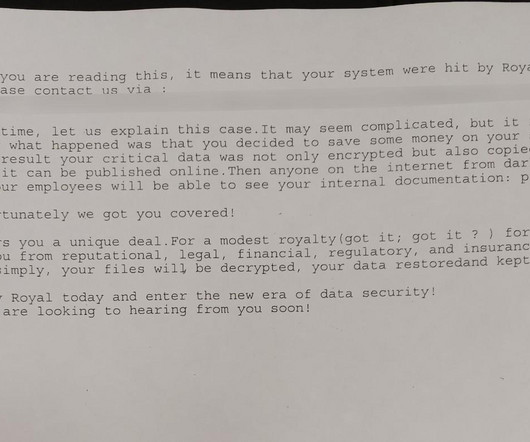
CISA and FBI warned of attacks conducted by the Bl00dy Ransomware Gang against the education sector in the country. The FBI and CISA issued a joint advisory warning that the Bl00dy Ransomware group is actively targeting the education sector by exploiting the PaperCut remote-code execution vulnerability CVE-2023-27350.




































Let's personalize your content