State of the Global Intelligent Document Processing Market 2023/2024
Info Source
SEPTEMBER 26, 2024
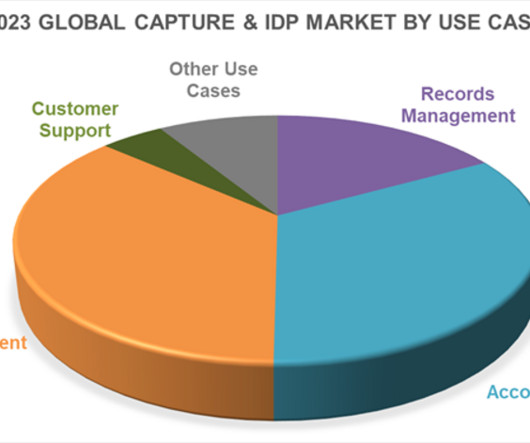
In our assessment of use cases, we expect the demand for these solutions to grow over proportionally in the next 5 years as GenAI technologies enable advanced automation capabilities and integrated customer communication features. These solutions are increasingly utilized in end-to-end automation of business processes.

























Let's personalize your content