Experts spotted first-ever crypto mining campaign leveraging Kubernetes RBAC
Security Affairs
APRIL 23, 2023
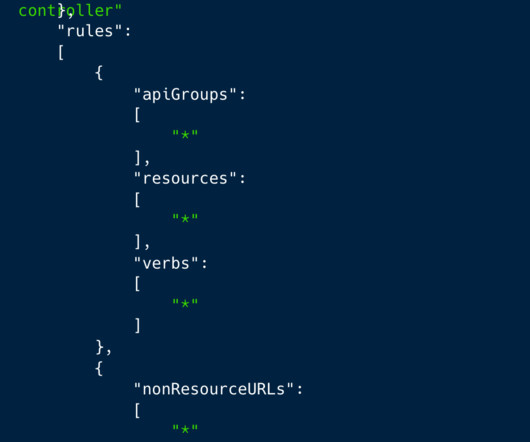
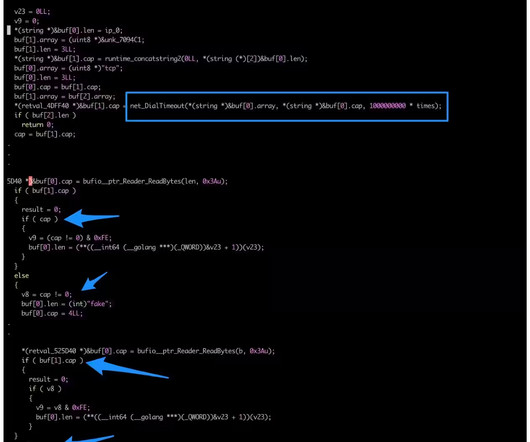
Experts warn of a large-scale cryptocurrency mining campaign exploiting Kubernetes (K8s) Role-Based Access Control ( RBAC ). Cloud security firm Aqua discovered a large-scale cryptocurrency mining campaign exploiting Kubernetes (K8s) Role-Based Access Control ( RBAC ) to create backdoors and run miners.



























Let's personalize your content